A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review - Mid November to Mid December
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
From Mid November till Mid December, 396 advisories were issued for 247 unique products.
Two zero-day advisories were issued during this period including a hotly debated SolarWind hack. It eclipses every other technology news due to its potential victims and sophistication.
Zero-Day Advisories
Solarwinds Orion Vulnerability a.ka. Sunburst
Solarwind reported that a vulnerability was injected into its Orion product platforms supply-chain system. It affects SolarWinds® Orion® Platform software, and SolarWinds Network Performance Monitor builds for versions 2019.4 HF 5, 2020.2 with no hotfix installed, and 2020.2 HF 1. [1]
An error related to SolarWinds.Orion.Core.BusinessLayer.dll containing a backdoor can be exploited to execute arbitrary code. Solarwinds digitally signed the Update containing the backdoor, so its users had no way of knowing if the Update was compromised.
Orion products downloaded, implemented, or updated during the relevant period contained the inserted backdoor. The relevant period is from March until June 2020. [2]
The vendor recommends updating to version 2019.4 HF 6 or 2020.2.1 HF 2.
The vulnerability is dubbed as Sunburst, and the list of the potentially affected customer is staggering. Solarwind lists US Armed forces, DoD agencies, UK defence sector, US department of treasury, UK NHS, NATO Support Agencies, and US president’s office among its customers.
The vulnerability is quite devastating because the software is a networking monitoring software which runs under a privileged account.
Flexera’ Secunia research has issued a Zero-day advisory SA99447 available in SVR, SVM and Data platform products. Further details are being added as they become available. Further details and its coverage in different products are available at this link
Microsoft Edge Chromium version:
A Google Chrome zero-day was reported on the 11th of November, which was covered in our previous blog. As a result, Microsoft Edge, based on the Chromium engine, also reported two vulnerabilities. One can be exploited to gain system access, and the other one has an unknown impact. Microsoft advises patching to 86.0.622.69.
Operating Systems:
The number of Secunia advisories for various Operating systems are as below:
- Fedora: 07
- Red Hat Enterprise Linux: 10
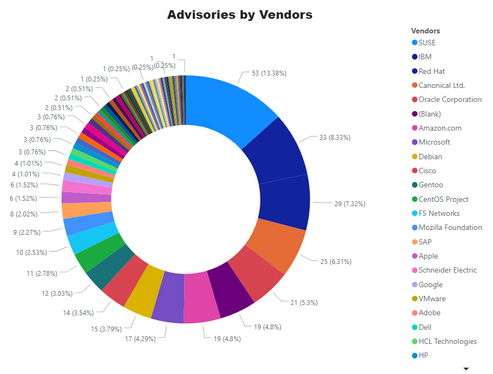
- Debian: 15
- Amazon Linux: 19
- Ubuntu: 25
- SUSE Linux: 53
- Oracle Linux: 17
- CentOS Advisories: 11
- Microsoft OS Advisories: 4
Advisories for Browsers
- Microsoft Internet Explorer (version 9 & 11): 1 Advisory.
- Microsoft Edge (HTML Based - Legacy): 1 Advisory
- Microsoft Edge (Chromium Based): 3 Advisories
- Google Chrome: 2 Advisories
- Mozilla Firefox: 2 Advisories
- Mozilla Thunderbird – 1 Advisory
Microsoft Patch Tuesday
December Patch Tuesday was a little light as compared to November. On December 8th – Second Tuesday of December, Microsoft issued advisories for these software.
- Microsoft Windows
- Microsoft Edge (EdgeHTML-based)
- Microsoft Edge for Android
- ChakraCore
- Microsoft Office and Microsoft Office Services and Web Apps
- Microsoft Exchange Server
- Azure DevOps
- Microsoft Dynamics
- Visual Studio
- Azure SDK
- Azure Sphere
A complete list of all applicable updates for August’s Patch Tuesday is here [3]
Patch Tuesday KBs
A digest of Patch Tuesday is listed here [4]
|
KB |
Affected OS/Software |
|
Windows 10, version 2004, Windows Server version 2004, Windows 10, version 20H2, Windows Server version 20H2 |
|
|
Windows 10 Version 1809, Windows Server 2019 |
|
|
Windows 10, version 1903, Windows Server version 1903, Windows 10, version 1909, Windows Server version 1909 |
|
|
Windows Server 2012 (Monthly Rollup) |
|
|
Windows 7, Windows Server 2008 R2 (Monthly Rollup) |
|
|
Windows 8.1, Windows Server 2012 R2 (Monthly Rollup) |
|
|
Windows 8.1, Windows Server 2012 R2 (Security-only update) |
|
|
Windows Server 2012 (Security-only update) |
|
|
Windows Server 2008 (Monthly Rollup) |
|
|
Windows 7, Windows Server 2008 R2 (Security-only update) |
|
|
Windows Server 2008 (Security-only update) |
|
|
Windows 10, version 1607, Windows Server 2016 |
|
|
Exchange Server 2019, Exchange Server 2016 |
|
|
Exchange Server 2013 |
|
|
Exchange Server 2010 Service Pack 3 |
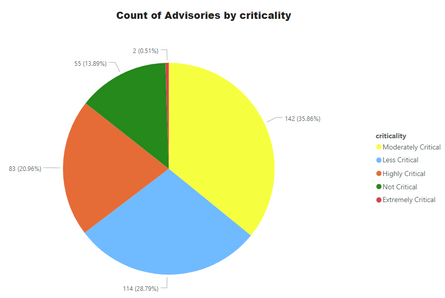
Advisories by Criticality
For easy understanding of Operations teams and management, Secunia Advisories are ranked into 5 simple and easy to understand criticalities. Secunia research follows a meticulous process which involves detailed analysis, peer review, and a QA process – among other things. Our customers can depend on the intelligence without indulging into more minute details of CVSS, impact and attack vector. All of these factors are considered during the ranking process. Further explained at this link.
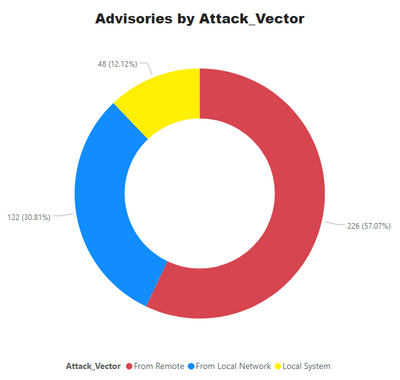
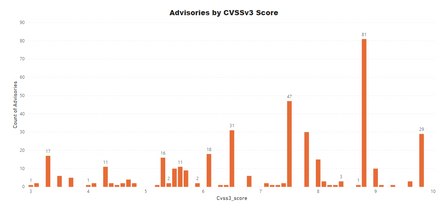
Advisories by Average CVSS Score
A CVSS score is a metric used to measure the severity of a vulnerability. CVSS v3 specifications and the criteria details are at this link.
CVSS ranges from 0 to 10. 0 being the lowest and 10 being the highest score; the advisories spread is as below:
CVSS 3 Score
- Advisories with Low CVSS3 under 4.0: 31 (7.83%)
- Advisories with Mid CVSS3 range 4-7: 133 (33.59%)
- Advisories with High CVSS3 range 7-10: 256 (60.24%)
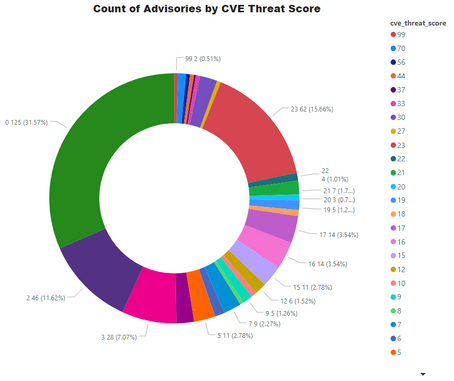
Threat Score
Threat score is calculated based on criticality and its linkage to a recent or historical threat of either remote trojan horse, ransomware, used in penetration testing tools, availability of exploit kit, and cyber exploit. Each rule triggers an increase in the threat value. A detailed explanation of Threat Score calculation is available at this link.
- Advisories with positive Threat Score (1+): 271 (68.43%)
- None Threat Score SAIDs (=0): 125 (31.57%)
- Low-Range Threat Score SAIDs (1-12): 124 (31.31%)
- Medium-Range Threat Score SAIDs (13-23): 123 (31.06%)
- High-Range Threat Score SAIDs (24-44): 16 ( 1.52%)
- Critical-Range Threat Score SAIDs (45-70): 06 ( 1.52%)
- Very Critical Threat Score SAIDs (71-99): 2 ( 0.51%)
Ransomware, Malware, and Exploit Kits:
- Historically Linked to Ransomware: 05 (1.26%)
- Historically Linked to Malware: 46 (11.62%)
- Linked to a Recent Cyber Exploit: 116 (29.29%)
- Related to a Historical Cyber Exploits: 172 (43.43%)
- Included in Penetration Testing Tools: 178 (44.95%)
Conclusion
The method and the style of SolarWinds Orion platform trojan horse throws a curveball at the organizations and security professionals. We preach to keep the software patched but ironically those customers that didn’t apply the Update were better off. However, users had no way of knowing if the patch contains malware as it was digitally code-signed by the vendor.
There would be many lessons to be learned by the software vendors and tighten up their supply-chain and build and publishing process. It is too early to call about the after-effects and change of behaviour, but many organizations have to review their software processes.
Many organizations were also panicking to check if they have affected software installed, which points out the need for an up to date software inventory.
A complete list of vulnerabilities, affected software, criticality, threat score, and relevant patch information is available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera. Stay Secure!
References:
[1] https://www.solarwinds.com/securityadvisory
[2] https://www.solarwinds.com/securityadvisory/faq
[4] https://msrc.microsoft.com/update-guide/releaseNote/2020-Dec
- SVM On-prem November Update in Software Vulnerability Management Release Blog
- Monthly Software Vulnerability Insights - December 2023 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - November 2023 in Software Vulnerability Management Blog
- 2022 Flexera Annual Vulnerability Review Report in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: Janurary 2023 in Software Vulnerability Management Blog