A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Forum
- :
- [Update: Please Use Ideas Portal Beginning December 2020] We Still Want Your Ideas about Software Vu...
- Subscribe to RSS Feed
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Subscribe
- Mute
- Printer Friendly Page
[Update: Please Use Ideas Portal Beginning December 2020] We Still Want Your Ideas about Software Vulnerability Management Products!
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
[IMPORTANT UPDATE: 9 December 2020] Great news - Our Flexera customer and partner community now have a direct opportunity to share ideas and participate in future feature planning. Learn more and add your ideas via the Ideas Portal moving forward. Please note if you have added an idea to this discussion, we will migrate the idea to the new portal and notify you once it's been done. Thank you to everyone for active participation!
---------------------------------------------
You may notice that we don’t currently have a replacement for the Ideas functionality here in the new community. This is temporary-- we are planning to launch ideation as a feature of this new community later this summer. In the meantime, please this discussion forum to continue to provide product feedback on Software Vulnerability Manager (SVM) and Software Vulnerability Research (SVR). Please don’t worry about reposting ideas you may have previously submitted; when the ideation capability is reintroduced here it will include any feedback you may have previously provided.
Apr 04, 2019 08:40 AM - last edited on Dec 09, 2020 02:42 PM by KPBussey
- Labels:
-
Idea
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Please consider this as an option very much wanted.
Sep 18, 2019 07:11 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I am bring back the SUSE question as more customers are moving from RH to SUSE due to the license changes from RH.
I find it rather strange to say you support SUSE but not have a packaged agent for a supported OS.
In any case, if it is not too much work as you mentioned, maybe is time to expedite the creation of such package.
with kind regards
Yiannis Kanellopoulos
Nov 21, 2019 10:07 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Dear Bob,
Our customer is looking to export dashboard as pdf report for management. But they are not able to pull down from SVM on-premise. This is very important requirement to have. As this customer has moved from cloud to on-premise, they are furiously looking to have this.
Please help with this.
Fawad Laiq
Sep 09, 2019 03:35 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Sep 18, 2019 12:58 PM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
Thanks for the response.
It's an important feature and many customers ask for this. Please if you can try to raise this with team and get this in next release. Thanks in advance.
Fawad Laiq
Sep 22, 2019 04:28 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
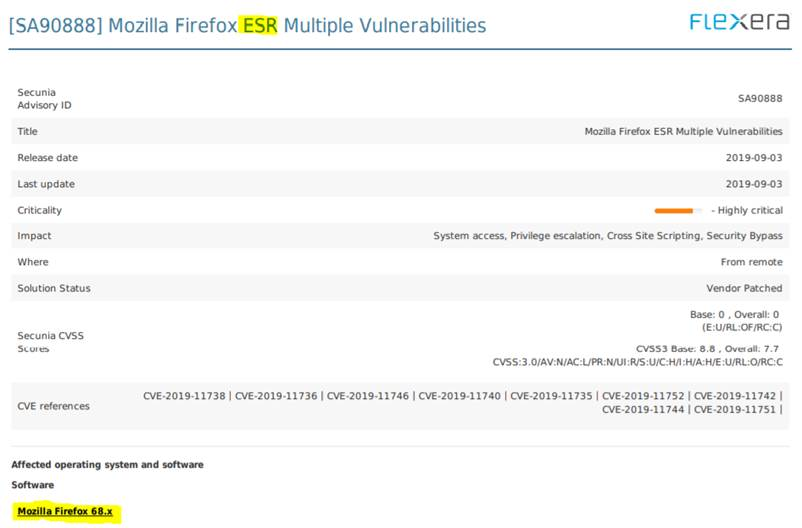
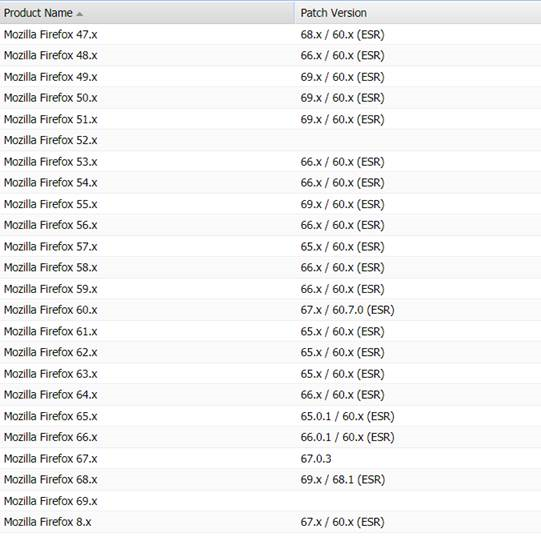
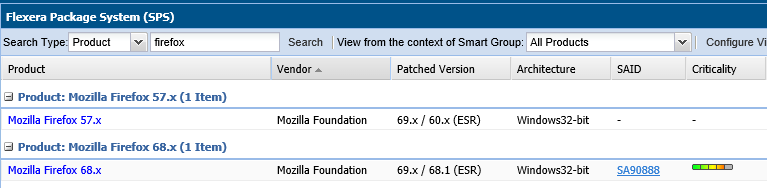
It would be great If svm was able to differentiate between Mozilla Firefox and Firefox ESR.
The Firefox ESR versions are not identical to their normal/free application, and when we are getting vulnerabilities on ESR it gets reported like this
When we look in the Secunia Prod CSI console, it looks like this
We then talked to the product owner who told us that they does not have any Mozilla Firefox ESR versions installed, and that they are using the free version from Mozilla. This makes it look like that Flexera cannot differentiate/determine on which version of Firefox the vulnerability is belonging to. I don’t know if it has something to do with the specific path/exe file Flexera are searching for, but we need to find a way to get the scanning results segmented into two separate products; Mozilla Firefox and Mozilla Firefox ESR.
Oct 28, 2019 07:07 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
First the good news: Research does differentiate when posting advisories (for example see SA91680 (ESR) and SA89514 (Stable)). However, when it comes to detecting the difference during assessment, we cannot do so today since the files for both are identical. As a result, we just detect it as Mozilla Firefox. Fortunately, our Mozilla Firefox SPS patch actually includes both installers, and automatically selects the correct installer to use, based on information read from a text file on the end-point.
Thank you for bringing it up, we are planning improvements to how we go about detection in the future and we'll include Firefox ESR as a great example to help test our ability to handle edge cases like this.
Nov 01, 2019 08:33 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
I'd like to see Flexera implement role-based access that determines which machines a user can see. SVM knows all the vulnerabilities of all the machines in our enterprise; least privilege would dictate that users can only see machines they're responsible for.
Nov 01, 2019 09:15 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Nov 01, 2019 09:33 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We're using SVM Cloud.
Nov 01, 2019 09:37 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
That is okay; as root admin, you can create partitions in SVM Cloud. If you don't see the option, please open a ticket to have it enabled for your account as it is a capability controlled by your license and so may need to be turned on.
Nov 01, 2019 09:54 AM - edited Nov 01, 2019 09:59 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
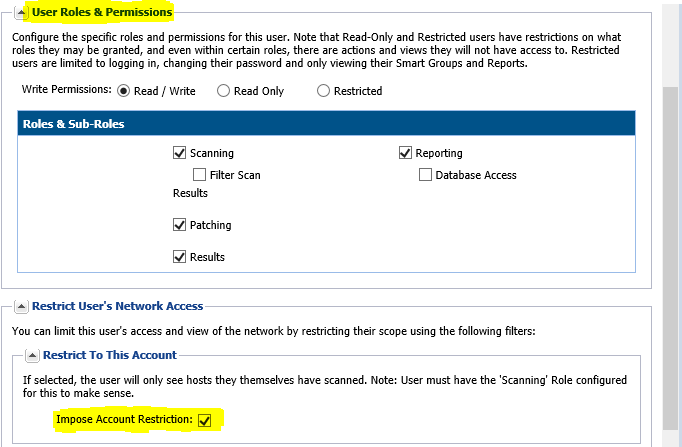
If you're not the root account, but you have an administrator account, you don't want to split the reporting between two databases (totally isolated between partition 1 and 2), but you want only users to be limited with reporting and visibility while the root has oversight of all sub-accounts and data, then you can set up a sub-user account with "Impose to this account" setting enabled.
Once you have logged in, downloaded and deployed Agent from this account to other selected systems that belong to this asset owner, the account will only see and be able to manage those systems and no other. Just make sure to never enable "Database Access" for those.
I thought I would share this as a second workaround.
Rosen
"To understand where a system breaks, one should think like the person who built it"
Nov 01, 2019 11:34 AM - edited Nov 01, 2019 11:35 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
HI,
we would like to be able to use the smart groups for hosts and product Dynamic. At the moment all is static. The pain is e. g. if you want to create a host smart group with only host name like AB-*. You need to search and then go like in our environment through 300 tabs to select each object manual. This process takes ages instead of select all button which is missing.
The problem then apply on top where a new device come in and wasn't selected the smart group is static. We have to go in and add missing devices manual again. That is not really practicable.
The same applies to smart groups for products. We have a few with e. g. "Adobe*" or "Google*", (Cisco*). If anybody install a new product which match this criteria we need to edit the smart group.
Regards
Lukas
Nov 08, 2019 03:22 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Great feedback, thanks. The need to be able to base smart groups on device name (starts with, contains) is already on our radar, but thanks for helping to highlight it and adding the need for similar on product names.
Nov 15, 2019 03:02 PM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Hi,
we have the issue that we can't get all software added in suggested software. This is most of the time for apps which use the Microsoft VSTO technology. This is either deployed to per user or per device. This products also contain security related DLL's which can become unsecure.
The problem is those apps normally does not have any *.exe. They only have DLL (which are not unique to the product and owned by e. g. Microsoft, Oracle or whatever vendor). The scan detection of *.vsto files on the system isn't supported by SVM. The app is installed in add/remove programs, loaded to all users and we can't get this scanned added to the database.
The other options we have is with vendors which are not properly filling in the metadata on the *.exe executed by users. If information are missing it can't be scanned or added to sugguested software. The same apply like above with the dll files. They are not unique for this product and this way can't be used as scan baseline to detect it.
It would be great if the scan engine could have other logical support features to overcome such product issues as well.
Regards
Lukas
Nov 08, 2019 03:27 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Should be able to scan, detect and report vulnerabilities in MS APP-V or VMware Thinapp S/w Packages.
Nov 13, 2019 08:56 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are working to offer a more inventory based option in the future. For now, we can cover most products effectively as we can detect and evaluate not just EXE files but DLL and OCX files as well.
Nov 15, 2019 03:29 PM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have the problem that this described Office 365 Changes are for our usage not helpful.
The issue is that SVM combine the whole suite or each product like Excel in one large set. This way. I end up to see for example
Excel 2019 /Office 365 with secure/unsecure / EOL. That view is really miss leading. There a few factors which are missing here.
1. Microsoft have four channels Monthly, Semi-Annual, Semi-Annual Targeted, Inside Program.
docs.microsoft.com/en-gb/officeupdates/update-history-office365-proplus-by-date
That way I see one large view of Office 365. In our company we have sets of users on different channels. This way each channel is for us technically an own "product" as it delivers other functionality/updates in each.
2. Microsoft have inside of the channels Versions like in in Semi-Annual 1808 + 1902 are in support. We have early adaptors and then are on 1902 and majority e. g. on 1808. The issue is then again like above one large set together combined.
What I have todo today to get a real view of our estate. I have to export each product into Excel. Then go to MS page, filter by version number which product is which channel assigned. Then inside channel see which is secure/non secure. Post that create manual dashboards to make it visible to Management which channels/versions are secure or not globally in our environment.
This is a lot of work. We have then to check in our SCCM/WSUS why xy device wasn't patched. But due of the different combinations been in one "pocket" combined the date are at the end not usefull for us today as we have heavy to manipulate them to get out of SVM what we want =
- each channel and version of product secure/non secure/EOL
Lukas
Nov 12, 2019 10:26 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We have similar issue then with Office. Microsoft offers different servicing channels with Window 10. Then inside of this channels like "Win10 Enterprise" they have versions like 1709, 1809 etc.
The Product Smart group only shows Win10 and then inside a version numbering logic for each host. This data give you then secure/non secure/EOL.
The problem is that as company you have different set of users on different channels to allow a pre-business view before it hits our users. To get a proper view in SVM to see how many devices in each channel are secure/non secure I have every month to export your data, load to Excel, run painful Pivot with numbering mapping from MS page to get an overview in granular view:
- Channel
- version
- secure/non secure / EOL
docs.microsoft.com/en-us/windows/deployment/update/waas-overview
docs.microsoft.com/en-us/windows/release-information/
This is all manual and end up to use SCCM to show this information instead of SVM for what we paid for to have this add-hoc view with detailed information.
There must be a way to improve this 🙂
Nov 12, 2019 10:33 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Some suggestions
- Consistent naming of products (The Solaris ones are a bit of a mess). Perhaps a short name in addition to the long-winded one. Like RHEL-8, RHEL-7, SLES-15SP1 etc.
For example SOLARIS-5, SOLARIS-6 instead of some of them being Sun Microsystems, some Oracle and some Oracle formerly Sun Micro etc. - A method to list all the product names available. Especially if it listed the long-winded name and the short unambiguous name proposed above
- The API should return an error if the parameters are incorrect.
How many advisories could trace themselves back to functions ignoring the input, or the wrong input's causing unpredictable output? - A proper changelog or journal capable of being returned in guaranteed sequential order. The current update listing by modified date is ambiguous for what has actually changed. Because the detail is in the advisory and you only get the LATEST info, not the info for a particular advisory change notification
This would be useful for some historical what-if scenarios we're looking at presently - Ability to run more than 1 session per login token. Otherwise I have to convince someone to create a new user every time I want to setup a new environment for my app
Yes I could setup an internal server to provide the input to my environments but then it becomes chicken & egg when I need to enhance it for upcoming development that is not yet ready for PROD
Nov 13, 2019 07:58 AM
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
We are deploying apps via SCCM applications and SCCM AppV. There is at the moment not way to see in SVM product groups a split between both apps technologies. There is also no way to create an own product group to filter by them either deployment technology/product or/and based on a logic like path contains C:\ProgramData\AppV.
The issue is that we see products with both deployments been always combined into one product. We have then always to run an export of the data and split between virtual packaged update required vs physical installs. This way to build deployment collections is also more hard and complicated.
Could we add a way to display them differently or any kind of filtering option to be able to split them to avoid constantly export as csv and then back to Excel and Pivot?
Nov 13, 2019 10:23 AM
- SVM On-prem November Update in Software Vulnerability Management Release Blog
- SVM October 2024 Update in Software Vulnerability Management Release Blog
- SUSE Liberty Linux support in Software Vulnerability Management Forum
- SVM On-prem July 2024 Update (SVM installation is now supported in RHEL 8) in Software Vulnerability Management Release Blog
- Monthly Vulnerability Insights: June 2024 in Software Vulnerability Management Blog