The Community is now in read-only mode to prepare for the launch of the new Flexera Community. During this time, you will be unable to register, log in, or access customer resources. Click here for more information.

- Flexera Community
- :
- FlexNet Manager
- :
- FlexNet Manager Knowledge Base
- :
- 403 error when using SAML authentication through ADFS
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Article History
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
Symptoms
FNMS Cloud returns a 403 HTTP error when using SAML authentication using ADFS as the identity provider.
Cause
This issue is due to the name ID isn't mapping in ADFS.
Resolution
To resolve the issue, please follow the detailed steps in the attachment 'ADFS FNMS SAML 2.0 configuration.docx'.
Feb 20, 2019 03:10 AM - edited Jun 03, 2020 08:43 AM
More than troubleshooting It was indeed a well explained article on SSO enablement as well.
I have doubt here , can we have SP initiated authentication as well with adfs and fnms ?
Because i have a client were we did the integration with adfs where the IdP initiated authentication is working , but SP initiated is not working .
Regards,
Junaid Vengadan
Hi @emtmeta, can you provide more details as to how "SP-initiated (workflow) is not working"? Does it lead to an error page, for example?
If it leads to an error page: can we get the error logs related to the request and then refer to this troubleshooting page? https://community.flexera.com/t5/FlexNet-Manager-Knowledge-Base/FNMS-SAML-Setup-Troubleshooting-guide-and-list-of-common-errors/ta-p/157810
If FNMS does not redirect to the IdP and instead to Flexera/AGW login page: is your intention perhaps to change the "Active Identity Providers" set in FNMS Web UI > System Settings > Security?
Cheers, kent
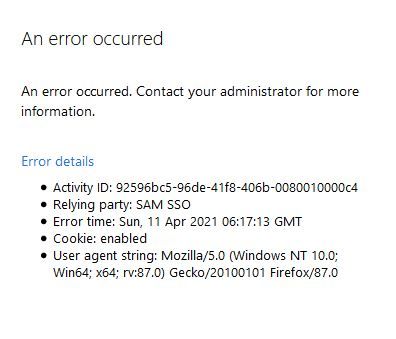
@kent-au , yeah i'm getting the error from SP initiated authentication, but the error is not at FNMS side , it is in adfs side (the flow was as follows )
- Logging to SAM portal (/suite)
- The FNMS is redirecting the authentication to adfs
- User is providing the user credential at adfs sso page
- The ADFS is forwarding the request back to FNMS (with auth string - as URL) , but it is failing before reaching FNMS with following error.
An error occurred contact your administrator for information (error screen attached)
@emtmeta we will need to check the logs for the given Activity ID you posted above in the IdP then. Hopefully that's gonna give us an idea what's wrong and how we can fix that.
Some of the IdP errors I have encountered before (albeit for a different IdP) includes:
- invalid signature / issuer does not match (common issue) - check the service provider public key configured in the IdP and whether it matches the Service Provider private key configured in the metadata that FNMS uses to sign outgoing requests to the IdP
- unauthorized - does the user you log in to have permission to access FNMS app?
Can you get the logs and copy them here?
@kent-au , i'm waiting for the ADFS side logs for the mentioned activity .
Meantime i got the WEBUI log in debug mode , and found the below
[DEBUG 2021-04-28 09:01:31,492 449010ms AuthServices ] Expanded AuthServicesUrl
AssertionConsumerServiceUrl: https://sam.SERVERNAME.com/Suite/AuthServices/Acs
SignInUrl: https://sam.SERVERNAME.com/Suite/AuthServices/SignIn
LogoutUrl: https://sam.SERVERNAME.com/Suite/AuthServices/Logout
ApplicationUrl: https://sam.SERVERNAME.com/Suite/
[DEBUG 2021-04-28 09:01:31,492 449010ms AuthServices ] No specific idp requested and no Discovery Service configured. Falling back to use configured default Idp http://stsnew.SERVERNAME.com/adfs/services/trust
[INFO 2021-04-28 09:01:31,492 449010ms AuthServices ] Initiating login to http://stsnew.SERVERNAME.com/adfs/services/trust
Please let me know if that is something to do with Signout URL , the one that i have not updated in WEBUI as of now .
Regards,
Junaid Vengadan
Below are the error from IDP side
Encountered error during federation passive request.
Additional Data
Protocol Name:
Saml
Relying Party:
https://sam.SERVER_NAME.com/Suite
Exception details:
Microsoft.IdentityServer.Service.Policy.PolicyServer.Engine.AssertionConsumerServiceUrlDoesNotMatchPolicyException: MSIS3200: No AssertionConsumerService is configured on the relying party trust 'https://sam.SERVER_NAME.com/Suite' that is a prefix match of the AssertionConsumerService URL 'https://sam.SERVER_NAME.com/Suite/AuthServices/Acs' specified by the request.
at Microsoft.IdentityServer.Service.SamlProtocol.EndpointResolver.LookupAssertionConsumerServiceByUrl(Collection`1 assertionConsumerServices, Uri requestedAssertionConsumerServiceUrl, String scopeIdentity)
at Microsoft.IdentityServer.Service.SamlProtocol.EndpointResolver.FindSamlResponseEndpointForAuthenticationRequest(Boolean artifactEnabled, AuthenticationRequest request, ScopeDescription scopeDescription)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolManager.GetResponseEndpointFromRequest(SamlRequest request, Boolean isUrlTranslationNeeded, ScopeDescription scope)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolManager.Issue(HttpSamlRequestMessage httpSamlRequestMessage, SecurityTokenElement onBehalfOf, String sessionState, String relayState, String& newSamlSession, String& samlpAuthenticationProvider, Boolean isUrlTranslationNeeded, WrappedHttpListenerContext context, Boolean isKmsiRequested)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.RequestBearerToken(WrappedHttpListenerContext context, HttpSamlRequestMessage httpSamlRequest, SecurityTokenElement onBehalfOf, String relyingPartyIdentifier, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired, String& samlpSessionState, String& samlpAuthenticationProvider)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSerializedToken(HttpSamlRequestMessage httpSamlRequest, WrappedHttpListenerContext context, String relyingPartyIdentifier, SecurityTokenElement signOnTokenElement, Boolean isKmsiRequested, Boolean isApplicationProxyTokenRequired)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.BuildSignInResponseCoreWithSecurityToken(SamlSignInContext context, SecurityToken securityToken, SecurityToken deviceSecurityToken)
at Microsoft.IdentityServer.Web.Protocols.Saml.SamlProtocolHandler.Process(ProtocolContext context)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.ProcessProtocolRequest(ProtocolContext protocolContext, PassiveProtocolHandler protocolHandler)
at Microsoft.IdentityServer.Web.PassiveProtocolListener.OnGetContext(WrappedHttpListenerContext context)
@kent-au
By tracing the error "Microsoft.IdentityServer.Service.Policy.PolicyServer.Engine.AssertionConsumerServiceUrlDoesNotMatchPolicyException: MSIS3200: No AssertionConsumerService is configured on the relying party trust 'https://sam.SERVER_NAME.com/Suite' that is a prefix match of the AssertionConsumerService URL 'https://sam.SERVER_NAME.com/Suite/AuthServices/Acs' specified by the request."
I have found similar case (http://www.gunnalag.com/2015/09/30/saml-and-active-directory-federation-services-adfs-integration-errors-events-possible-causes-and-fixes/ ) which suggest to create or update the consume URL .
Do you think this will be a right move ?
Hi @emtmeta, did you change the Assertion Consumer Service (ACS) URL to be the actual FNMS URL for your organization, which for FNMS Cloud will be something like https://my-subdomain.flexnetmanager.com/Suite/AuthServices/Acs? The error seems to be indicating it's trying to access a placeholder URL instead i.e. https://sam.SERVER_NAME.com/Suite/AuthServices/Acs
For IdP configuration side of things, you may find the Okta configuration guide to be a helpful reference. While it won't exactly be the same, the configuration should be pretty similar.
Okta IdP configuration guide - https://community.flexera.com/t5/FlexNet-Manager-Knowledge-Base/FNMS-SAML-Setup-Okta-configuration-guide-to-enable-SSO-SAML-in/ta-p/157729
If you still face issues, please post screenshots of your ADFS configuration including the ACS URL being set, tho just remember to mask any details which might be sensitive.
---
Also just noting that all the above articles I linked are sub-pages of this page we have in the community:
SSO SAML Configuration Guide - https://community.flexera.com/t5/FlexNet-Manager-Knowledge-Base/Ultimate-SSO-SAML-configuration-guide-in-FlexNet-Manager-Suite/ta-p/157608
Cheers, Kent