- Flexera Community
- :
- FlexNet Manager
- :
- FlexNet Manager Knowledge Base
- :
- Secure your estate with HTTPS and TLS
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
- Article History
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Introduction
- Transport Layer Security (TLS)
- What is TLS?
- Set Up TLS
- Hypertext transfer protocol secure (HTTPS)
- Set up HTTPS
- Import certificate into IIS
- Import the certificate into trusted stores
- Application server (Inventory/ Batch/ Presentation server)
- Beacon server
- Agent machines
- Renewing Certificates
- Bypassing Certificates
- Windows Machines
- Unix-based machines
- Mutual TLS
- Common Errors
- Revocation check failure
- OpenSSL error
Introduction
Enabling Transport Layer Security (TLS) and Hypertext Transfer Protocol Secure (HTTPS) adds end-to-end security to any communications within FlexNet Manager Suite or Flexera One ITAM that occur over the internet. This article describes the purpose of TLS and HTTPS and walks you through setting up these protocols in your FlexNet Manager Suite or Flexera One ITAM environment.
Transport Layer Security (TLS)
What is TLS?
Transport Layer Security (TLS) is a cryptographic protocol that provides end-to-end security of data sent between applications over the internet. It encrypts data sent over the internet to ensure that eavesdroppers and hackers can't see what you transmit. TLS is most familiar to users through its use in secure web browsing (you may have noticed the padlock icon that appears in web browsers when a secure TLS session is established). TLS is particularly useful for private and sensitive information such as passwords, credit card numbers, and confidential personal correspondence. It's also used for other applications such as e-mail, file transfers, video/audioconferencing, instant messaging, voice-over-IP, and internet services such as DNS and NTP.
TLS does not, however, secure data on end systems. It simply ensures the secure delivery of data over the internet, avoiding possible eavesdropping or alteration of the content.
Set Up TLS
To set up TLS to secure and encrypt internal FlexNet Manager Suite communication between agents, beacons, and the application server, see How to set up HTTPS (SSL/TLS) to secure and encrypt internal FNMS communication between agents, beacons, and the application server.
Hypertext transfer protocol secure (HTTPS)
HTTPS relies upon the transmission of TLS/SSL certificates, which verify that a particular provider is who they say they are. When a user connects to a webpage, the web server will send its SSL certificate to the client. The SSL certificate holds the public key necessary to start the secure session.
Set up HTTPS
There are two steps to configure HTTPS: import the certificate into IIS and import the certificate into trusted stores. Each component requires one or both processes to complete HTTPS setup. The following steps will walk you through the process.
NOTE: You can configure HTTPS on all aspects of FlexNet Manager Suite. For Flexera One ITAM, you only need to implement HTTPS on the beacon and can skip the steps to configure HTTPS on the application server.
Import certificate into IIS
To configure your presentation server to be viewed as HTTPS, first set up IIS to accept and serve HTTPS communication:
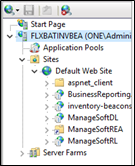
- Open IIS and select your server's name located on the top of the left navigation bar in IIS Manager.
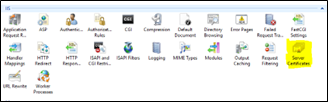
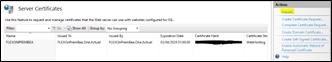
- Double-click on the Server Certificates icon.
- Import a commercial SSL certificate from a known certificate authority or create a self-signed certificate with the application server's hostname or FQDN.
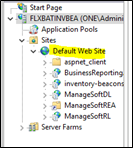
- Under Sites in the left navigation bar, select Default Web Site.
- Select Bindings on the right sidebar.
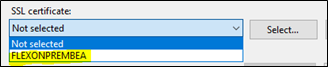
- Add HTTPS to the list and select your desired SSL certificate.
- Restart IIS.
- Test logging into the web UI with https://YourServerName from another machine.
NOTE: Ensure no network firewalls block TCP port 443 (or the configured port in step six above) between the application server and the beacons.
Import the certificate into trusted stores
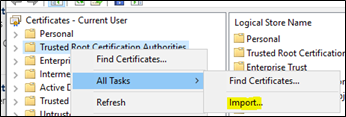
- Open a Run window and type in certmgr.msc.
- Right-click Trusted Root Certificate Authorities, then select All Tasks > Import…
- Based on the SSL Certificate source that you used in IIS on the application server, follow one of the steps below.
- If you're using a commercial SSL certificate from a known certificate authority, import the root certificate from your SSL certificate authority (for Flexera One ITAM customers, install DigiCert Global Root CA).
or
- If you're using a self-signed SSL certificate, import the certificate under Trusted Root Certificate Authorities\Local Computer as shown to be used by the Local System Account. You can export self-signed certificates from IIS or by viewing the certificate in your browser while running as an administrator and exporting as a base 64-encoded file.
Application server (Inventory/ Batch/ Presentation server)
You'll need to configure both your application server and beacon server to allow your inventory beacons to communicate with the application server via HTTPS and offer web UI users an end-to-end encrypted connection. To do so:
- Import the certificate into IIS on your application server following the Set Up HTTPS steps above.
- Add the certificate used on your application server to each of your beacons' trusted stores using the Import the certificate into trusted stores steps above.
If you’re experiencing issues with your beacon uploading and downloading from your application server, see the Common errors section below.
Beacon server
In FlexNet Manager Suite Cloud/Flexera One ITAM, by default, the inventory beacon requires the use of HTTPS via TLS 1.2 to communicate to the cloud application server. For assistance updating these protocols, see Transport Layer Security (TLS) 1.1 & 1.2 Configuration.
For FlexNet Manager Suite On Premises installations, by default, the inventory beacon will continue to communicate to the application server with the same method it used when installed. The inventory beacon will continue functioning if HTTP is still active on the application server. However, if HTTP is disabled on the application server, the beacon cannot communicate with it.
To enable HTTPS communication to allow agents to connect via HTTPS, follow the Import certificate into IIS steps above, then do the following:
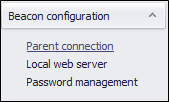
- Open the FlexNet Beacon UI.
- Select Parent Connection in the left navigation bar.
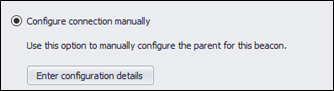
- Select Configure Connection Manually.
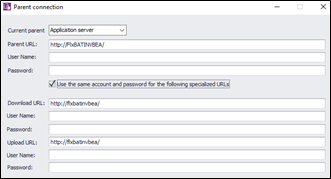
- For each connection URL, change HTTP to HTTPS and configure the URLs with either the FQDN or the server name you previously set when importing the certificate into IIS on the application server.
- Select Ok, then select Save on the beacon.
Agent machines
After implementing the certificates on your beacons, each agent must be configured individually on Unix-based operating systems. For Windows machines, you can push the certificates out via group policy.
New Unix-based machines (Linux, Mac, etc.)
Refer to Agent Third-Party Deployment: Enabling the HTTPS Protocol on UNIX Agents. Note that you must place the certificate in the same folder as the installation media.
Existing Unix-based machines
Refer to the steps in Agent Third-Party Deployment: Enabling the HTTPS Protocol on UNIX Agents; however, you must add the certificate file as a cert.pem file instead of the MGSFT_rollout_cert file into the following location on each machine: /var/opt/managesoft/etc/ssl.
Windows Lite Agents
You can push the certificates out via group policy, or you can add the following arguments to your ndtrack command:
-o CheckServerCertificate=false -o CheckCertificateRevocation=false
Renewing Certificates
To renew certificates, follow the same procedure as you did to add the certificate initially. Currently, there is no way to renew certificates centrally from Flexera One ITAM or FlexNet Manager Suite.
Bypassing Certificates
You can disable the certificate or revocation check as an initial way to ensure that the agents and beacons can communicate properly. You can also use this method if a device will only be accessing the beacon/application server using internal networks. Enabling this as a full-time solution is not recommended, as it is less secure and makes implementing HTTPS obsolete.
Windows Machines
New Machines
Add the following lines under [Common] in your bootstrap mgssetup.ini file. Ensure that duplicate desc0 and desc1 lines don't exist in your current file under [Common].
desc0 = CheckCertificateRevocation
val0 = False
desc1 = CheckServerCertificate
val1 = False
Existing machines
Add the following strings with the value of False under this registry key HKLM\SOFTWARE\Wow6432Node\ManageSoft Corp\ManageSoft\Common for a 64-bit server or HKLM\SOFTWARE\ManageSoft Corp\ManageSoft\Common for a 32-bit server:
CheckServerCertificate
CheckCertificateRevocation
Unix-based machines
New machines
Disable the certificate and revocation checks by adding the following lines in the mgsft_rollout_response file.
MGSFT_HTTPS_CHECKSERVERCERTIFICATE=false
MGSFT_HTTPS_CHECKCERTIFICATEREVOCATION=false
NOTE: If these lines already exist, modify them by removing the "#" sign.
Existing machines
Disable the certificate and revocation checks by adding the following lines under [ManageSoft\Common] in the FlexNet inventory agent's /var/opt/managesoft/etc/config.ini file.
CheckServerCertificate=false
CheckCertificateRevocation=false
Mutual TLS
Mutual TLS (mTLS) authentication can help ensure trust between beacons and inventory devices. Mutual TLS can be configured if certificates are installed on beacons while inventory device computers run the FlexNet inventory agent. For more information, see Using Client Certificate Mapping Authentication in IIS for mutual TLS (mTLS) authentication of computers running the FlexNet inventory agent.
Common Errors
Both the revocation check failure error and OpenSSL error frequently occur due to the installed certificate having an issue accessing the revocation chain. Resolve these errors by checking the certificate chain for errors within the certificate.
Revocation check failure
The revocation check failure error is slightly different depending on the device's operating system, but it generally looks like the image below.
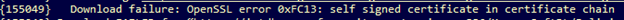
OpenSSL error
The OpenSSL error is like the revocation check failure error but occurs more often on Unix-based operating systems.
May 12, 2023 01:19 PM - edited Jul 19, 2023 11:52 AM