- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review: September 2019
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Foreword
The month of October is the "National Cybersecurity Awareness Month" (NCSAM) in the US, and the "European Cybersecurity Month" (ECSM). It is no different across other territories too. A pro-active collaborative effort between governments and the security industry is put, to raise general awareness about the importance of cybersecurity among citizens and organizations across the globe and to present the best methods of defense.
At Flexera, the cybersecurity awareness month repeats 12 times a year. This is why we launched the "Third Party Thursday" blog series six months ago. We aim to raise awareness among customers and the general public about the true threat picture as we see it, as nobody else reports on it, 12 times a year.
We are now changing the blog name to reflect better on the purpose of the blog series. We'll also make it easier for you to track the data in our reports by starting to analyze vulnerability data from between 1st - 31st date of each month. This is why we have now adopted the new blog name - Monthly Vulnerability Review.
The Monthly Vulnerability Review blog aims to deliver security insights derived from analyzing the software vulnerabilities processed, analyzed, and verified by Secunia Research at Flexera each month. By doing so, we aim to present the bigger picture that can serve as a baseline for organizations to adopt better vulnerability management strategies, as we also deliver ultimate insight on which vendors are most often being vulnerable.
Monthly Advisory Overview
Between August 29 - October 1 of 2019, Flexera has released a total of 405 new Secunia Advisory IDs (SAIDs).
A big 40.49% of them have been attributed to Unix/Linux/Debian-based software packages. This does not include vulnerabilities reported for Unix/Linux/Debian operating systems, or for the Linux Kernel itself.
The remaining 241 (59.51%) Secunia Advisories cover all other vendors and products, including the security software vulnerabilities in the Linux Kernel, and the underlying Unix/Linux/Debian operating system.
Products and Vendors Overview
The September's 405 SAIDs has been attributed to 79 unique vendors, 263 unique product titles, and 355 different software product versions. The next pie chart provides more detail on how much advisories have been attributed to each vendor in September, respectively. We provide a named top 25 list for extended visibility.
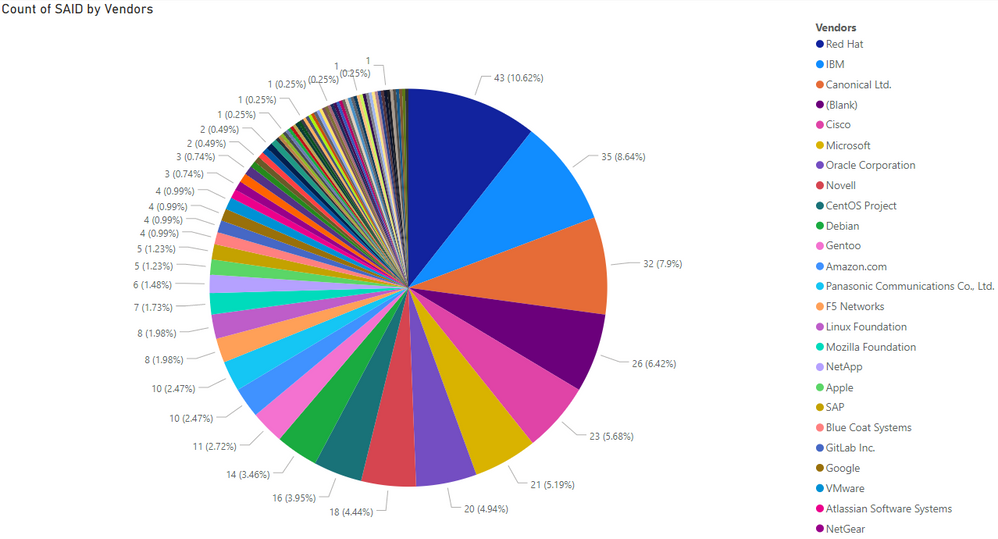
This statistic tells us that Microsoft-based vulnerabilities account for only 5.19% of the total monthly volumes. This shows how wrong it is to patching only Microsoft software while ignoring third-party Windows-based software or vulnerabilities reported on other operating system platforms such as Linux or Mac OSX.
Advisory Criticality Breakdowns
Next, we provided a breakdown of the 405 new advisories as per their assigned criticality ratings. The numbers provided on their right side indicate the increase or decrease in the total number of advisories compared to the month before. There have been fewer new security advisories in September compared to the month before.
- “Extremely Critical“ = 0 (-)
- “Highly Critical“ = 92 (+14)
- “Moderately Critical“ = 141 (-23)
- “Less Critical“ = 125 (-38)
- “Not Critical“ = 46 (-20)
To make a little more sense of this data, we compiled a report which shows the breakdown of criticality by vendors attribution. Next, you'll see the criticality shares that were attributed to each vendor. FYI, "Blank" refers to a collection of "various open-source software" such as Jenkins, Go, Piwigo, Netty, etc.
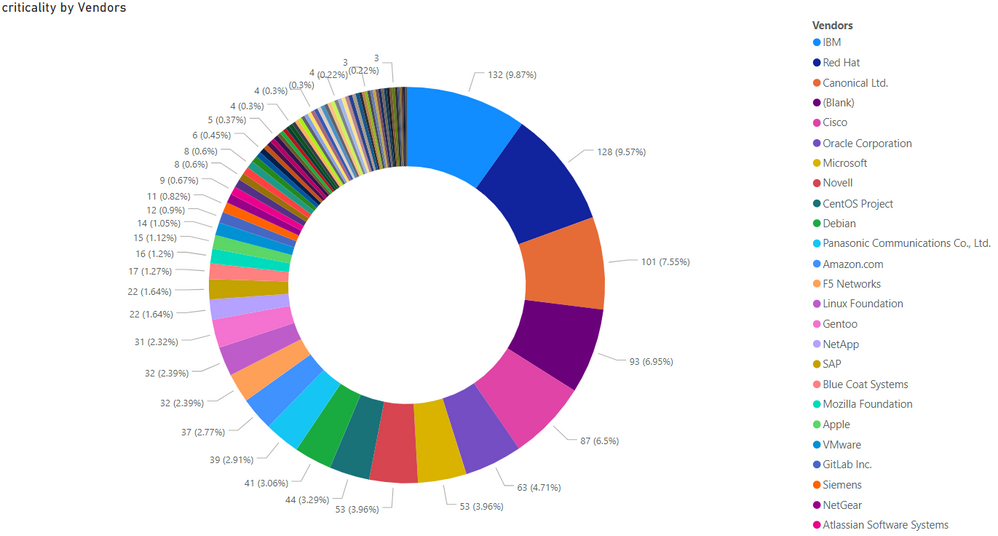
To understand what this criticality breakdown means, consider that the numbers provided for each vendor (e.g. IBM = 132) are the collective advisory criticality of the possible number of each of the ratings - from 1 to 5, where 1 equals "Extremely Critical" rating and 5 equals "Not Critical". We already know that e.g. IBM has 35 new SAIDs attributed to their name in September which produced a total Criticality sum of 132 (almost 10%).
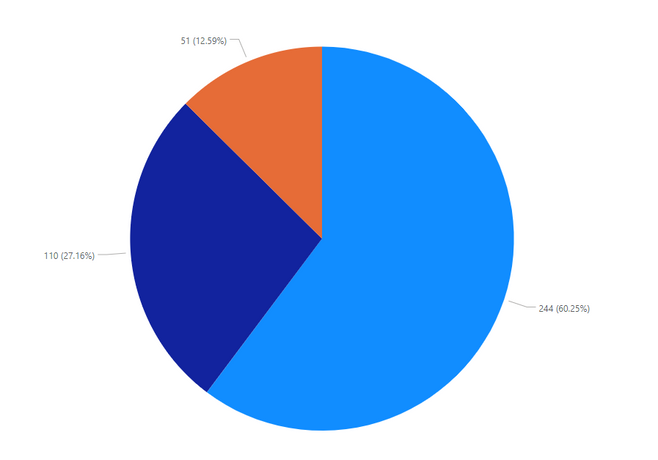
Attack Vectors Overview
60.25% of the software vulnerabilities reported in September by Flexera are remotely-exploitable. Another 27.16% have been identified as exploitable from the "Local Network". The remaining 12.59% of the vulnerabilities have been identified with a "Local System" attack vector. Over the past 6 months, we have noted a hard tendency where more than 55% of all vulnerabilities reported each month are remotely exploitable.
Advisory CVSS3 Overview
Flexera provides CVSS3 score calculation on the advisory level. We have broken down the 405 new advisories into 3 CVSS3 score ranges - low, medium, and high. Here is how a CVSS3 breakdown of these ranges looks like
- CVSS3 score under 4.0 = 29 SAIDs
- CVSS3 score range 4-7 = 128 SAIDs
- CVSS3 score range 7-10 = 248 SAIDs
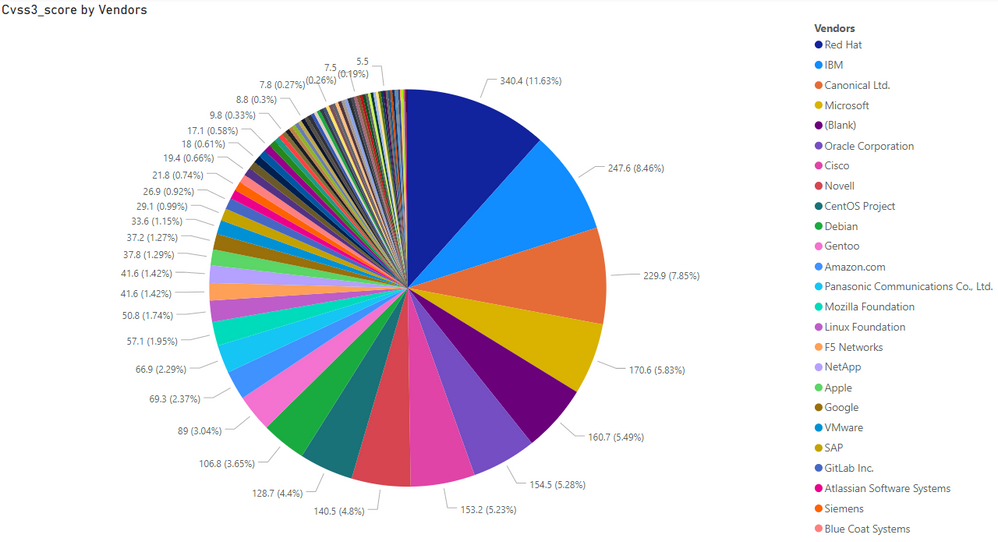
The average CVSS3 (against 405 SAIDs) for the month of September equaled CVSS3 of 7.2 per released advisory. If we look at the collective CVSS3 sum of all SAIDs as broken down by vendor names, we can see a change in the rankings as compared to the earlier breakdown ranking based on criticality ratings.
As one example, these statistics show us that IBM is slightly ahead of Red Hat in terms of SAID Criticality summing, while Red Hat is very much ahead of IBM in terms of the overall severity of their monthly advisories.
We can also see that Microsoft lines up 4th in overall severity summing while they did rank 7th in the advisory Criticality summing which we displayed earlier. This means that while Microsoft may have a lower number of advisories that create a lower summing in terms of Criticality, their advisories have a predominantly very high CVSS3 score assigned to them by Secunia Research. Such stats can be very relevant for prioritization purposes.
Monthly Vulnerabilities Overview
Unique Standalone Vulnerabilities
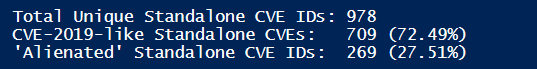
Flexera confirmed the exploitability of exactly 978 unique standalone vulnerabilities In September of 2019. That many unique vulnerability identifiers have been references in 405 new security advisories.
One standalone vulnerability may be exposed to more than one software product. This stat does not show the absolute count of vulnerabilities exposed through all 355 software versions reported vulnerable in this period.
For example, imagine the "Fallout, RIDL, ZombieLoad" Intel vulnerabilities reported in the month of May. These were identified in four unique standalone CVE IDs, but these four CVEs exposed dozens of vulnerabilities in all major operating system platforms, browsers, and other software packages that rely on direct CPU interaction.
72.49% of the 978 standalone vulnerabilities are the security flaws reserved and released in 2019 *(CVE-2019-like). The remaining 27.51% are vulnerabilities that have been reported throughout September, in a variety of software products but have been reserved and released in previous years (e.g. "alienated vulnerabilities").
Monthly Vulnerabilities-to-Patch [Minimum]
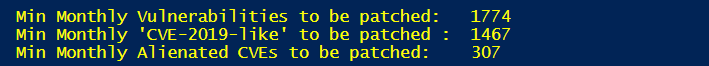
Different research teams track software vulnerabilities differently. Flexera tracks vulnerabilities by the product they appear in. If we look at it this way, there were at least 1774 vulnerabilities exposed through 355 different software product versions. This means that each unique standalone vulnerability validated by Flexera in September has been exposed through a minimum of two different products as reported in September of 2019.
Threat Intelligence Overview
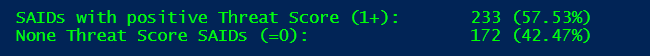
In September, 57.3% (233 SAIDs) of all released Secunia Advisories reported on at least one vulnerability with evidence of exploitation. 91% of them (212 SAIDs) reported at least one vulnerability that has been linked to historical cyber exploits on the day of the advisory release. We see another hard tendency where more than 55% of all new monthly advisories report on vulnerabilities that have already been exploited previously.
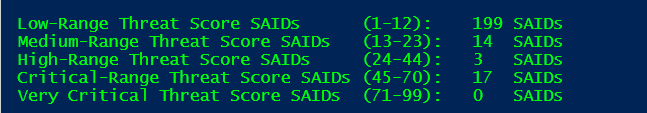
The following screen shows a breakdown of the advisories with a positive score by their threat score ranges:
Furthermore, let's consider the following analysis about the threats seen in the new 405 advisories:
- 17 SAIDs report on at least one vulnerability historically linked to ransomware
- 21 SAIDs report on at least one vulnerability historically linked to malware.
- 86 SAIDs report on at least one vulnerability linked to recent cyber exploits.
- 93 SAIDs report on at least one vulnerability linked to penetration testing tools and automated exploits.
Through its Threat Intelligence capabilities, Flexera has seen at least 22 different malware/ransomware families be exploiting at least 24 different CVEs which have been linked to a greater number of Secunia Advisories.
Conclusions
A large percentage of the software vulnerabilities each month are reported for Unix-based software packages.
There are a plethora of Linux Kernel/OS vulnerabilities reported each month in quite a lot of different Unix distros as well. Due to the shared functionality and design between many of them, when one core vulnerability is reported publicly, all other vendors follow to multiplicate the vulnerability effect within their distro builds.
This creates a lot of security issues for system designers and security teams who have to manage large environments comprised of many Unix/Linux/Debian servers. We can probably claim that around 50% of the vulnerabilities each month can be attributed to Unix/Linux/Debian systems, and their software package.
Creating a task force that is always ready to respond to newly reported Linux vulnerabilities and making sure that this task force has all the necessary tools to recognize shared functionality between the different flavors will help you take few steps in advance to hackers, especially if you can pro-actively patch imminent threats.
Here are a few more takeaways that we've seen this month, and we've seen repeating in the past few months:
- 55%+ of all vulnerabilities reported each month can be exploited from remote.
- 55%+ of all advisories include at least one vulnerability that has been exploited prior to advisory release.
- Nearly 30% of the monthly vulnerabilities each month are "alienated" that is, old issues that have been reported by the vendor way too late, or vulnerabilities that continue to re-appear in various products.
- More than 50% of all advisories report on at least one vulnerability linked to a historical cyber exploit.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Monthly Vulnerability Insights: March 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - February 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - January 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - December 2023 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - November 2023 in Software Vulnerability Management Blog