- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- SVM Patch Automation FAQ
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Does this functionality have an additional cost?
No, this is a new capability of the core SVM product. It is available on both our hosted cloud instance of SVM as well as in our on-premise version. No special licensing or unlocking of the feature is necessary. If you do have the Vendor Patch Module, the feature is also available to automate those patches and works the very same way they do for the included SPS patches.
Does this functionality require the Vendor Patch Module?
No, it does not. Patch automation applies to both SPS (included) and VPM (optional) patches.
Does automation require special configuration?
Yes, without proper configuration configuring subscription options made in the console will only save your desired settings with no action take. Actual implementation of these settings requires installation and configuration of a new daemon.
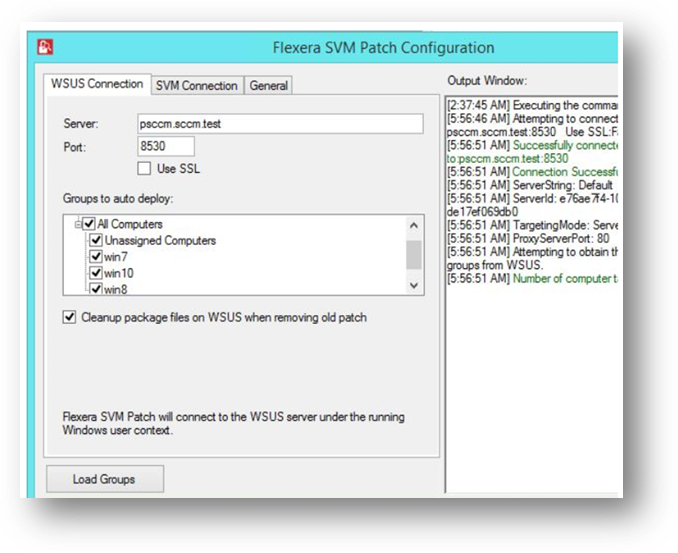
To do so install and configure the new version (v2.0) of the Flexera SVM Patch Configuration
Patch automation is delivered via a new version of the Flexera SVM Patch Configuration (Version 2.x) tool, which is part of the Software Vulnerability Manager Client Toolkit. The SVM Toolkit installer contains updates to the Flexera SMV Patch Configuration tool as well as some optional tools documented in our online community. The SVM Toolkit installer can be downloaded at:
https://resources.flexera.com/tools/SVM/SVMClientToolkitInstall.msi
NOTE: If you already have the SVM Toolkit installed, the installer will upgrade you to the latest version.
How do I automate a patch?
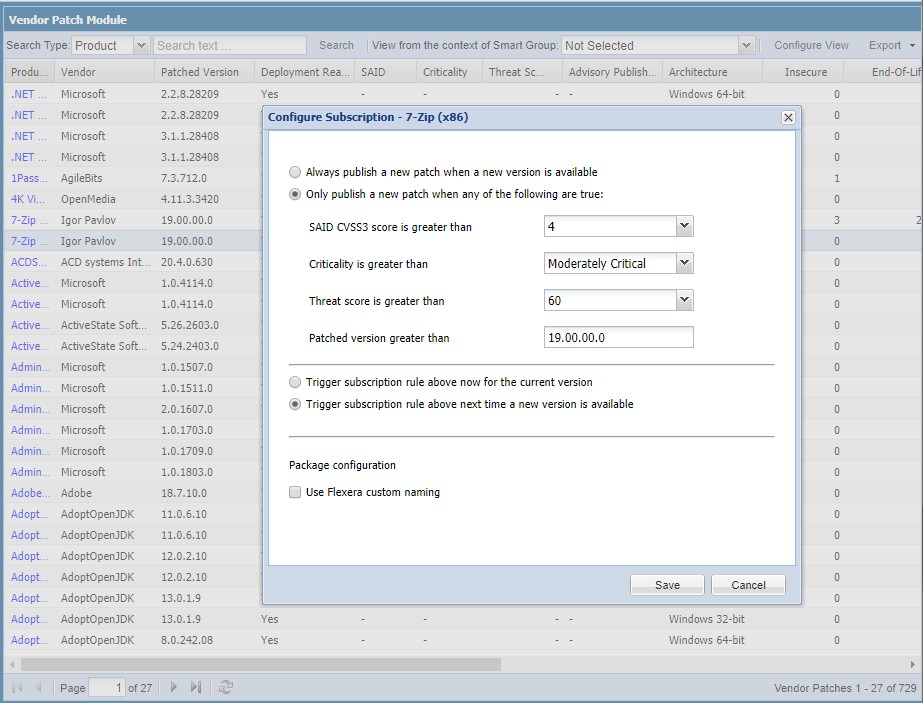
Simply right click on any SPS or VPM patch and choose “Subscribe to Patch”. From here you can choose to always publish a new patch when it becomes available, or you can choose to only automate publishing a new patch when certain criteria are met (recommended).
Should I automate everything?
We do not recommend over-using patch automation. Automation does not change the fact that any patch deployment should undergo proper testing and validation to ensure there are no unexpected consequences. Even when a patch is successful, there is some risk that it could affect other applications or services on the endpoint. Automation of patch deployment to test systems can increase the number of patches you can manage, but care should still be taken to ensure you are automating the right patches.
To facilitate this, you can not only choose for which applications you’d like to publish new patches, but for each of those you may set limits to publish only those that meet your specified criteria. Which may be based on one or more of the following:
- CVSS Score (based on advisory vulnerability score)
- Criticality (based on criticality level)
- Threat Score (based on likelihood of exploitation) *
- Minimum Version (to only automate if the version is higher than that specified)
* Appears only when licensed for Threat Intelligence Module
How should I choose what to automate?
We recommend you take a phased approach to determine how many patches you can comfortably manage through the testing and deployment process. We recommend getting comfortable with the feature by starting with simpler applications that you feel are of relatively low risk. Then, add applications that you feel would offer the most value and set criticality and threat limits to publish only those that are a priority. Over time, you can add more applications and/or reduce the criteria for automation to increase the volume of automatically published patches.
Are there some patches I cannot automate?
All SPS patches are supported once you’ve created a template to specify your desired settings. For Vendor Patch Module, patch automation requires it be identified as a “deployment ready” patch. As of March 2020, over 1,200 of the patches provided by VPM are designated as “deployment ready”. The remainder cannot be automated because vendor limitations prevent our ability to provide everything necessary to provide an out of the box patch that would satisfy automation needs.
If you would like to determine just which patches are deployment ready, you can filter for such in SVM or look to those items marked with an asterisk in our online list of available patches.
How can I determine the status of automation actions?
In the near future, we intend to offer an option to receive a daily digest of activity. For now, you can review logs either in a new “Subscription Status Log” or in the product’s main “Activity Log”.
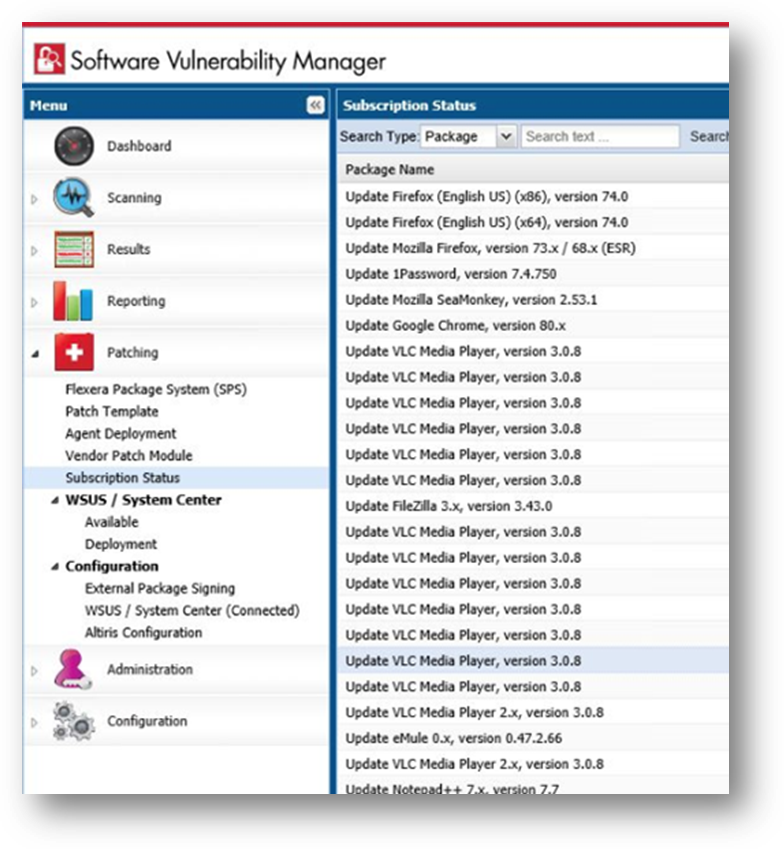
You can see the status and details of patches published automatically on a new page named Subscription Status, which is opened by selecting Subscription Status on the Patching menu.
Like all activities, patch level activities are also recorded in the Activity Log, which can be viewed by selecting Activity Log from the Configuration menu.
How can I dictate that newly published patches automatically deploy to pilot systems?
SCCM offers Automatic Deployment Rules (ADRs) to allow you to specify what happens with new updates when they appear. A good video (an external resourced) on setting up WSUS and SCCM ADRs can be found at https://www.youtube.com/watch?v=a2AWwhUaQuw
Alternatively, you can use the SVM Console or the SVM WSUS Management Tool to review and approve newly published patches.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- SVM August 2024 Update in Software Vulnerability Management Release Blog
- SVM On-prem July 2024 Update (SVM installation is now supported in RHEL 8) in Software Vulnerability Management Release Blog
- SVM June Update (CVSS v4.0 support is here..) in Software Vulnerability Management Release Blog
- NVD vs Secunia Research: Enhancing Vulnerability Management in Software Vulnerability Management Blog
- SVM April 2024 Update in Software Vulnerability Management Release Blog