A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review: October 2019
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The Monthly Vulnerability Review blog aims to deliver security insights derived from analyzing the software vulnerabilities processed, analyzed, and verified by Secunia Research at Flexera each month. By doing so, we aim to present the bigger picture that can serve as a baseline for organizations to adopt better vulnerability management strategies, as we also deliver ultimate insight on which vendors are most often being vulnerable.
Flexera discloses vulnerabilities through its proprietary Secunia Advisories (SAIDs). One Secunia Advisory can report on one or more software vulnerabilities. When there is more than a single software vulnerability contained in a given advisory, the “Title” of the SAID will indicate “Multiple Vulnerabilities.” When there are multiple products reported in a single Secunia Advisory, the title will mention "Multiple Products." Additional details about the proprietary Secunia Advisory can be seen in our first blog edition.
Monthly Advisory Overview
Between October 1 – November 1 of 2019, there have been 441 new Secunia Advisories processed by Secunia Research. That represents a 9% increase from September to October. Of the total 441 advisories, 27% reported multiple vulnerabilities in each separate Secunia Advisory. 37.1% were attributed only to Linux-based software packages for the various distros tracked in the Flexera software vulnerability database.
The remaining 276 SAIDs (62.9%) cover all other software products, operating systems, and platforms. Linux Kernel flaws and software vulnerabilities found in various Linux operating systems have not been included in the previous 37.1% statistic, and are accounted for in the 62.9% altogether with the rest.
Products and Vendors
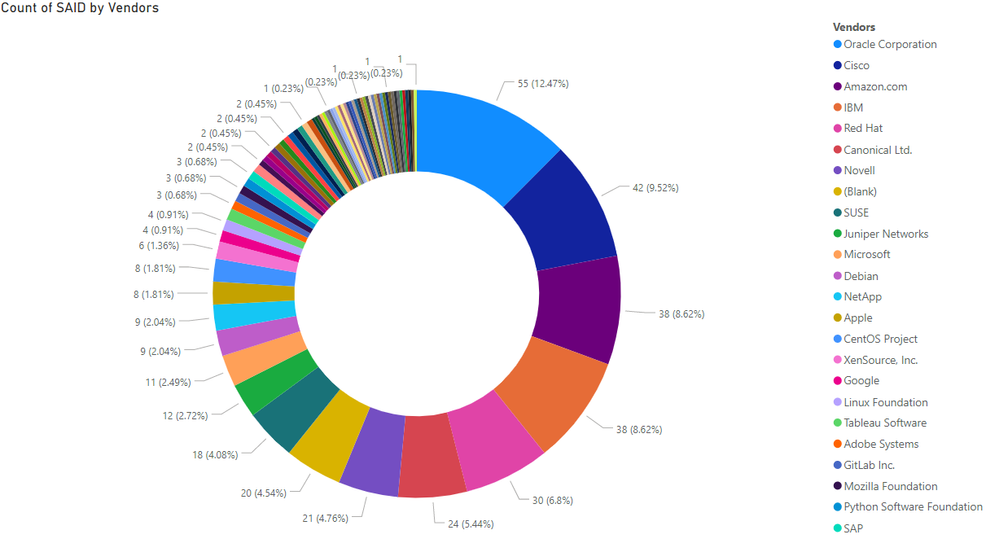
Flexera has attributed the 441 advisories to 377 different software product versions, from 296 unique product titles, released by 74 different vendors. While there have been five vulnerable vendors less compared to the data from September, we saw an increase of 33 more product titles from 263 to 296 in October, and also an increase of 22 product versions from 355 to 377.
In October, Oracle Corporation had most security advisories attributed to them with a total of 55 SAIDs. They’ve had 13 SAIDs more than what Cisco had on their name, and 17 more than Amazon and IBM. In percentages, Oracle holds 12.47% monthly advisory share, Cisco has 9.52%, while IBM and Amazon have 8.62% each. With Red Hat’s 6.82%, the top 5 vendors held 46.05% of all Secunia Advisories processed by Flexera that month.
Advisory Criticality
We made a breakdown of the criticality ratings assigned to all Secunia Advisories processed by Flexera in October of 2019. There have been no Extremely Critical advisories, 17.91% SAIDs have a Highly Critical rating, 36.28% Moderately Critical, 35.15% Less Critical, while the remaining 10.66% advisories classified with the Not Critical rating by Flexera. The numbers on the right side provided below show the increase or decrease in the advisory counts between September and October months.
- “Extremely Critical” = 0 (-)
- “Highly Critical” = 79 (-13)
- “Moderately Critical” = 160 (+19)
- “Less Critical” = 155 (+30)
- “Not Critical” = 47 (+1)
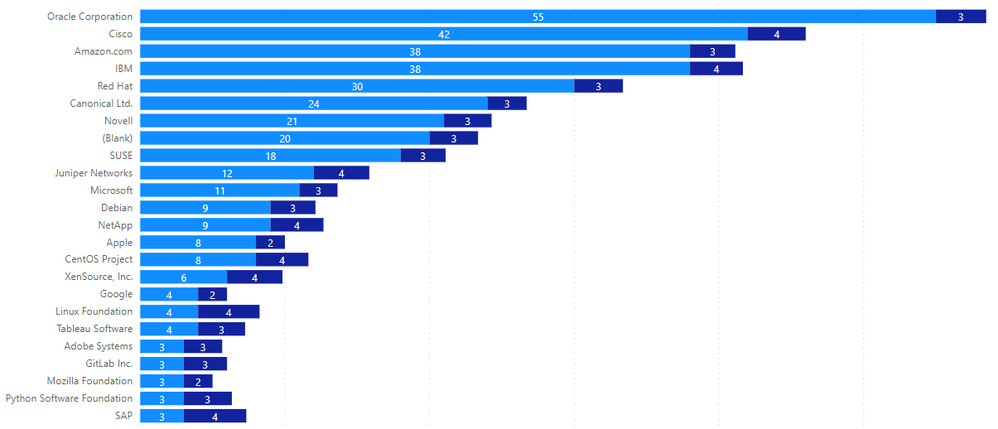
We analyzed the average criticality rating per advisory assigned to the top 25 list of vendors with most Secunia Advisories attributed to them. "Blank" refers to a collection of "various open-source software" such as Jenkins, Go, Piwigo, Netty, etc. and not to a single vendor as it is the case with the rest in the list.
The light-blue numbers display the amount of Secunia Advisories attributed to each vendor, while the dark-blue numbers indicate the average per-advisory criticality rating result. Adobe Systems, Mozilla Foundation, Google, and Apple topped average criticality per the advisory, with all of them sharing a “Highly Critical” rating. The last entry in the top-5 criticality list goes to Microsoft based on a criticality rating average of 2.636 per Secunia Advisory. Criticality average of 2.636 out of 11 advisories means that almost every advisory attributed to Microsoft has a Highly Critical rating.
Because Apple had more advisories than the first three vendors, and few less than Microsoft, it ranked as the most critical vendor to handle among these five titans of modern-day software. We must also note that those vendors had significantly fewer Secunia Advisories attributed to them than the vendors in the top 5 which would normally play a role in the average measurements and comparisons.
For the record, a criticality rating of 1 translates into "Extremely Critical" (e.g., priority 1), while the criticality rating of 5 translates into a "Not Critical" rating as per the Secunia Research assignments.
Attack Vectors
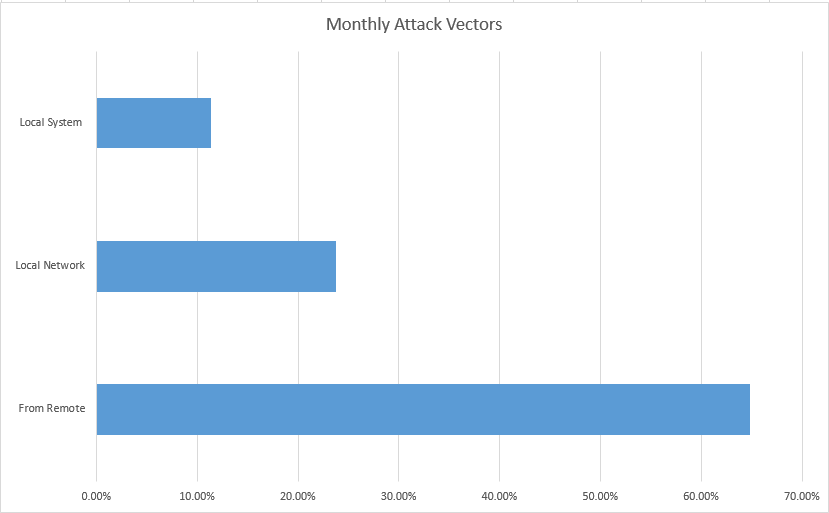
In October, there has been a significant increase in remotely exploitable vulnerabilities. There was a 4.6% increase in the overall monthly share of security advisories reporting vulnerabilities identified as remotely exploitable. It reached 64.85% (286/441) in October, while the monthly share for September was 60.25% (244/405). The difference of 42 SAIDs represented an actual 17.1% increase from September to October in the count of advisories that contain remotely exploitable vulnerabilities.
Another 23.81% advisories disclosed on software vulnerabilities identified with the “Local Network” attack vector. The security advisories reporting vulnerabilities exploitable from “Local System” were a total of 11.34%.
CVSS3 Scores
We’ve made a breakdown of the CVSS3 scores of all October advisories into three specific ranges:
- Low Severity Range (CVSS3 0-4)
- Medium Severity Range (CVSS3 4-7)
- High Severity Range (CVSS3 7-10)
Because Secunia Research assigns CVSS3 scores on an advisory level, this breakdown helps us to identify which CVSS3 range had a predominant amount of Secunia Advisories each month. In October, 4.1% of all advisories resided in the low-severity range, 38.5% resided in the medium-severity range, and 57.4% resided in the high-severity range. The following sums up the exact count of advisories in each range:
- SAIDs in the Low CVSS3 range = 18 (-11)
- SAIDs in the Mid CVSS3 range = 170 (+42)
- SAIDs in the High CVSS3 range = 253 (+5)
Next to the main numbers in bold, you see the increase or decrease in advisory counts as compared to the month before. We can spot a pattern where forty-two extra Secunia Advisories have been added to the medium-severity CVSS3 range, reminding us of the 42 advisories added to the “From Remote” attack vector percentages that we saw earlier.
That is a strong indication that many, if not all, the newly added remotely-exploitable vulnerabilities resided in the medium-criticality CVSS3 scoring range, judging by the patterns seen in this analysis. That should lead to an increased focus on the less-severe weaknesses, because overlooking such flaws may have dramatic consequences to every organization that neglects the mid-ranges (you WannaCry?).
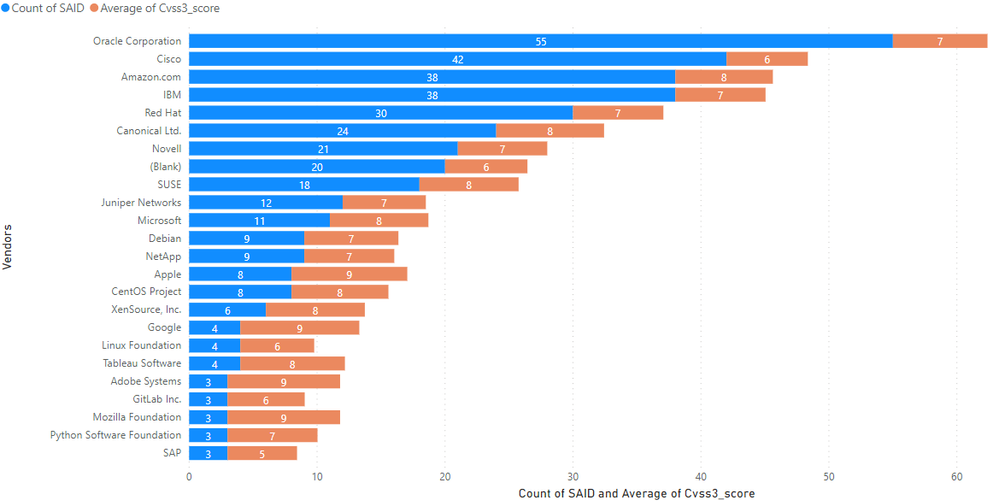
Adobe Systems, Mozilla Foundation, Google, and Apple were the most severe with an average CVSS3 of 9 per the issued advisory, but that is because they had a lower number of advisories attributed to them. Still, the most severe was Apple due to having had twice as many advisories as the first three. From the vendors with the highest number of reports, Amazon Linux flaws have been more severe than others, as this vendor ranked a top performer in SAID counts, criticality, severity, and remote attack vectors too.
Monthly Vulnerabilities
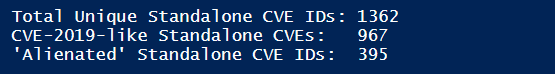
During October of 2019, Secunia Research detected, verified, and disclosed on at least 1362 unique standalone software vulnerabilities represented by that much unique CVE identifiers. That is a base minimum that you should consider because Flexera also reveals on software vulnerabilities that do not have a CVE identifier (yet). Those vulnerabilities have not been included in our blog analysis.
Of the 1362 unique vulnerabilities with a CVE ID, 29% have been reserved and disclosed in previous years, also referred to as “alienated vulnerabilities.” The remaining 71% are vulnerabilities that have had their CVE ID reserved and reported publicly as an active vulnerability in the year we are in now – 2019.
If we analyze the 1362 security flaws on average against this month’s vendor and product data, we can measure that there has been an average of 18 software vulnerabilities per vendor (74), nearly five software vulnerabilities per product title (296), and about four vulnerabilities per product version (377).
However, this is the case only if we measure one unique CVE as one standalone vulnerability. That is simple math that allows us to make a fundamental analysis of the monthly security risk as a minimum. Still, it does not yet reflect the real big picture as realities on the vulnerability landscape are different.
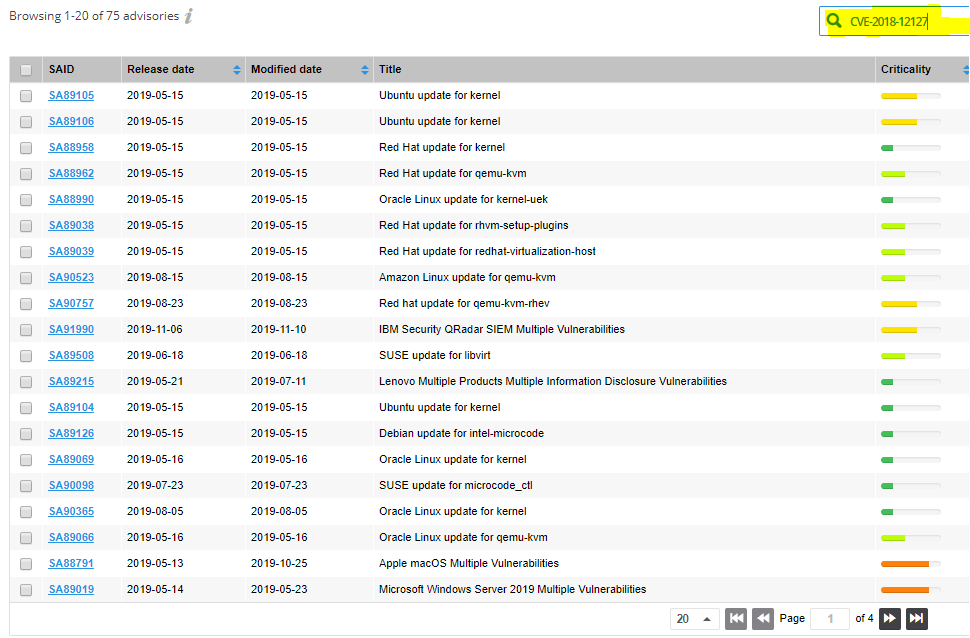
The reality is that many vulnerability IDs can (and usually will) be replicated across multiple Secunia Advisories because a single CVE ID can often affect more than one software product and vendor. An example of a few CVE IDs that exposed dozens of vulnerabilities in different vendors and products could be Intel’s Fallout/RIDL/ZombieLoad side-channel attacks.
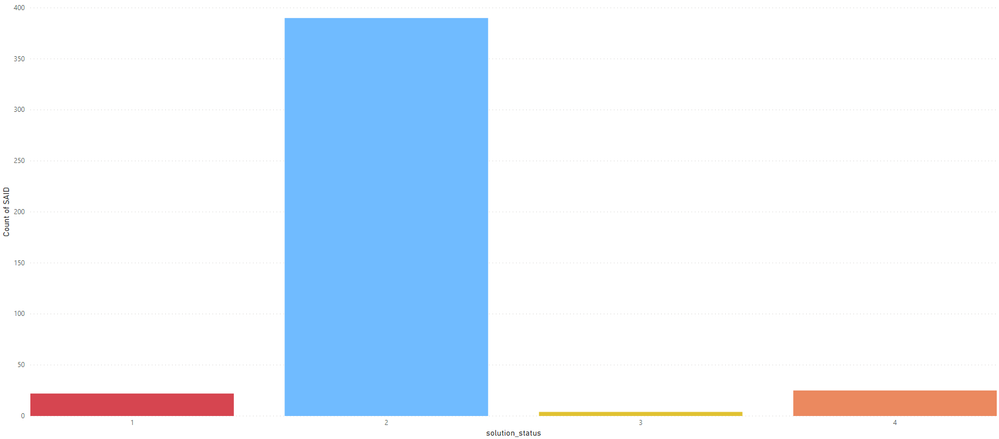
In the next screen, we make an example with one of the four Intel MDS CVE IDs, CVE-2018-12127, which affected dozens of products and vendors, for as many as 75 different SAIDs (until today and keep counting):
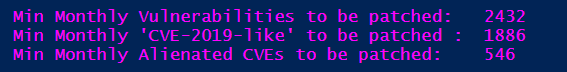
If we identify the number of vulnerabilities using the correct logic as explained here, the actual amount of software vulnerabilities detected and disclosed by Secunia Research jumps up to 2432 vulnerabilities.
The vulnerability counts for October, as seen through the data analyzed by us, represent a 39% increase in the standalone unique CVE ID counts from September to October (1362/978), and a 37% increase in the actual amount of detected by Flexera product-based vulnerabilities (2432/1778). That covers Linux-based software packages, all operating systems, all platforms, and all software products altogether.
Threat Intelligence Overview
Threat Intelligence Module leverages machine learning, artificial intelligence, and human curation from thousands of sources in the open, deep, and dark web. The module augments Software Vulnerability Manager’s world-class vulnerability intelligence with a threat score that provides the ultimate prioritization tool for your busy desktop operations teams.
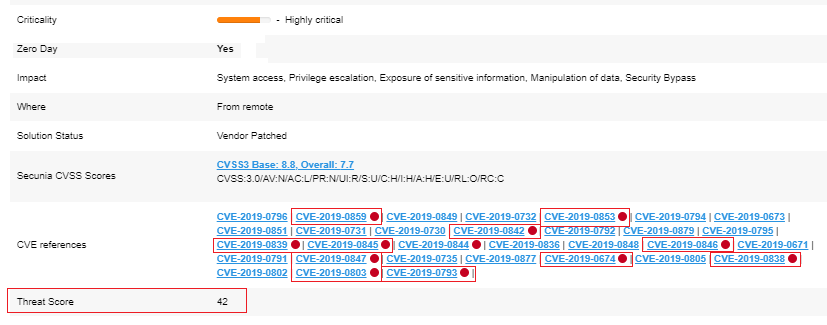
In October, 52.15% of all Secunia Advisories have disclosed on at least one vulnerability that has any evidence of a known exploitation threat. The remaining 211 advisories have not been linked to a known threat yet. Of the 52.15% advisories with a positive threat score, we can analyze the following statistics:
- 187 advisories reside in the low threat score range
- 37 SAIDs live in the medium threat score range
- 3 advisories reside in the high threat score range
- 3 advisories reside in the critical threat score range
- Vulnerabilities in 185 advisories linked to a historical cyber exploit
- Vulnerabilities in 92 advisories related to recent cyber exploits
- Vulnerabilities in 82 advisories related to Penetration Testing tools
- Vulnerabilities in 22 advisories linked to a to Malware
- Vulnerabilities in 3 advisories have linked a to Ransomware.
Additionally, Flexera has observed through its Threat Intelligence module at least 17 different malware families linked to a subset of CVE IDs that appear to be easily targeted and easily exploited by more than one malware family at a time. This information is available through the Flexera SVR REST API by dumping the full month data locally and performing an additional post-analysis of the malware titles linked to each advisory. SVR customers who have Threat Intelligence module included with their software can request more details on how this is scripted by contacting Flexera Support about it.
Time-To-Patch
In October, 88.44% of the released Secunia Advisories have a patch provided by the vendor. These advisories contained 93.87% of the vulnerabilities detected by Secunia Research at Flexera that same month! That leaves only 6.13% of all vulnerabilities reported over a whole month without a direct patch solution. For those flaws, you can apply a workaround where needed and where possible.
The amount of detected and disclosed vulnerabilities indeed goes higher and higher in the past many years, but that is a good thing because it demonstrates that there is more quality security vulnerability research. The vendors and the security community are discovering more security flaws. Patches are coordinated accordingly to the responsible disclosure principle in a timelier manner, also thanks to specialized websites that help intermediate vulnerability coordination in favor of speed, simplicity and to ensure that security researchers are rewarded accordingly for their consistent research work.
That leads to an increasing amount of software vulnerabilities that have a vendor patch on the day of the public disclosure. 93.87% of all vulnerabilities having a vendor patch is massive news in terms of the current situation of a high vulnerability increase from one month to another, but also a historical aspect. There is no better moment of emphasizing on the importance of vulnerability patching.
Flexera has the solution capabilities of delivering verified actionable vulnerability intelligence to your doorstep in a mostly automated fashion. It also has the means and capabilities to offer the most extensive collection of ready-to-deploy software packages through the Software Package System (SPS), and the Vendor Patch Module (VPM) provided through the Software Vulnerability Manager solution. There is no better time for organizations to look at upgrading their patch management technologies. Only 1 out of 20 vulnerabilities does not have a patch provided by the vendor. Many times, this 1 security weakness will have a workaround or partial fix.
Flexera can help organizations simplify their patching effort and achieve appropriate and very needed automation of detecting vulnerabilities and prioritizing a security patch against them, through an intelligent and fully integrated to your domain manner, for as many as 1.000 software product versions in several hundred unique product titles available through the SVM Vendor Patch Module and SVM Software Package System.
That is a resource that should be used for everyone's advantage, as much as possible, in times when security breaches make the news headlines every single day. There has always been a general lack of extensive amount of third-party software patches that can be tied to the security posture and prioritized through a single interface to drive domain security faster at its very core. By providing such capabilities, Flexera already helps many organizations gain a timely advantage against hackers to minimize their software attack surface to a minimum by assisting them to remain protected at the root on an ongoing basis.
- Monthly Vulnerability Insights: October 2024 in Software Vulnerability Management Blog
- SVM October 2024 Update in Software Vulnerability Management Release Blog
- Monthly Vulnerability Insights: September 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: August 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: July 2024 in Software Vulnerability Management Blog