A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review - Mid January 2021
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
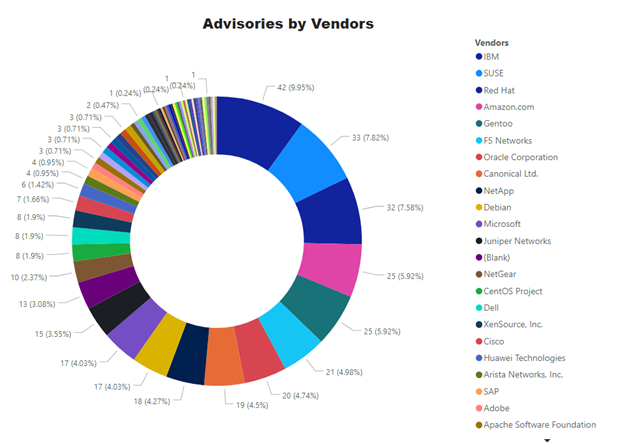
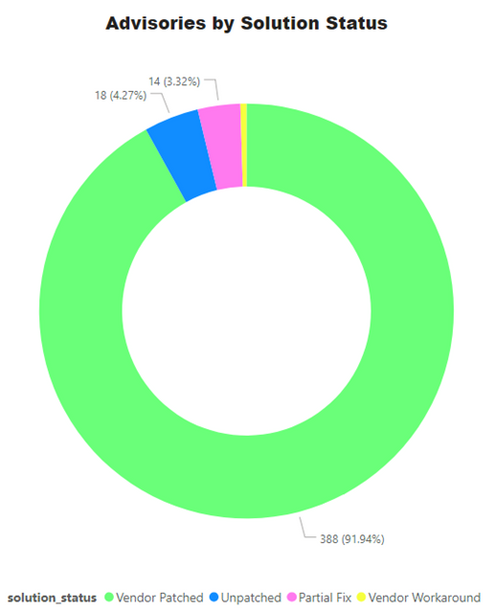
422 advisories for 281 unique product from 66 unique vendors were issued from Mid December 2020 till mid-January 2021.
Several Microsoft patches were issued in this month’s Patch Tuesday which included a patch for Microsoft Malware Protection Engine that is linked to SUNSPOT malware.
Zero-Day Advisories
Microsoft issued a zero-day in their recent patch Tuesday on January 12th. The advisory itself is moderately critical because of its local attack vector. However, it is linked t recent malware and cyber-attack. The vulnerability is reported in Microsoft Malware Protection engine which can be exploited to gain local escalation of privileges. CVE-2021-647 has 7.8 CVSS scores with a threat score of 28.
This vulnerability is particularly important as it is linked to SUNBURST and SUNSPOT vulnerabilities – as discussed in the previous blog. Microsoft Forefront Endpoint Security, Microsoft Malware Protection 1.x, Microsoft Security Essentials 4.x, Microsoft System Center Endpoint Protection, Microsoft Windows defender are the affected product.
Call to Action:
Microsoft recommends an update to version 1.1.17700.4.
In their security blog, Microsoft suggests that another target for the SUNBURST attack was to steal credentials, escalate privileges and move latterly to either steal and even create valid SMAL authentication token. Microsoft dubs it as SOLORIGATE. [1]
At this rate, the security industry is soon going to run out of interstellar acronyms for vulnerabilities and exploits.
Microsoft Patch Tuesday
January’s Microsoft Patch Tuesday edition had 11 KBS that fix 26 CVEs in 11 different products. [2] Another local escalation of privileges vulnerability CVE-2021-1648 was fixed which was an update to a previous update from December.
Patch Tuesday had updates for
- Microsoft Windows
- Microsoft Edge (EdgeHTML-based)
- Microsoft Office and Microsoft Office Services and Web Apps
- Microsoft Windows Codecs Library
- Visual Studio
- SQL Server
- Microsoft Malware Protection Engine
- .NET Core
- .NET Repository
- ASP .NET
- Azure
A list of KBs listed for different Operating systems is as below: [2]
|
KB |
Affected OS/Software |
|
4598229 |
Windows 10, Version 1903, Windows Server, Version 1903, Windows 10, Version 1909, Windows Server, Version 1909 |
|
4598230 |
Windows 10, Version 1809, Windows Server 2019 |
|
4598242 |
Windows 10, Version 2004, Windows Server, Version 2004, Windows 10, Version 20H2, Windows Server, Version 20H2 |
|
4598275 |
Windows 8.1, Windows Server 2012 R2 (Security-only update) |
|
4598278 |
Windows Server 2012 (Monthly Rollup) |
|
4598279 |
Windows 7, Windows Server 2008 R2 (Monthly Rollup) |
|
4598285 |
Windows 8.1, Windows Server 2012 R2 (Monthly Rollup) |
|
4598287 |
Windows Server 2008 (Security-only update) |
|
4598288 |
Windows Server 2008 (Monthly Rollup) |
|
4598289 |
Windows 7, Windows Server 2008 R2 (Security-only update) |
|
4598297 |
Windows Server 2012 (Security-only update) |
Advisories for different Operating Systems:
The number of Secunia advisories for various Operating systems are as below:
- Fedora: 00
- Red Hat Enterprise Linux: 27
- Debian: 17
- Amazon Linux: 24
- Ubuntu: 19
- SUSE Linux: 33
- Oracle Linux: 17
- CentOS Advisories: 08
- Microsoft OS Advisories: 05
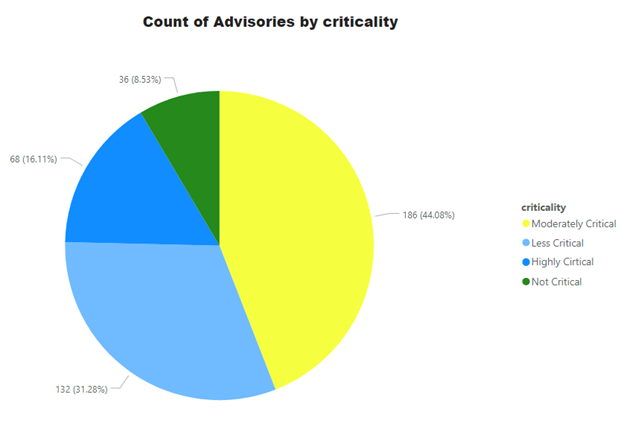
Advisories by Criticality
For easy understanding of Operations teams and management, Secunia Advisories are ranked into 5 simple and easy to understand criticalities. Secunia research follows a meticulous process which involves detailed analysis, peer review, and a QA process – among other things. Our customers can depend on the intelligence without indulging into more minute details of CVSS, impact and attack vector. All of these factors are considered during the ranking process. Further explained at this link.
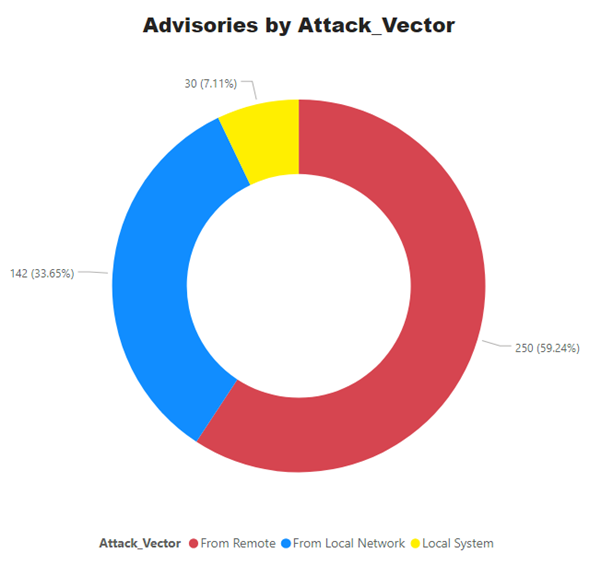
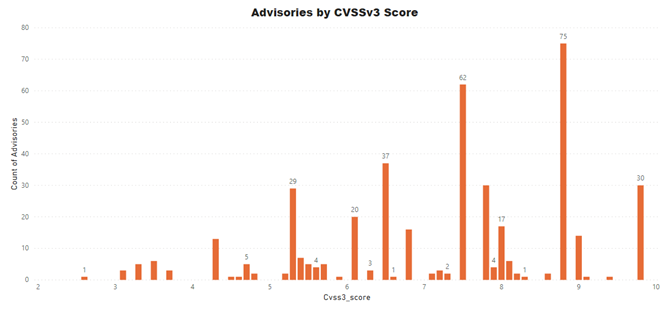
Advisories by Average CVSS Score
A CVSS score is a metric used to measure the severity of a vulnerability. CVSS v3 specifications and the criteria details are at this link.
CVSS ranges from 0 to 10. 0 being the lowest and 10 being the highest score; the advisories spread is as below:
CVSS 3 Score
- Advisories with Low CVSS3 under 4.0: 18 (4.2%)
- Advisories with Mid CVSS3 range 4-7: 152 (36.02%)
- Advisories with High CVSS3 range 7-10: 252 (59.72%)
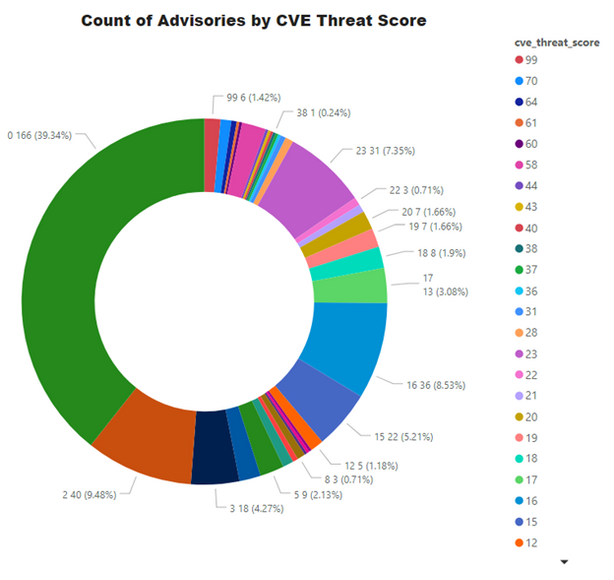
Threat Score
Threat score is calculated based on criticality and its linkage to a recent or historical threat of either remote trojan horse, ransomware, used in penetration testing tools, availability of exploit kit, and cyber exploit. Each rule triggers an increase in the threat value. A detailed explanation of Threat Score calculation is available at this link.
- Advisories with positive Threat Score (1+): 256 (60.66%)
- None Threat Score SAIDs (=0): 166 (39.34%)
- Low-Range Threat Score SAIDs (1-12): 92 (21.80%)
- Medium-Range Threat Score SAIDs (13-23): 130 (30.81%)
- High-Range Threat Score SAIDs (24-44): 11 ( 2.61%)
- Critical-Range Threat Score SAIDs (45-70): 17 ( 4.03%)
- Very Critical Threat Score SAIDs (71-99): 6 ( 1.42%)
Ransomware, Malware, and Exploit Kits:
- Historically Linked to Ransomware: 10 (2.37%)
- Historically Linked to Malware: 59 (13.98%)
- Linked to a Recent Cyber Exploit: 60 (14.22%)
- Related to a Historical Cyber Exploits: 154 (36.49%)
- Included in Penetration Testing Tools: 176 (41.71%)
Conclusion
The affects pf SUNBURST vulnerabilities are still being unveiled and its aftershocks will be felt for quite some time – unfortunately. Microsoft has revealed that it is being used to steal and even creating new SAML authentication tokens.
A complete list of vulnerabilities, affected software, criticality, threat score, and relevant patch information is available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera. Stay Secure!
References:
[2] https://msrc.microsoft.com/update-guide/releaseNote/2021-Jan
- Monthly Vulnerability Insights: October 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: September 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: August 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: July 2024 in Software Vulnerability Management Blog
- SVM On-prem July 2024 Update (SVM installation is now supported in RHEL 8) in Software Vulnerability Management Release Blog