A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Third Party Thursday: Your place to learn about the latest reported software vulnerabilities
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The aim of this blog is to provide a review of the software vulnerabilities reported by Flexera, in this case for the period from March 28 to April 25. We analyzed the vulnerabilities, vendors and software that have new security risks. I will explore the data to look at it from different perspectives, in order to see the big threat picture that is being introduced. And I will try to answer the following questions:
- Which vendors are insecure, and which ones are less secure more than others? How did they compare to each other?
- What overall security risk has been introduced by third-party software and Microsoft altogether?
- Why we shouldn’t underestimate low-criticality ratings and CVSS, and what danger does that hold?
- How Threat Intelligence can help us figure out complex questions and achieve advanced prioritization?
We will track vulnerabilities by counting one Secunia Advisory ID (SAID) as one vulnerability. In fact, 50% of the advisories referenced in this blog have “multiple vulnerabilities” listed in their title. That tells us there is possibly many reported issues. There are some very shocking advisories that include immense amounts of issues. I have included some examples in the blog.
What is Secunia Advisory ID (SAID)?
Secunia Advisory ID is a proprietary security advisory bulletin issued by Flexera in the event a new software vulnerability is discovered by Secunia Research, or reported publicly by the corresponding affected vendor, another third-party security team, researcher or reporter.
SAIDs are synonymous with world-class vulnerability research and human-curated vulnerability intelligence. After enabling the optional Threat Intelligence module to Software Vulnerability Manager and Software Vulnerability Research solutions, threat score will also be included within SAIDs.
What is Threat Intelligence?
Threat Intelligence Module leverages machine learning, artificial intelligence and human curation from thousands of sources in the open, deep and dark web. The module augments Software Vulnerability Manager’s vulnerability intelligence with a threat score that provides the ultimate prioritization tool for your busy desktop operations teams.
Monthly Advisory Overview
Between March 28 and April 25, Flexera released total of 469 Secunia Advisory IDs, without counting advisories released as “Rejection Notice." About 55% of the vulnerabilities reported in 469 SAIDs have been associated with a known threat and more than half of all advisories reported on multiple vulnerabilities. Here is summary of the 55% with a known threat:
- 193 SAID have low threat score (1-12)
- 50 SAIDs have medium threat score (13 - 23)
- 6 SAIDs have high threat score (24 – 44)
- 6 SAIDs have critical threat score (44 – 70)
Monthly Sorting Through Criticality
Here is a summary of the criticality ranges contained in 469 new Secunia Advisory IDs:
- “Not Critical” = 10% of all SAIDs;
- “Less Critical” = 35.7% of all SAIDs;
- “Moderately Critical” = 37% of all SAIDs;
- “Highly Critical” = 17.3% of all SAIDs;
I often see people that like to prioritize only based on criticality ratings without considering a more insightful approach.
Here, I want to look at an example of why is it a bad practice to look only at high ratings.
We would have to discard 45.7% of the newly reported vulnerabilities if we are to follow this practice. I will be overlooking important threats which only become apparent after analyzing the discarded data with Threat Intelligence. Here is an example of three specific advisories that would have been ignored:
- SA88212 SUSE kernel modules [Not Critical] = Historically linked to Malware; Historically linked to Ransomware; Linked to Historical Cyber Attack; [Threat Score=High] [AV=Local System]
- SA88477 Lenovo Bluetooth Security Bypass [Less Critical] = Linked to Historical Cyber Exploit; Historically Linked to Ransomware; [Threat Score=High] [AV=Local Network]
- SA88603 IBM BigFix Security Compliance Analytics [Less Critical] = Linked to Historical and Recent Cyber Attacks; Recently linked to penetration testing tools; [Threat Score=Medium] [AV = Local Network]
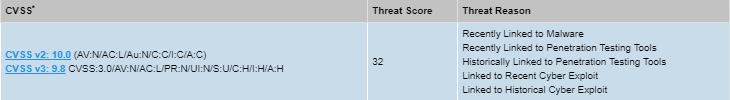
SA88212 and SA88477 report on two of the most exploited vulnerabilities in the list of 469 SAIDs judging by their high threat score. This example teaches a good lesson. Malicious actors seek to explore unexpected entry points to your network, thereby exploiting vulnerabilities that are often overlooked.
Sorting and prioritizing only by criticality rating hides risks of overlooking dangerous active threats.
Overall Impact Analysis
One Secunia Advisory may show more than one “Impact” types, depending on the possible outcomes there are from successful exploitation of the total number of vulnerabilities linked to the corresponding SAID. Next, you will see “Impact” summary derived from all vulnerabilities:
- “Denial of Service” = 42.5% of all SAIDs
- “System Access” = 27.8% of all SAIDs
- “Exposure of Sensitive Information” = 29% of all SAIDs
- “Privilege Escalation” = 11% of all SAIDs
- “Manipulation of Data” = 14% of all SAIDs
- “Cross-Site Scripting” = 9.8% of all SAIDs
- “Spoofing” = 6.8% of all SAIDs
System Access, Exposure of Sensitive Information, and Denial of Service are the most probable Impacts introduced by vulnerabilities reported by Flexera in the covered period. About 69% of all security advisories published in this period, or 323 SAIDs, reported on at least one of these impact types.
One can determine which impact types endanger the business the most based on confidentiality, integrity, availability (CIA) requirements, and start prioritizing the issues that are most urgent using that:
- DoS = Availability
- System Access = Integrity
- Exposure of Sensitive Information = Confidentiality
Threat Intelligence tells us that 61.6% of the vulnerabilities with most prevalent impact type included in the 323 new SAIDs have been associated with a known threat. This equals 199 security advisories, 70% of which reported on Moderately Critical or Highly Critical vulnerabilities (with a known threat).
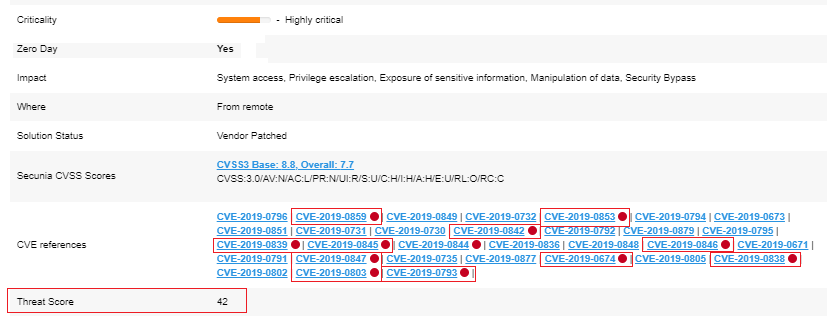
Here is an example of one of the three most critical threats in this resulting list [SA88527]:
Most Prevalent Attack Vector
Attack Vector (AV) vulnerability criteria is very important in terms of the overall expectations of where an attack might occur from. Here we see that half of all reported vulnerabilities could have been exploited remotely by an attacker, who can then hide his online traces better to prevent being tracked.
- 288 advisories reported that attack can occur “From Remote” (60.6%)
- 132 advisories reported that attack can occur “From local network” (28.1%)
- 49 advisories reported that attack can occur from “From Local System” (10.5%)
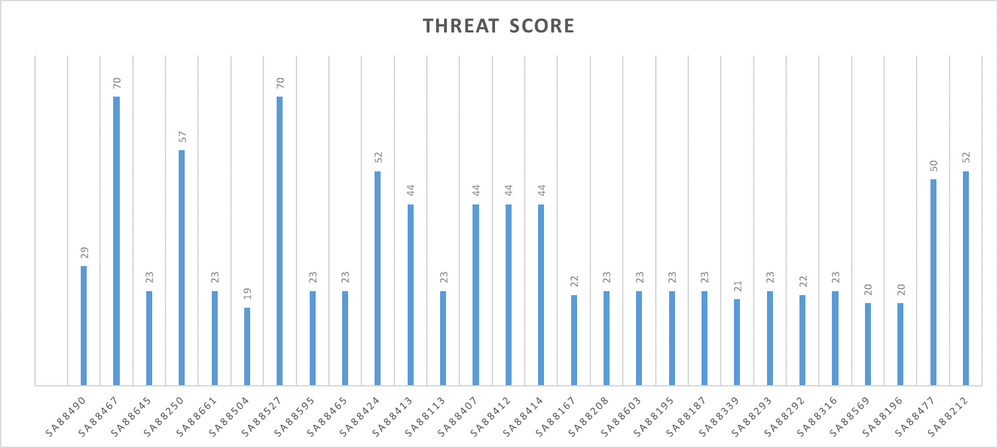
In fact, 52% of the 288 vulnerabilities that enable remote attack have a known threat. That is 32% of all SAIDs, or 150 new advisories. Sorting the 150 remaining ones by criticality rating and Threat Intelligence gives me a list of advisories that require urgent prioritization due to their high threat tags:
Solution Status
The patching phase is critical to the success of every vulnerability management project. The solution status of an SAID gives away the knowledge on what can be done to resolve the vulnerabilities. Here is a helicopter view of the solution statuses included in the totality of the 469 security advisories by Flexera:
- 88.5% of all advisories have “Vendor Patched” solution status;
- 4.8% of all advisories have “No Fix” solution status;
- 5.2% of all advisories have “Partial Fix” solution status
- 2.6% of all advisories have “Workaround” solution status;
- 1 advisory has a solution status of “Unknown”;
Overall Threat Summary
Looking on the surface of our summary, here is what we found out:
- 50%+ of the newly disclosed vulnerabilities reside in the moderate-high ratings range.
- Low-rating vulnerabilities should not be overlooked.
- Nearly 20% of them have a known threat
- 55% of all disclosed vulnerabilities had a known threat as they were publicized. 45% do not.
- 60%+ of all vulnerabilities can be exploited from remote, while 52% of already have a known threat.
- The top 3 most prevalent impacts are found in 323 SAIDs, and 70% of these have known threats.
Nothing is lost even with such quantified impact involved. And 88.5% of the issues have a patch.
Vendor and Product Overview
Let's look at which vendors were vulnerable, and which ones were less secure than others.
Microsoft Windows
Flexera released 14 advisories for Microsoft in this period, with two of them reporting on the only two Zero Day vulnerabilities disclosed in the covered period. Few of the other advisories had high threat score.
Linux Distros
System and kernel vulnerabilities in various Linux distros have been identified in 155 SAIDs. The below list summarizes the total number of advisories issued for each tracked distro. The advisories listed next to the vendor names are the ones that I would suggest to you to verify if these have been handled.
- Ubuntu = 34 SAIDs; [SA88166; SA88415; SA88339; SA88293; SA87652]
- SUSE = 27 SAIDs; [SA88204; SA88292; SA88615; SA88290; SA88212]
- Debian = 15 SAIDs; [SA88252; SA88187; SA88491]
- Gentoo Linux = 24 SAIDs; [SA88113; SA88271; SA88155; SA88556; SA88270]
- Red Hat = 17 SAIDs; [SA88182; SA88775; SA88321; SA88830]
- Amazon Linux = 11 SAIDs; [SA88330; SA88524; SA88509]
- Oracle Linux = 13 SAIDs; [SA88207; SA88206; SA88300; SA88278; SA88451]
- CentOS = 9 SAIDs; [SA88221; SA88217; SA88224; SA88779; SA88539]
- Solaris = 5 SAIDs; [SA88595; SA88526; SA88862; SA88863; SA88577]
Android
There was one advisory for Android that reports on 81 different vulnerabilities. SA88250 included Remote AV; High Threat Score by [+ evidences of exploit and known threats]; Highly Critical rating assigned by Secunia Research; at least 3 different impact types, and it points to secure Vendor Patch.
IT/Asset Management
147 new security advisories identified issues with IBM, Lenovo, Oracle, Siemens, SAP, HP, VMWare, Hitachi, Samba, Nagios XI, QNAP, Synology, Consul, Jetty, ManageEngine, Roundup, Cybozu, TIBCO.
82% of all advisories are with first three vendors in this list, or 121 SAIDs.
Web/Email Management
29 SAIDs identified vulnerabilities with NetApp, Apache, Atlassian, Joomla!, Drupal, WordPress, Horde, Zimbra, Dovecot, DirectAdmin, NextCloud, Contao.
Security Software
Flexera released 22 new SAIDs for security software products by F5, Trend Micro, McAfee, SonicWall, Palo Alto, Elastic, Fortinet, Forcepoint, Symantec, Avecto, and ZoneAlarm.
Commercial Windows Apps
13 SAIDs were attributed vulnerabilities to software products by Adobe, Google, Tableau, Wireshark, Foxit Reader, Waterfox, TeamSpeak, Evernote and SPIP.
Open Source Software
17 new SAIDs are released for FFmpeg, Magento, FreeRADIUs, Clam Anti-Virus, Pacemaker, TensorFlow, Foreman API, MISP, 389 Directory Server, Evince, Nautilus, atftp, and Poppler in this category.
Development Zone
6 new security advisories for GitLab, Jenkins, PHP, Ruby Nokogiri, Symfony add to the overall list.
Networking/Other Platforms
33 new security advisories issued in this period identified vulnerabilities with Cisco IOS, Cacti, ISC BIND, Zyxel, and Juniper OS on the networking side. GOG Galaxy and Blackberry complete this list of vendors.
Other
3 new security advisories for Rockwell Micrologix controllers, WAGO I/O controllers, and Xerox printers complete the software listing in this chapter of my blog.
Most Vulnerable Vendors for April
Here is the top 10 summary of the vendors that have earned most security advisories on their account:
- Oracle
- IBM
- Ubuntu
- SUSE
- Gentoo
- Cisco
- Red Hat
- Debian
- Microsoft
- Lenovo
April’s Prioritization List
We’ve finally arrived at the section where I would want to sum up the data. Industry reports, including Gartner, show that 6-10% of the vulnerabilities disclosed each year actually are exploited in the wild. Here is a list of nearly 6% of all security advisories that required immediate prioritization in April:
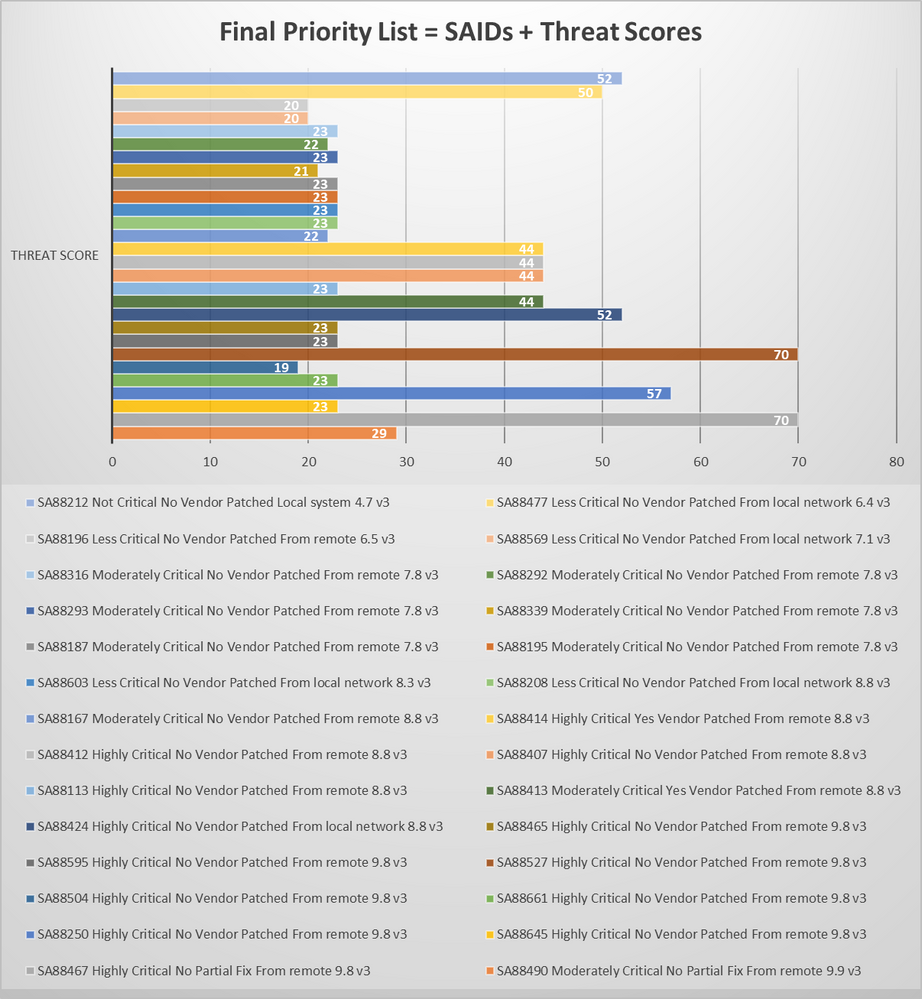
After performing mitigation of the vulnerabilities mentioned in my priority list no . 1, you should look at what other vulnerabilities require prioritization next, as per official security best practices requirements, internal policies for handling security threats and regulatory compliance.
Conclusions
If your software has been mentioned somewhere in my blog, you better patch it fast. Remember that no matter how scary the situation looks overall, 88.5% of the vulnerabilities have a vendor-provided patch.
The problem with big numbers is that they hardly get smaller with limited resources. To avoid dealing with large data volumes in your prioritization approach, a day-by-day software management effort is required to help you split the work into automated vulnerability management tasks that run on a daily basis. You will eventually get ahead of time and the threats that endanger you to achieve much better security.
In order to understand vulnerability threats, one must understand the big picture. In order to effectively prioritize vulnerability threats, one must get familiar with the vendors and the software that pose a threat. The wide applicability of software is certainly a factor, but so is the element of surprise. Vulnerabilities should not be ignored based on their vendor, not even based only on their overall rating.
In our final list, we included threats from less critical to highly critical, as opposed to what many do – patch-only high-criticality ratings. In reality, the vulnerabilities we prioritized have been actively exploited in the past and present. This example shows how important Threat Intelligence is for parallel assessment and detection of ‘insignificant threats’ that pose real critical danger to any organization.
- SVM On-prem November Update in Software Vulnerability Management Release Blog
- Monthly Vulnerability Insights: October 2024 in Software Vulnerability Management Blog
- The file chosen does not have enough information to submit. in Software Vulnerability Management Forum
- Monthly Vulnerability Insights: September 2024 in Software Vulnerability Management Blog
- SVM August 2024 Update in Software Vulnerability Management Release Blog