The Flexera Community is currently in maintenance mode to prepare for the upcoming launch of the new community. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Release Blog
- :
- SVM December 2020 Update
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Software Vulnerability Manager December 2020 update is live now. This release adds a most requested and very significant feature to SVM along with some valuable product enhancements.
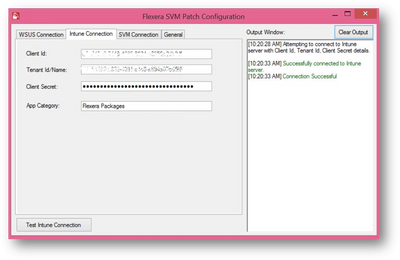
Publish patches to Microsoft Intune from SVM
SVM integration with Intune was on top of our list of priorities based on many of our customer requests. You can now publish both the Flexera Software Package System (SPS) and Vendor Patch Module (VPM) patches to Intune from SVM. The SVM Patch Configuration tool (aka Patch Daemon) lets you setup a connection between SVM server and Intune. This capability is applicable to both automatic (subscribed packages) and manual (single patch) publish.
Please note that when a patch is published from SVM to Intune, you may be required to make edits, in Intune, to the Requirements and Detection Rules automatically set by the SVM to meet your requirements. This is a known issue; we will be releasing a new version of Patch Daemon soon to fix this issue.
New Data APIs
Three new data APIs are added in this release to help you download the assessment data from SVM and persist in your local database. If you wish you build a historical report for your organization to understand the trends of vulnerabilities from a device and software standpoint, then these are the APIs for you.
Agent Caching of Scan Rules
New scan agents available with this release, will now cache scan rules. Agents servers will determine if the agent needs a new set of rules and will only push these rules if needed. This will result in decrease in the amount of network traffic generated by the scan agents which will be especially beneficial in very large environments. To take benefit of this enhancement, the current version of the scan agent in your environment should be upgraded to the new version of the agent - 7.6.0.15.
For more details regarding our December update, please see the full release notes here.
- SVM On-prem December 2023 Update in Software Vulnerability Management Release Blog
- SVR December 2023 Update in Software Vulnerability Management Release Blog
- SVM December 2023 Update in Software Vulnerability Management Release Blog
- Monthly Vulnerability Insights: December 2022 in Software Vulnerability Management Blog
- SVM On-prem December 2022 Update in Software Vulnerability Management Release Blog