- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Forum
- :
- SVM on-prem Server ldaps Configuration
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
I need help with SVM ldaps configuration. The system I am using is RHEL 7. I have run /usr/local/Secunia/csi/install/ldapconfig.sh. Provided the host url as ldaps://servername:636. Rest all details are fine. But I am not able to connect to ldaps.
I am able to telnet 636 from SVM server. RootCA is imported in cer format to /etc/pki/tls/certs
I can connect using ldap but it can only find one UID attribute. User has read rights to users and groups outside SVM.
Thanks and Regards,
Fawad
Fawad Laiq
Jun 25, 2020 02:36 AM
- Labels:
-
Software Vulnerability Manager
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Fawad
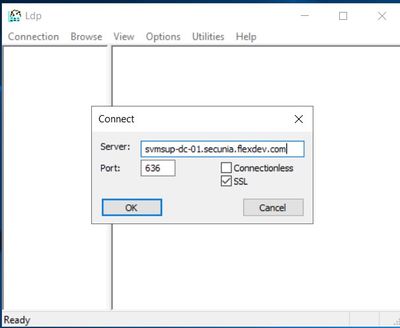
You first need to verify that you can access LDAP on 636 using the LDP tool on the Active Directory server Domain controller that you are attempting to query. To access the tool select Run from the Start menu and type "ldp" complete the server name using the full FQDN type in port 636 and Check the SSL Checkbox
Once you have clicked OK the tool will attempt to connect and if successful will look like this below:-
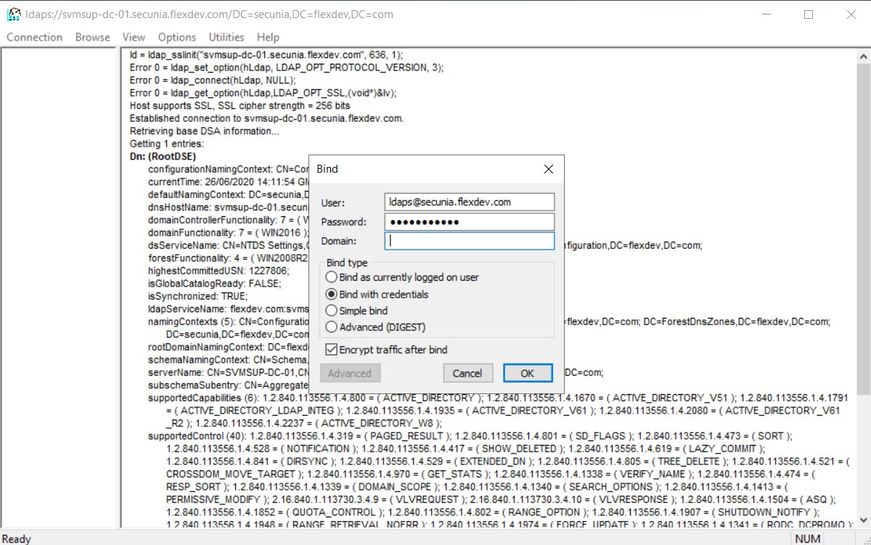
In order to query the Active Directory you will need to create a user account to use to create the BIND between the SVM Server and the AD, you can also test this using the tool to make sure it authenticates successfully.
In the LDP tool "Connection" menu select "BIND" and complete the tool with the user account you have created to use for the BIND then select the "bind with credentials" option in Windows environment it is best if you use the username@domain format as I have below:
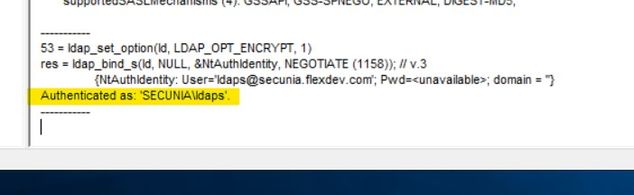
Click on the "OK" button you should see an output similar to below confirming authentication.
So now we know we can connect to the AD using Port 636 SSL and we can successfully BIND the credentials.
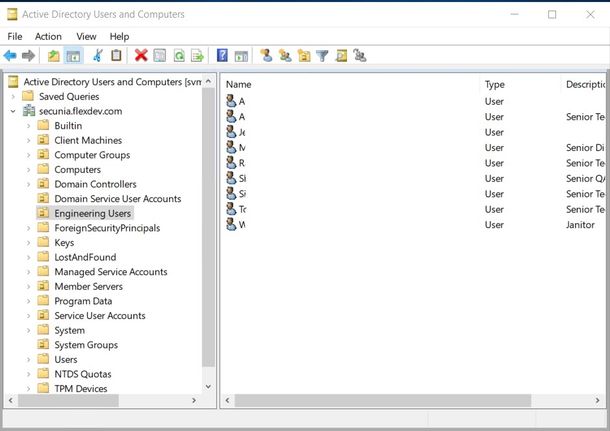
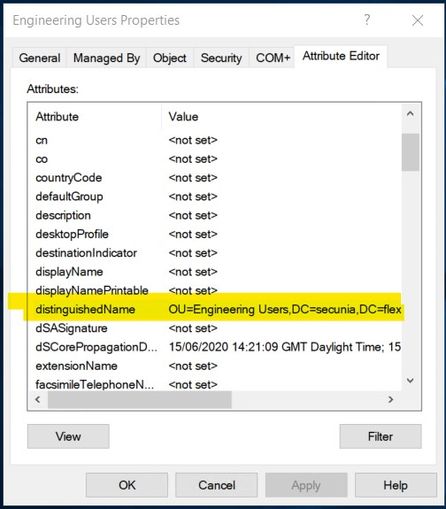
The next part we need to find out is where do we collect a list of user accounts from, these may be in a specific OU (Organisation Unit) to find out what the location of this is open your active directory Users and Computers and look for the OU that contains your users accounts:-
In the left-hand pane select the OU which contains your users, right-click on the folder and select "Properties" and select the Attribute Editor, scroll down till you come to "distinguishedName" as below:-
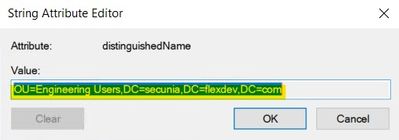
Double Click on the "distinguishedName" attribute and you will get this as below:-
This is the path you will need to enter into the SVM LDAP configuration process.
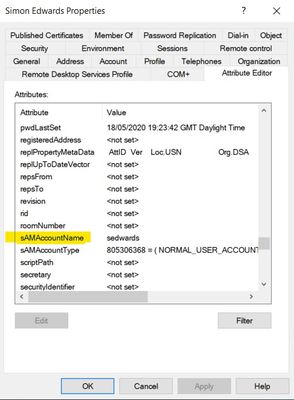
The next parameter we need to find out is the what is the distinguishing attribute that defines each user, in the Windows LDAP environment we will use the "sAMAccountName" attribute as the UID for SVM, so enter in sAMAccountName in the SVM LDAP Configuration process.
Below is a screenshot of a user account showing the sAMAccountName parameter that this is the Username
Notes:
If you are unable to connect to the AD using the LDAP Tool on Port 636 it may be that you are not using a Windows CA Certification authority in the domain issuing Server Certificates to domain controllers, if you are not using Windows PKI in your environment you will have to either look at using Active Directory Lightweight Directory Services Role and configure this with SSL.
Senior Technical Support Engineer
SVM Support
Jun 26, 2020 08:59 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Fawad
Also in regard to your certificates on the SVM Server
The Root Certificate and an Intermediate Certificates need to be in *.crt format needs to be placed in this folder /etc/pki/ca-trust/source/anchors/
Once the certificates are copied into this folder, run the follow commands:-
update-ca-trust
update-ca-trust extract
This will update the Root Certificate Bundle.
Regards
Simon Edwards
Senior Technical Support Engineer
SVM Support
Senior Technical Support Engineer
SVM Support
Jun 26, 2020 09:08 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Fawad
You first need to verify that you can access LDAP on 636 using the LDP tool on the Active Directory server Domain controller that you are attempting to query. To access the tool select Run from the Start menu and type "ldp" complete the server name using the full FQDN type in port 636 and Check the SSL Checkbox
Once you have clicked OK the tool will attempt to connect and if successful will look like this below:-
In order to query the Active Directory you will need to create a user account to use to create the BIND between the SVM Server and the AD, you can also test this using the tool to make sure it authenticates successfully.
In the LDP tool "Connection" menu select "BIND" and complete the tool with the user account you have created to use for the BIND then select the "bind with credentials" option in Windows environment it is best if you use the username@domain format as I have below:
Click on the "OK" button you should see an output similar to below confirming authentication.
So now we know we can connect to the AD using Port 636 SSL and we can successfully BIND the credentials.
The next part we need to find out is where do we collect a list of user accounts from, these may be in a specific OU (Organisation Unit) to find out what the location of this is open your active directory Users and Computers and look for the OU that contains your users accounts:-
In the left-hand pane select the OU which contains your users, right-click on the folder and select "Properties" and select the Attribute Editor, scroll down till you come to "distinguishedName" as below:-
Double Click on the "distinguishedName" attribute and you will get this as below:-
This is the path you will need to enter into the SVM LDAP configuration process.
The next parameter we need to find out is the what is the distinguishing attribute that defines each user, in the Windows LDAP environment we will use the "sAMAccountName" attribute as the UID for SVM, so enter in sAMAccountName in the SVM LDAP Configuration process.
Below is a screenshot of a user account showing the sAMAccountName parameter that this is the Username
Notes:
If you are unable to connect to the AD using the LDAP Tool on Port 636 it may be that you are not using a Windows CA Certification authority in the domain issuing Server Certificates to domain controllers, if you are not using Windows PKI in your environment you will have to either look at using Active Directory Lightweight Directory Services Role and configure this with SSL.
Senior Technical Support Engineer
SVM Support
Jun 26, 2020 08:59 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Fawad
Also in regard to your certificates on the SVM Server
The Root Certificate and an Intermediate Certificates need to be in *.crt format needs to be placed in this folder /etc/pki/ca-trust/source/anchors/
Once the certificates are copied into this folder, run the follow commands:-
update-ca-trust
update-ca-trust extract
This will update the Root Certificate Bundle.
Regards
Simon Edwards
Senior Technical Support Engineer
SVM Support
Senior Technical Support Engineer
SVM Support
Jun 26, 2020 09:08 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi Simon,
This worked, thanks a lot.
Fawad Laiq
Jul 03, 2020 05:46 AM
- SVM Agent Error: 300 Server returned error when processing results in Software Vulnerability Research Knowledge Base
- SVM March 2023 Update in Software Vulnerability Management Release Blog
- Visual Studio 2010 Shell (Isolated) installed with SQL Server 2014 or SQL Server 2012 . in Software Vulnerability Manager Knowledge Base
- Apache Log4j “Log4Shell” and Beyond in Software Vulnerability Management Blog
- How to configure Mariadb 10.3 from Mariadb 5.5 on SVM On-premise Server in Software Vulnerability Manager Knowledge Base