A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- FlexNet Manager
- :
- FlexNet Manager Knowledge Base
- :
- [FNMS SAML Setup] Troubleshooting guide and list of common errors
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
- Article History
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Checking the error logs
- To enable debug-level logging
- Accessing the logs
- Common errors and possible resolutions
- Inspecting the SAML requests and responses exchanged
- Using StubIdP for testing purposes
This article is a part of a wider topic, see parent page.
Checking the error logs
If you're using FlexNet Manager Suite Cloud, you can provide the Error IDs to Support.
If you are using FlexNet Manager Suite On-premise, you can enable debug-level logging and analyze the error logs yourself.
To enable debug-level logging
- Modify the log level for the following items to "DEBUG" in %programdata%\Flexera Software\Compliance\Logging\WebUI.config file.
- Kentor.AuthServices (default: "WARN")
- Root (default: "INFO")
- Restart IIS.
- Perform the same action that led to the error you encountered before (it will now emit debug-level logging).
Accessing the logs
The WebUI log is accessible in %programdata%\Flexera Software\Compliance\Logging\WebUI\webui.log file.
Most authentication-related errors with SAML begin with a generic error message. The error log details are found at the end of the line. For example, see the full error below:
ManageSoft.Compliance.Security.Sso.SamlCoreException: There is problem while authenticating via SAML. Please make sure (a) that the web.config element 'kentor.authServices' is correctly configured, and (b) that the web server can connect to the configured SAML identity provider (if automatic metadata download is enabled). ---> System.Configuration.ConfigurationErrorsException: Unexpected entity id "https://sts.windows.net/xxx/" found when loading metadata for "https://sts.windows.net/yyy/".
at Kentor.AuthServices.IdentityProvider.ReadMetadata(ExtendedEntityDescriptor metadata)
at Kentor.AuthServices.IdentityProvider.DoLoadMetadata()In the above log, the error log you will be interested in analyzing is:
System.Configuration.ConfigurationErrorsException: Unexpected entity id "https://sts.windows.net/xxx/" found when loading metadata for "https://sts.windows.net/xxx/"
at ...Common errors and possible resolutions
#1 - Operator not being assigned to any role
User hello@flexera.com has no access rights in tenant
Resolution
- Ask your FlexNet Manager Suite administrator to assign you to a role via the web UI.
- If you are the administrator, either assign yourself to the Administrator role via the database or ensure you have the FnmsAdmin claim set to true for only yourself (and not other users who aren’t meant to be granted the administrator role upon first sign-on). If you prefer to do this via database, you can run the following command:
EXEC dbo.GrantOperatorFullAccess 'hello@flexera.com'
#2 - AudienceRestrictionCondition is not valid
Example log
System.IdentityModel.Tokens.AudienceUriValidationFailedException: ID1038: The AudienceRestrictionCondition was not valid because the specified Audience is not present in AudienceUris- Check that the Audience URL configured in the IdP matches your FlexNet Manager Suite URL (for example, https://flexnet.myorganization.com/Suite) or the return URL. Keep in mind that there typically should not be any trailing slash, and the URL is case-sensitive. Don't forget to check if you’re using HTTP vs. HTTPS.
#3 - Invalid service certificates / null reference exception
Example log
System.NullReferenceException: Object reference not set to an instance of an object.
at Kentor.AuthServices.Configuration.ServiceCertificateCollection.InsertItem(Int32 index, ServiceCertificate item)
at Kentor.AuthServices.Configuration.ServiceCertificateElementCollection.RegisterServiceCertificates(SPOptions options)- In your web.config within the kentor.authServices section, remove or comment out service certificates with invalid fileName references.
<serviceCertificates>
<!-- Remove or comment the following: -->
<!-- <add fileName="" /> -->
</serviceCertificates>#4 - No IdP with Entity ID xxx found / unexpected Entity ID found
Example log
System.Collections.Generic.KeyNotFoundException: No Idp with entity id "..." found. ---> System.Collections.Generic.KeyNotFoundException: The given key was not present in the dictionary.
at System.ThrowHelper.ThrowKeyNotFoundException()
OR
System.Configuration.ConfigurationErrorsException: Unexpected entity id "urn:internal:federation:xxx" found when loading metadata for "urn:federation:xxx"- The EntityID you configured in the <identityProviders> section in your web.config is not correct.
- Inspect the SAML response sent by the IdP to see the Entity ID included in the SAML response. Make sure this matches what's set in web.config.
- Verify that the Entity ID set in the IdP is correct and is a valid URL. It doesn’t have to point to an actual location on the web; for example, the Entity ID should be http://okta.com/xxx instead of OKTA_XXX.
- Remember that the Entity ID in the parent <kentor.authServices> is different from the Entity ID in <identityProviders> section. In a typical setup, the former will simply be your FlexNet Manager Suite URL, and the latter will be the Entity ID supplied by your IdP (for example, http://www.okta.com/xxx).
#5 - Failed signature validation
Example log
Kentor.AuthServices.Exceptions.InvalidSignatureException: Message from https://okta.com/xxx failed signature verification
- Verify that the public certificate you configured in SP via the <signingCertificate> section matches the private key of your IdP.
- Verify that the private certificate you configured in SP via the <serviceCertificates> section matches the public key you supplied to your IdP.
#6 - Signature didn't verify or contents tampered
Example log
Kentor.AuthServices.Exceptions.InvalidSignatureException: Signature didn't verify. Have the contents been tampered with?
at Kentor.AuthServices.XmlHelpers.VerifySignature(IEnumerable`1 signingKeys, SignedXml signedXml, XmlElement signatureElement, Boolean validateCertificate)
at Kentor.AuthServices.XmlHelpers.IsSignedByAny(XmlElement xmlElement, IEnumerable`1 signingKeys, Boolean validateCertificate, String minimumSigningAlgorithm)
at Kentor.AuthServices.Saml2P.Saml2Response.ValidateSignature(IOptions options)- Verify that the public certificate you configured in SP via <signingCertificate>> section matches the private key of your IdP.
- Ensure there is no extra spacing, formatting, or invisible characters in the public certificate you provided or in the SAML responses being received by your IdP.
#7 - The signature verified correctly but that key is not trusted
Example log
Kentor.AuthServices.Exceptions.InvalidSignatureException: The signature verified correctly with the key contained in the signature, but that key is not trusted.- Verify that the public key provided by your IdP team. This is the one you configured within the <signingCertificate> section in web.config.
- If the metadata contains the same public key, does it have different contents than the one you configured within the <signingCertificate> section in web.config?
- Talk to your IDP team about whether the certificate they provided is correct for the SP you are configuring. There are cases where your IdP team may have different environments (for example, staging.myidp.com and prod.myidp.com). If that is the case, check if your IdP team provided you with the public key for the correct environment.
#8 - Signed AuthenticateRequests expected but no service certificates are configured
Example log
System.Configuration.ConfigurationErrorsException: Idp "http://www.okta.com/xxx" is configured for signed AuthenticateRequests, but ServiceCertificates configuration contains no certificate with usage "Signing" or "Both". To resolve this issue you can a) add a service certificate with usage "Signing" or "Both" (default if not specified is "Both") or b) Set the AuthenticateRequestSigningBehavior configuration property to "Never".- In a typical setup, you can set AuthenticateRequestSigningBehavior to Never in the web.config file.
- In an advanced setup, if you prefer to set up service certificates (required for SLO/assertion encryption), then set AuthenticateRequestSigningBehavior to Always and specify a valid certificate within the <serviceCertificates> section.
#9 - Unable to load certificate file
Example log:
System.Security.Cryptography.CryptographicException: The system cannot find the file specified.
at System.Security.Cryptography.CryptographicException.ThrowCryptographicException(Int32 hr)
at System.Security.Cryptography.X509Certificates.X509Utils._QueryCertFileType(String fileName)
at System.Security.Cryptography.X509Certificates.X509Certificate.LoadCertificateFromFile(String fileName, Object password, X509KeyStorageFlags keyStorageFlags)- This error indicates that the certificate you specified either in <signingCertificate> or <serviceCertificates> can’t be found. Check the certificate path you specified either via the file path or reference the Certificate Store path.
#10 - A unique match to certificate path is required
Example log:
System.InvalidOperationException: Finding cert through FindBySubjectName in LocalMachine:My with value flexnet.myorganization.com matched 2 certificates. A unique match is required.- Modify the store certificate path in web.config to use different find mechanisms that will result in one certificate being found. For example, you can change findType to FindByThumbprint or FindBySerialNumber.
- Use another certificate with a unique subject name.
- Proceed with caution: delete the duplicate certificates that are not relevant from the Certificate Store.
#11 - Cannot verify signature of message from unknown sender
Example log
Kentor.AuthServices.Exceptions.InvalidSignatureException: Cannot verify signature of message from unknown sender https://localhost:44300/Metadata- Verify the Entity ID set in the <identityProviders> section of web.config. Ensure it matches the Entity ID supplied by your IdP (or in the SAML response).
#12 - IdP returns status AuthnFailed
Example log
Kentor.AuthServices.Exceptions.UnsuccessfulSamlOperationException: Idp returned status "AuthnFailed", indicating that the single logout failed. The local session has been successfully terminated.- This error means that your IdP is unable to authenticate you, which could be for various reasons. Talk to your IdP team or IdP vendor to get the relevant logs. In Okta, you can view the logs by going to Okta admin page (classic UI) > FlexNet Manager Suite On-premise > View logs.
- Some possible logs might be:
- Malformed request: Check the SAML request sent to the IdP (refer to the "How you can inspect SAML requests/responses exchanged" section).
- Issuer does not match: The certificate issuer you configured in the <serviceCertificates> section may not match the issuer you configured in the IdP.
- Invalid signature: The IdP is not able to verify the signature of your signed SAML requests, and you should check the private certificate you configured in <serviceCertificates> section in web.config and compare it to the corresponding public key you uploaded/provided to your IdP.
- Unauthorized: Check the user permission in the IdP and whether the user is correctly assigned to the SAML application, the user is not suspended, etc.
#13 - Invalid provider type specified
Example log
System.Security.Cryptography.CryptographicException: Invalid provider type specified.- If you generated a self-signed certificate and/or you are configuring the <serviceCertificates> section, this error may occur because the certificate wasn't generated using the correct API. For example, if you used PowerShell's New-SelfSignedCertificate command, you may need to specify -KeySpec KeyExchange when generating the self-signed certificate.
#14 - Received message contains unexpected InResponseTo
Example log
Kentor.AuthServices.Exceptions.UnexpectedInResponseToException: Received message contains unexpected InResponseTo "id58c95ac8acce4ccd85826688510f5129". No cookie preserving state from the request was found so the message was not expected to have an InResponseTo attribute. This error typically occurs if the cookie set when doing SP-initiated sign on have been lost.- Ensure cookies are enabled in the browser.
- Clear all cookies from your browser (or try in browser private/incognito mode).
- If you have a load-balancing farm, you need to synchronize the machine key. Otherwise, one server won't be able to encrypt cookies set by another server.
#15 - Unable to connect to remote server/operation time out when loading Metadata URL
Example log
Unable to connect to the remote server ---> System.Net.Sockets.SocketException: No connection could be made because the target machine actively refused it 127.0.0.1:44300
...
at System.Net.WebClient.OpenRead(Uri address)
at Kentor.AuthServices.Metadata.MetadataLoader.Load(String metadataLocation)
OR
System.Net.WebException: The operation has timed out
at System.Net.WebClient.OpenRead(Uri address)
at Kentor.AuthServices.Metadata.MetadataLoader.Load(String metadataLocation)- This can happen when you set metadataLocation as metadata URL in the web.config.
- Ensure your SP can download the specified metadata URL. Try accessing the metadata URL manually from a browser in FlexNet Manager Suite server.
#16 - SAML operation cannot be processed because it is not signed
Example log
Kentor.AuthServices.Exceptions.UnsuccessfulSamlOperationException: Received a LogoutResponse from http://localhost:44300/8a9c3d9f-3228-4d96-9c69-00000000/Metadata that cannot be processed because it is not signed.- Some SAML operations, such as SLO, require signed requests. For example, your SP cannot trust an IdP-initiated SLO if the saml2p;LogoutRequest sent by the IdP is not signed. To resolve this, talk to your IdP team and ensure these requests are signed so the SP can trust them.
#17 - No Saml2 Response found
Example log
Kentor.AuthServices.Exceptions.NoSamlResponseFoundException: No Saml2 Response found in the http request.
at Kentor.AuthServices.WebSso.AcsCommand.Run(HttpRequestData request, IOptions options)- Verify the Assertion Consumer Service (ACS) URL is set correctly. It should be: https://myorganization.flexera.com/Suite/AuthServices/Acs.
#18 - Invalid account: please enter a valid email address (FlexNet Manager Suite Cloud)
Example log
ManageSoft.Compliance.Security.Sso.SamlCoreException: Invalid account: please enter a valid email address.
at Flexera.Web.Presentation.Security.SingleSignOnTenantSaml.ValidateIdentityUsername(String username)- Inspect the Name ID supplied in the SAML response. If you set a custom authenticationLogin value in web.config, like OperatorLogin, then inspect the attribute value supplied in the SAML response.
- The Name ID/operator identifier must be a valid email address.
#19 - The SAML Response is not signed and contains unsigned Assertions
Example log
Kentor.AuthServices.Exceptions.Saml2ResponseFailedValidationException: The SAML Response is not signed and contains unsigned Assertions. Response cannot be trusted.
at Kentor.AuthServices.Saml2P.Saml2Response.ValidateSignature(IOptions options)- Ensure the SAML response returned by your IdP is signed.
- Alternatively, set WantAuthnRequestsSigned to false in your metadata file, like below:
<EntityDescriptor entityID="..." ...>
<IDPSSODescriptor WantAuthnRequestsSigned="false" ...>.../IDPSSODescriptor>
</EntityDescriptor>#20 - SP timeout/SessionNotOnOrAfter value is out of range
Example log
System.ArgumentOutOfRangeException: Specified argument was out of the range of valid values.
Parameter name: validFrom
at System.IdentityModel.Tokens.SessionSecurityToken..ctor(ClaimsPrincipal claimsPrincipal, UniqueId contextId, String id, String context, Byte[] key, String endpointId, Nullable`1 validFrom, Nullable`1 validTo, UniqueId keyGeneration, Nullable`1 keyEffectiveTime, Nullable`1 keyExpirationTime, SctAuthorizationPolicy sctAuthorizationPolicy, Uri securityContextSecurityTokenWrapperSecureConversationVersion)
at System.IdentityModel.Tokens.SessionSecurityToken..ctor(ClaimsPrincipal claimsPrincipal, UniqueId contextId, String context, String endpointId, Nullable`1 validFrom, Nullable`1 validTo, SymmetricSecurityKey key)
at System.IdentityModel.Tokens.SessionSecurityToken..ctor(ClaimsPrincipal claimsPrincipal, String context, Nullable`1 validFrom, Nullable`1 validTo)
at Kentor.AuthServices.HttpModule.CommandResultHttpExtension.SignInOrOutSessionAuthenticationModule(CommandResult commandResult)- First, inspect the SAML response to determine if the SessionNotOnOrAfter attribute is provided. This attribute controls the SP session's lifetime before it has to re-authenticate with the IdP.
- If not, it will default to the UTC current date + timeout value configured. The timeout value configured is the default session lifetime configured in FlexNet Manager Suite/IIS. Alternatively, from 2020 R1 onward, the default timeout will be retrieved from the LoginTimeoutMinutes value in the compliance tenant setting.
- If the value calculated from the previous step is an earlier date/time than the current UTC date, then you’ll receive the error.
Resolution
- Ensure SessionNotOnOrAfter provided is in UTC time and is not earlier than the current UTC time.
- Applicable to 2020 R1 onward: ensure LoginTimeoutMinutes set in the database is not a negative value.
#21 - Provided certificate is not valid because it does not contain a private key
This means that the certificate you configured in <serviceCertificates> section in web.config does not contain a private key to sign outgoing SAML requests from SP to the IdP.
Resolution
- If you specified a store reference path, don't add it to the CA where the private key can't be stored.
Inspecting the SAML requests and responses exchanged
You can open the use developer tools in your browser and view the Networks tab while trying to log in via SAML. You may also need to check the Preserve Log option. Once you have done this, when performing SSO via SAML, you’ll be able to see all the HTTP requests happening in the background. These HTTP requests will contain the SAML requests and responses exchanged between the Idp and SP.
To make things simpler, you can use any SAML message decoder plugin of your choice to easily inspect the SAML requests/responses exchanged.
Some ideas on what to inspect:
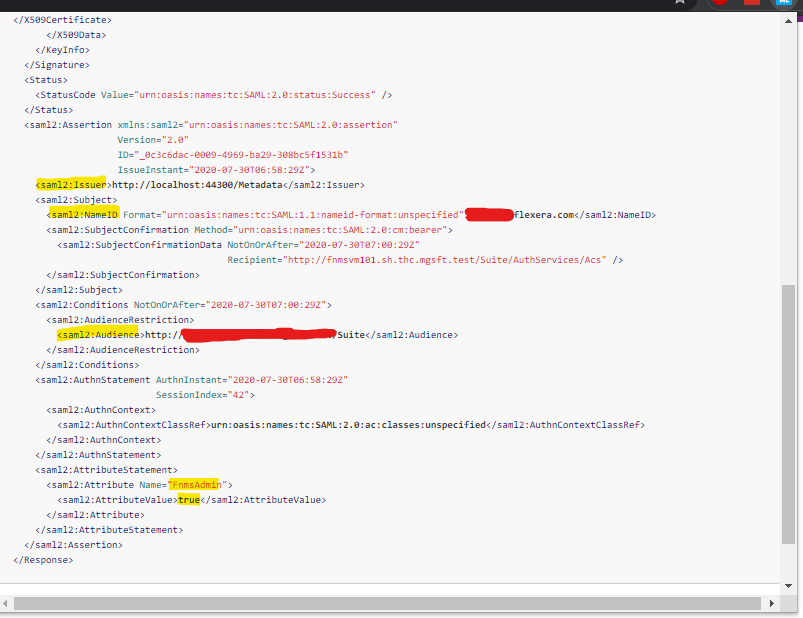
- If you get an error relating to the Name ID being an unexpected format, inspect the Name ID in the SAML response.
- If you are wondering why operator details are not populated correctly (refer to attributes supported), inspect the attribute in the SAML response.
Sample SAML request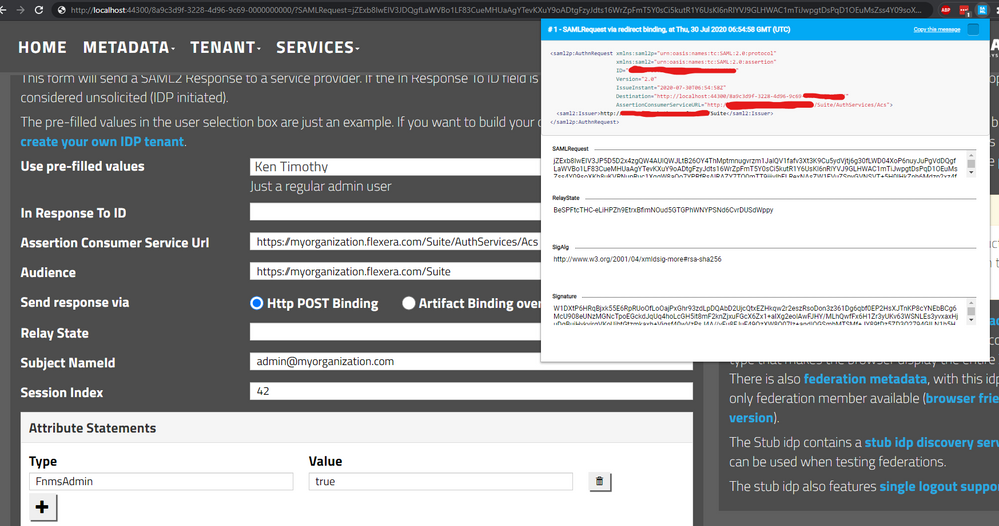
Sample SAML response
Information you may be interested in is highlighted in yellow below.
Using StubIdP for testing purposes
Important notes:
- Never configure your FlexNet Manager Suite production environment with StubIdp.
- It’s highly recommended that you disable network access to the FlexNet Manager Suite system so that only you can access it.
- Ignoring the above warnings can lead to people gaining unauthorized access to your system, as you will be using StubIdP, which is essentially a mock IDP that allows you to impersonate any identity without needing any credentials.
If you are a FlexNet Manager Suite administrator and want to test run the configuration prior to engaging with your IdP team, or you have been in back-and-forth discussions with your IdP team and the configuration just doesn't seem right, then using StubIdp might be the right choice for you.
- Go to https://stubidp.sustainsys.com/
- Create your own tenant by going to StubIdp homepage > select Create your own IdP tenant. You will get a unique URL similar to https://stubidp.sustainsys.com/1506e6c0-d2b0-49e8-919a-00000000000. Replace any reference to this URL with your own in the proceeding steps.
- Fill in the following details to automatically pre-fill the Assertion Consumer Service URL, Audience URL, predefined users, and Attribute Statements:
{
"HideDetails": false,
"UserList": [
{
"DisplayName": "Admin User",
"Description": "A user who will be granted Administrator rights upon first login",
"Assertion": {
"NameId": "admin@myorganization.com",
"AttributeStatements": [
{
"Type": "FnmsAdmin",
"Value": "true"
}
]
}
}
],
"DefaultAssertionConsumerServiceUrl": "https://myorganization.flexera.com/Suite/AuthServices/Acs",
"DefaultAudience": "https://myorganization.flexera.com/Suite",
"IdpDescription": "FlexNet StubIdP - testing only"
}- The above snippet includes what you should enter for the Assertion Consumer Service URL, Audience URL, etc. Alternatively, refer to the parent article for specific IdP configuration guides.
- You can download the metadata file from https://stubidp.sustainsys.com/1506e6c0-d2b0-49e8-919a-00000000000/Metadata and rename it to metadata.xml.
- You can download the IdP public certificate from https://stubidp.sustainsys.com/1506e6c0-d2b0-49e8-919a-00000000000/Certificate.
- In your web.config, refer to the previous section about supplying metadata and other relevant information in your FlexNet Manager Suite system. In web.config, you will see something similar to the below.
<kentor.authServices entityId="https://flexnet.myorganization.com/Suite" returnUrl="https://flexnet.myorganization.com/Suite/AuthServices" authenticateRequestSigningBehavior="Never">
<identityProviders>
<add entityId="https://stubidp.sustainsys.com/1506e6c0-d2b0-49e8-919a-00000000000/Metadata" signOnUrl="https://stubidp.sustainsys.com/1506e6c0-d2b0-49e8-919a-00000000000" allowUnsolicitedAuthnResponse="true" binding="HttpRedirect" loadMetadata="true" metadataLocation="~/App_Data/metadata.xml">
<signingCertificate fileName="~/App_Data/stubidp.sustainsys.com.cer" />
</add>
</identityProviders>
<serviceCertificates>
<!-- Not needed in typical setup unless you want to configure SLO. -->
<!--<add storeName="My" storeLocation="LocalMachine" x509FindType="FindBySubjectName" findValue="flexnet.myorganization.com" use="Signing" />-->
</serviceCertificates>
</kentor.authServices>- When you reach the FlexNet Manager Suite URL, you’ll be redirected to StubIdP where you can choose to impersonate any user. If you use the predefined values above, you should see Admin User in the dropdown. Select any user, then select the Login button.
- If that works successfully, you can be sure that you’ve configured SAML successfully in FlexNet Manager Suite, and you can provide the relevant values below for your IdP team to create the actual SAML application you will be using in your production environment:
-
- Assertion Consumer Service URL
- Audience URL
- The expected Name ID value (typically email address)
- Optionally, any attribute statements they should pass along to FlexNet Manager Suite
- Have them provide the IdP X.509 public certificate so you can configure them in the signingCertificate section in web.config file above
on
Aug 07, 2020
03:00 AM
- edited on
Jun 13, 2024
03:50 PM
by
![]() HollyM
HollyM
![]()
- Mark as Read
- Mark as New
- Permalink
- Report Inappropriate Content
@kent-au Thanks a lot for the detailed article , this very much useful and simpler to follow.
By the way, i was testing the SSO in one of my customer premise where i have observed that once the SAML authentication is started from the Okta, the site is just freezes at below URL.
https://xxx.oktapreview.com/app/xxx_flexnetmanagersuite_1/xxx/sso/saml
when checked in SAML tracer , it is stuck at the below step .
GET https://flexnet.myorganization.com/Suite/AuthServices
But when i reload the page, it is going to /suite .
Note : the mentioned issue is reported in new each login from Okta to FNMS .
- Mark as Read
- Mark as New
- Permalink
- Report Inappropriate Content
Hi @emtmeta,
What SSO/recipient/destination URLs do you have configured in Okta? From what it sounds, there might be an issue with the redirect URL configured in Okta.
For Okta configuration guide, see https://community.flexera.com/t5/FlexNet-Manager-Knowledge-Base/FNMS-SAML-Setup-Okta-configuration-guide-to-enable-SSO-SAML-in/ta-p/157729
For WebUI side of the configuration, see https://community.flexera.com/t5/FlexNet-Manager-Knowledge-Base/FNMS-SAML-Setup-WebUI-configuration-guide-to-enable-SSO-SAML-in/ta-p/157804
Also, is the behavior you are describing consistent across different browsers and devices?
Cheers, Kent
- Mark as Read
- Mark as New
- Permalink
- Report Inappropriate Content
Thanks a lot for the feedback.
I had a detailed troubleshooting and did some changed returnUrl in the web.config file as follows
Old Value : returnUrl="https://flexnet.myorganization.com/Suite/AuthServices"
New Value : returnUrl="https://flexnet.myorganization.com/Suite/"
When i removed authServices from the URL, the reported issue is no longer observed.
is this right practice ?
Regards,
Junaid Vengadan
- Mark as Read
- Mark as New
- Permalink
- Report Inappropriate Content
Hi @emtmeta,
I can't say for certain but I remember seeing similar configuration for 'returnUrl' i.e. without /AuthServices. That should be completely fine as long as authentication flow works as expected for both IdP and SP initiated SSO.
Cheers, Kent
