A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Data Platform
- :
- Data Platform Release Blog
- :
- Data Platform mitigation for Apache Log4j 1.2 vulnerability CVE-2021-4104
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
A vulnerability has been publicly disclosed in Apache Log4j 1.2. The vulnerability has been assigned the identifier CVE-2021-4104 with a CVSS score of “High”.
All versions of Data Platform include Log4j 1.2 components, and thus are potentially exposed to this vulnerability. This article describes the potential impact of the vulnerability on Data Platform and options for mitigation.
Vulnerability description
The National Vulnerability Database describes the CVE-2021-4104 vulnerability at https://nvd.nist.gov/vuln/detail/CVE-2021-4104 as follows (current as of Dec 30, 2021):
JMSAppender in Log4j 1.2 is vulnerable to deserialization of untrusted data when the attacker has write access to the Log4j configuration. The attacker can provide TopicBindingName and TopicConnectionFactoryBindingName configurations causing JMSAppender to perform JNDI requests that result in remote code execution in a similar fashion to CVE-2021-44228. Note this issue only affects Log4j 1.2 when specifically configured to use JMSAppender, which is not the default.
The default configuration of Data Platform does not meet the preconditions described for the vulnerability to be exploited.
Mitigation options
The following steps should be taken on all computers on which Data Platform components are installed:
- The following mitigation advised by Apache is appropriate to follow:
Audit your logging configuration to ensure it has no JMSAppender configured.
Logging configuration is stored in files named log4j.xml. Such configuration would be highly unusual for a Data Platform installation, and would only appear if a non-default configuration has been applied.
- Ensure appropriate access controls are in place to ensure only authorized users have access to computers. (This is appropriate to do regardless of the impact from Log4j vulnerabilities.)
- Upgrade to the Data Platform 5.5.48 release (or later). Out of an abundance of caution, Flexera has upgraded some of the Log4j components in this release of Data Platform to version 2.17.0 that is not exposed to currently disclosed vulnerabilities.
Steps to upgrade Data Platform
Perform the following steps to upgrade to the latest version of Data Platform. This is the typical upgrade process used for regular monthly releases, as documented in the Data Platform Release Notes.
- Verify that a notice indicating a new Patch Set is now available is shown in the Data Platform Admin Console after a catalog sync.
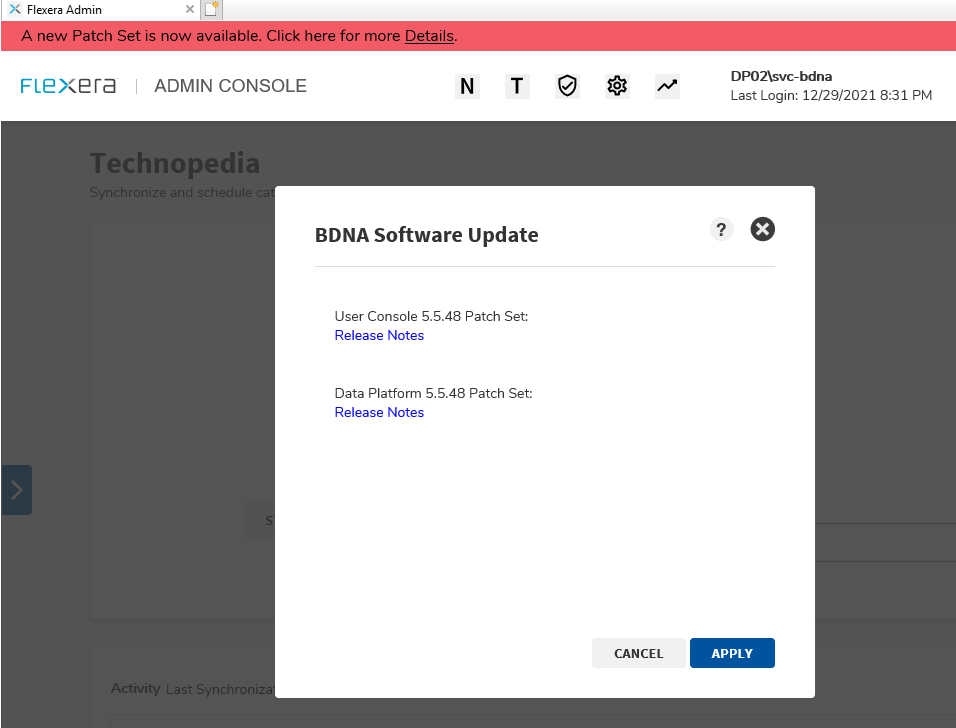
- Click the Details link to invoke the Patch Set deployment dialog. Ensure the Patch Set version shown is 5.5.48 (or newer).
- Click the APPLY button to start the Patch Set installation.
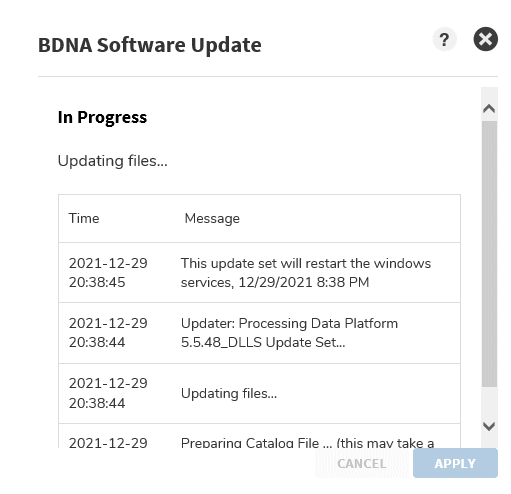
- Patch Set installation typically takes around 15 minutes. You may see an authentication dialog appear due to services restarting, which is normal. In this case, close your browser window, wait 10-15 minutes, then try logging back into the Admin Console.
- The New Patch Set Available banner will no longer be displayed when installation is completed.
Related information
Also see the following pages:
- CVE definition: https://nvd.nist.gov/vuln/detail/CVE-2021-4104
- Expanded CVE definition: https://www.cve.org/CVERecord?id=CVE-2021-4104
- Apache Log4j Security Vulnerabilities page: https://logging.apache.org/log4j/2.x/security.html
Changelog
2021-12-30 12:53 PM CST: Initial article.
2022-01-03 7:50 PM CST: Add link to Data Platform 5.5.48 release notification.
2022-02-01 11:20 PM CST: Update to clarify that not all instances of the Log4j component have been updated in the Data Platform 5.5.48 release.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- CVE-2024-9389: Data Platform User Console Command Execution Vulnerability in Data Platform Knowledge Base
- Data Platform 2022 - 5.5.58 Patch (October 2022) in Data Platform Release Blog
- Re: Log4j vulnerability in Data Platform Forum
- Data Platform mitigation for Apache Log4j 1.2 vulnerability CVE-2021-4104 in Data Platform Release Blog
- Identifying Apache Log4j JNDI Vulnerability “Log4Shell” and Variants (CVE-2021-44228, CVE-2021-45046, CVE-2021-45105, CVE-2021-4104) in Data Platform Blog