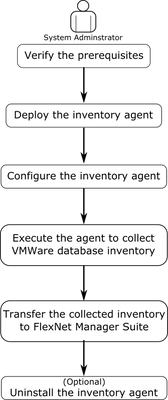
VMware stand-alone inventory agent for FlexNet Manager Suite
Discovery and inventory information are necessary for FlexNet Manager Suite to perform license consumption calculations. For collecting inventory, we recommend that you deploy one or more inventory beacons on your network and use supported inventory ...