A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Third Party Thursday: Focus on what matters and patch
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
The Third Party Thursday blog series aims to deliver more insight about new vulnerabilities that have been reported through Secunia Research at Flexera between the last Thursday of the past month until the last Thursday of the current month. The blog frequently includes a monthly summary of vulnerabilities and recommendations for security administrators about different ways to prioritize and mitigate software flaws. In this particular blog, we focus on vulnerability research from June 28 to July 25 in 2019.
Monthly Advisory Overview
In this period, Flexera has released 405 new Secunia Advisories (SAIDs). Secunia Research added the “Multiple Vulnerabilities” label to the titles of 212 new advisories, which is the process to signify that each advisory is disclosing one or more software vulnerabilities, as there is no upper limit.
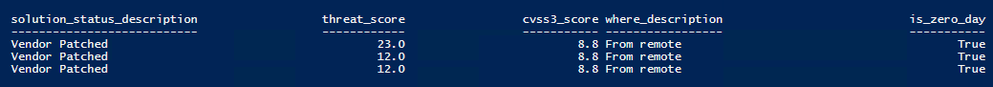
Three advisories for Microsoft Windows have received a zero-day advisory status. All vulnerabilities reported through the three, zero-day advisories have a vendor patch that can be deployed to patch the software flaws.
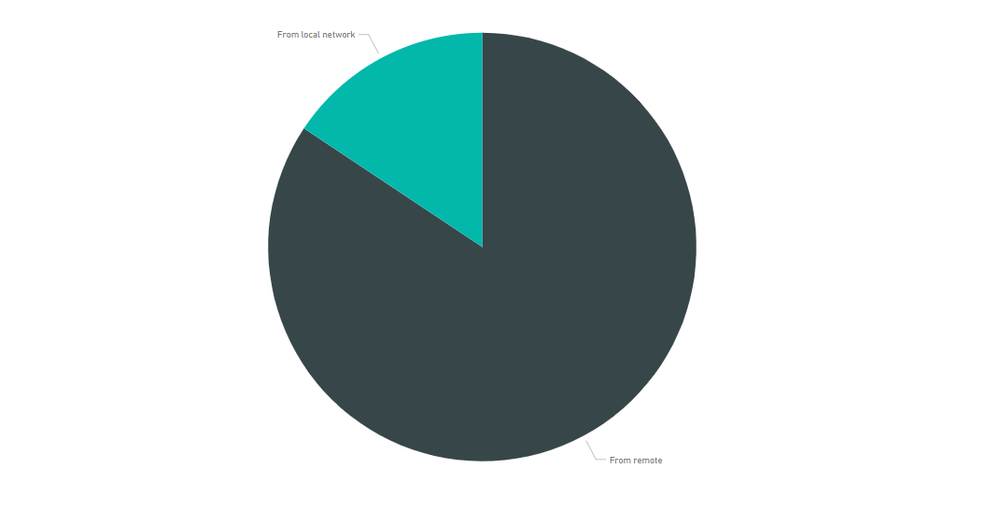
61.8% of all vulnerabilities disclosed in this period have a “from remote” attack vector. This is a larger percentage than what we've seen in previous months, likely because of the significant increase of remotely exploitable vulnerabilities reported in the “Moderately Critical” range – 121 out of 141 moderate advisories report on remotely exploitable software vulnerabilities.
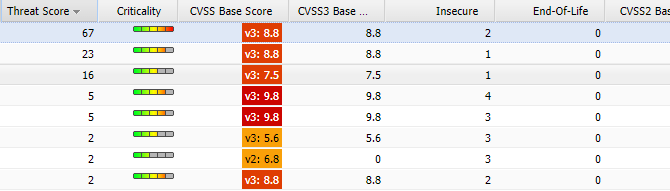
51.8% of all new security advisories published by Flexera in this period disclose one or more software vulnerabilities that have been associated with a known threat that can exploit them. The following list shows the monthly advisory breakdown of each of the available threat score ranges:
- Low Threat Score= 179 new SAIDs;
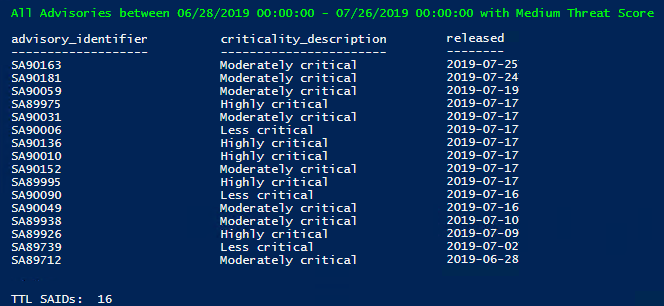
- Medium Threat Score = 16 new SAIDs;
- High Threat Score = 1 new SAID;
- Critical Threat Score = 13 new SAIDs;
- Very Critical Threat Score = 6 new SAIDs;
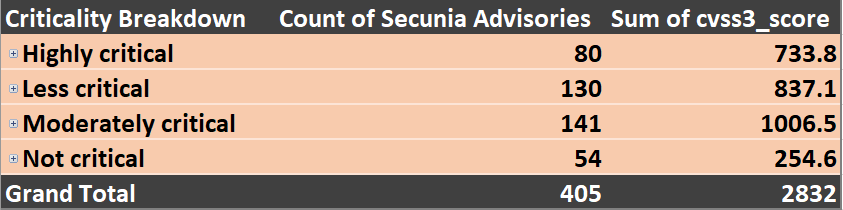
In July, Flexera didn't assign an extremely critical rating to any new advisories. The next figure shows the advisory count and CVSS3 score sums for the advisories found within each criticality range.
There was a notable increase in the overall count of less critical advisories (130) in July, as compared to 106 advisories issued in the previous month. The overall CVSS3 severity sum of all less critical advisories equaled nearly a quarter of the total severity introduced by all vulnerabilities all together.
141 advisories have been assigned a rating of Moderately Critical. A significant percentage (86%) of those can be exploited “from remote," while 14% have been identified as having the “local network” exploit vector. This makes advisories assigned with the moderately critical rating especially important to watch after.
Prioritize What Matters
To be able to cope with an expanded list of vulnerabilities, especially when trying to keep up with less and moderately critical advisories, it is important to focus on what matters first. Software Vulnerability Manager's Threat Intelligence module can help you take this approach. The prioritization of security patches will be based on informed decisions about the imminent risk of a security breach and not based on personal opinions or lack of other prioritization methods that can provide the same flexibility and insights. One can identify vulnerabilities across all criticality ranges that pose an imminent threat to their security and patch them first, before patching other flaws that pose no imminent threat to security.
Even when you can't patch the remainder of your software that has no known threat quickly, you would've left behind software programs that have no present or historical evidence of exploitation. At this point, you had successfully shut the wide-open front door of your network. The exploitation of software vulnerabilities that have no known exploit code will be a much harder task to accomplish, and it'll require malicious actors to take more time to test, target and execute their exploits against your environment.
This naturally opens more breathing space for vulnerability administrators and gets them ahead of the adversary in terms of vulnerability posture. It limits the exploitable attack surface significantly. That's especially important if you aim to prevent mass-targeted automated ransomware/malware campaigns, which would often target well-known vulnerabilities for which PoC exploit code is publicly available.
Patch More, Patch Faster
The Software Vulnerability Manager's rapid evolution is unbeatable. Flexera has just introduced a huge expansion of its patching capabilities with the introduction of the new Vendor Patch Module. Additionally, other new capabilities have been introduced including, API capabilities that can be used for improved cross-partition reporting and data automation purposes.
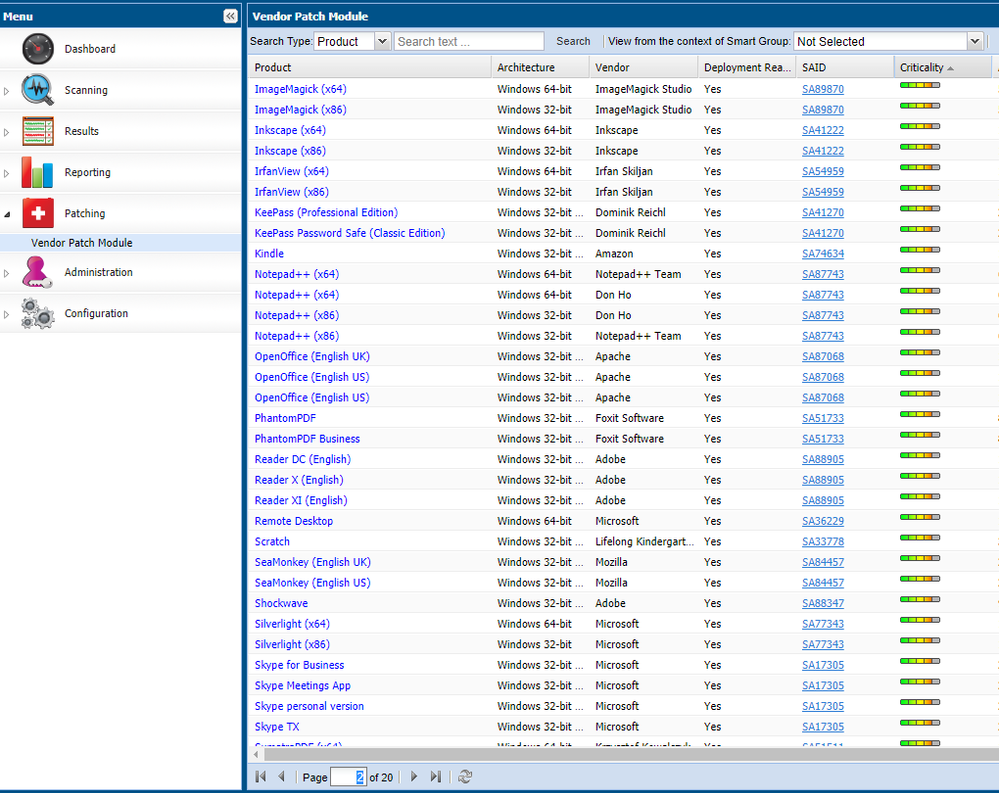
The recent inception of the Vendor Patch Module solves one fundamental vulnerability management problem - the lack of ability to deploy a larger array of patches, an array extensive enough to provide support for commercially available third-party software, but also for open-source projects and business-oriented software that isn't normally supported for patching through most security products.
The overall extensibility of Vendor Patch Module and its usefulness in a variety of patching use cases makes it the perfect addition to the already advanced SPS system. The extended vendor and product support greatly increase the speed with which you may address a larger number of security threats at once, with minimal effort, in a single patch management interface.
Packages in the Vendor Patch Module can be filtered through traditional security filters like SAID, criticality or threat score columns. This helps the Vendor Patch Module blend perfectly with the intended security profile of the Software Vulnerability Manager and it enables customers of Flexera to perform an easy adoption of the new vendor patch service, and quickly catch up with their patch backlogs to limit their vulnerability posture.
Final Thoughts
I often mention that hundreds of new vulnerabilities released every month may often cause panic among vulnerability administrators. This is what bad guys hope will happen, to capitalize on any mistakes that result from it. Panic cannot help anyone make the right decisions at the right times. Intelligent technology can do that. Software Vulnerability Manager has always been the most intelligent technology in its particular security space, but in the past few years, it lacked certain extensibility and flexibility, especially at the finishing phase.
Threat Intelligence, Vendor Patch Module, and new APIs help Flexera raise the bar for every vendor and competitor product that operates in the same space. It's raised the bar for hackers too, because this current technology is one of the very few that can change the status quo and put the time advantage in your hands—taking it away from hackers. Hackers will no longer have a time advantage over you. You can regain full control of all software vulnerability risks while reducing patch backlogs and catching up with all delays.
- New and Improved Threat Scores in SVM and SVR in Software Vulnerability Management Blog
- Monthly Vulnerability Review: September 2019 in Software Vulnerability Management Blog
- Third Party Thursday: Harness the power of Vulnerability Intelligence in Software Vulnerability Management Blog
- Third Party Thursday: monthly vulnerability trends in Software Vulnerability Management Blog