Unable to Search for Catalog Items after Upgrading to 2023 R2
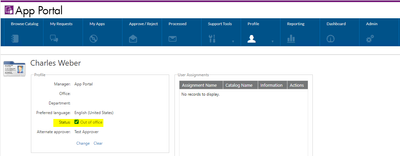
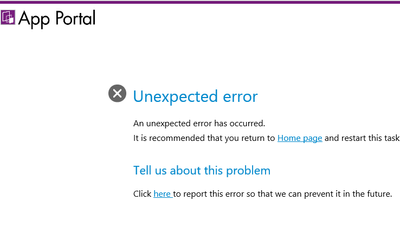
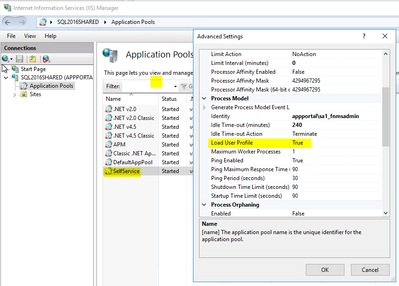
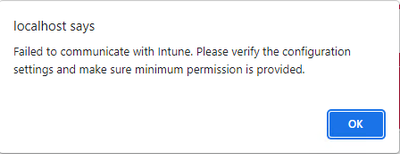
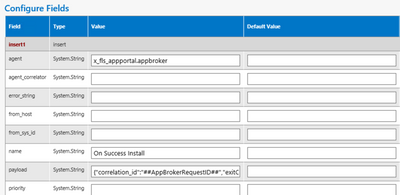
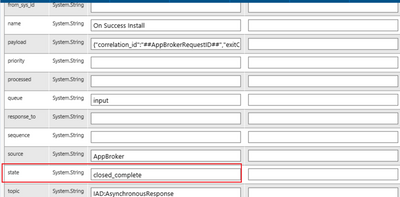
Summary Unable to Search for Catalog Items after Upgrading to 2023 R2. Symptoms Searching for a catalog item under Browse Catalog yields no results.. This behavior started after the upgrade to 2023 R2. Fix Version and Resolution In 2023 R2, new Advan...