A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review – March 2020
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
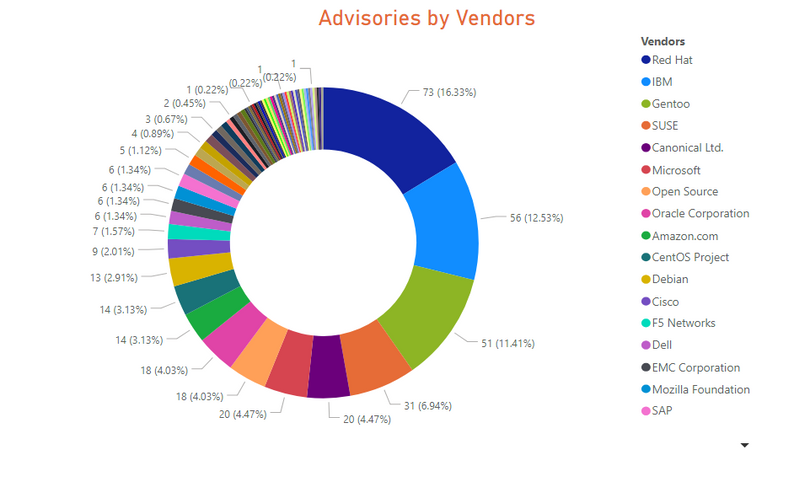
447 advisories for 67 unique vendors in 286 products and 344 unique versions, while issued 133 rejected advisories.
A zero-day vulnerability in Trend Micro Worry-Free Business Security was reported on March 17th.
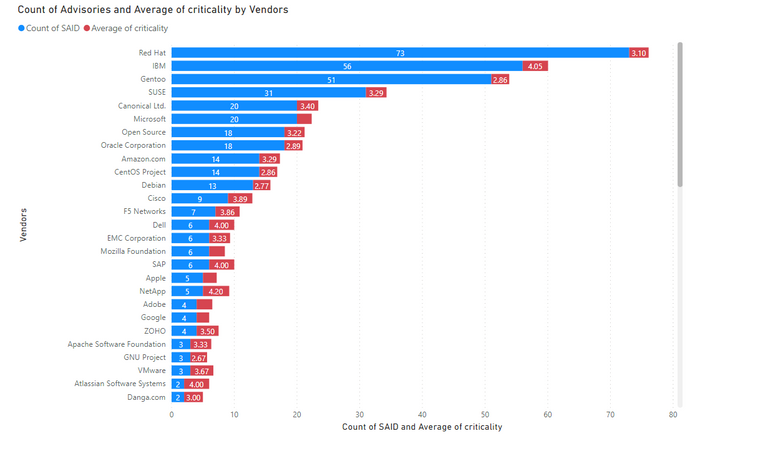
Red Hat was the top vendor with most vulnerabilities in Red Hat Enterprise Linux and Fedora Project
20 advisories for Microsoft products, which landed it on 6th top vendor.
Linux-based Operating systems were once again among the top Operating systems with most advisories.
Zero-Day
A zero-day vulnerability in Trend Micro Worry-Free Business Security 9.x. The patch for this vulnerability was available on the day of its public disclosure.
An Extremely critical advisory was issued for Microsoft Windows Operating systems. Vulnerabilities in Adobe Type Manager Library can be exploited from remote, which can result in arbitrary code execution.
Call to Action
Update to the version 9.5 B1525 version.
Deploy Microsoft updates for Windows 7, 8.1, 10, and Server 2008, 2012, and 2016.
Key Points
- Except for IBM, the vendors of Operating systems were among the top 10 list with most vulnerabilities.
- Microsoft had 20 advisories and slipped back to 6th position. Out of band patches were issued for Microsoft Edge on Feb 7th and 26th.
Call to Action
- Make sure to Install relevant patches from Red Hat Linux, Ubuntu, IBM, SUSE, and yum update repositories.
- Follow Not only the Patch-Tuesday but also install the Out of Band patches for Microsoft. The extremely critical advisory was issued on 23rd March – not in the regular Patch Tuesday.
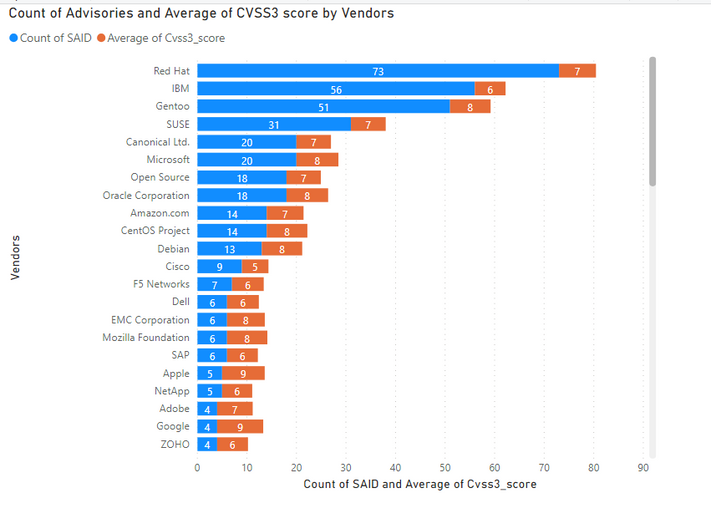
5 being the highest criticality, the below graph shows the average criticality per vendor, which is sorted based on the number of advisories.
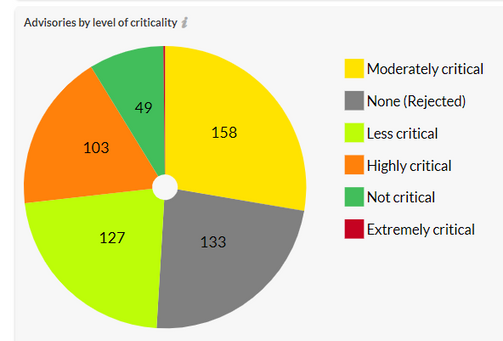
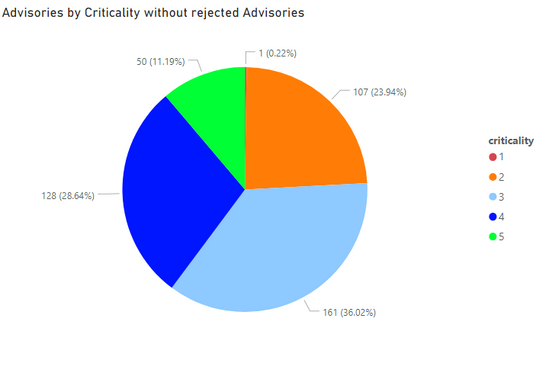
Secunia Research at Flexera categories the severity of vulnerabilities into five criticalities ranging from Extremely to Not Critical. It helps executives, system administrators, and Non-security people to quickly understand the gravity of issues.
1. Extremely Critical, 2. Highly Critical 3. Moderately Critical 4. Less Critical 5. Not Critical
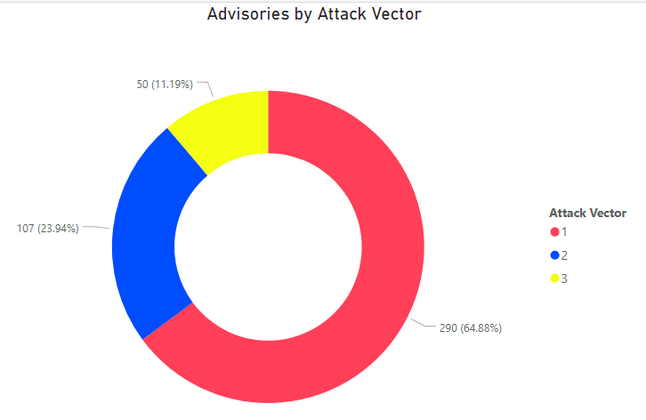
Count of Advisories versus Attack Vector.
The majority of vulnerabilities can be exploited by remote – 65%.
1. Remote. 2. Local Network. 3. Local System
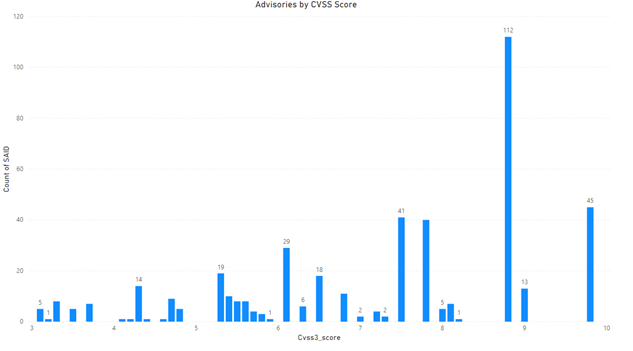
Advisories by Average CVSS Score
CVSS is an industry-standard used to rank the severity of a vulnerability. CVSS 3 is the standard.
CVSS 3 Score
- Advisories with Low CVSS3 under 4.0: 26 (5.82%)
- Advisories with Mid CVSS3 range 4-7: 149 (33.33%)
- Advisories w/ High CVSS3 range 7-10: 272 (54.70%)
Here we rank the Vendors and average of CVSS scores for the vulnerabilities reported in their relevant advisories.
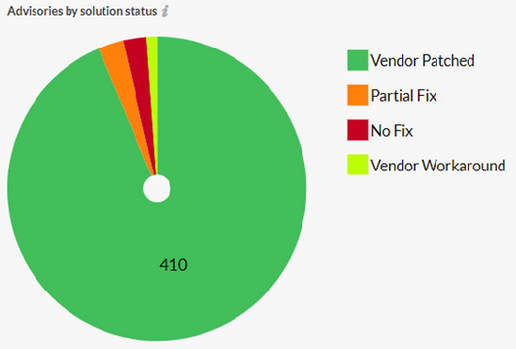
Advisories by Solution
87% of vulnerabilities had a vendor patch available, while only 3.2% had no fix while the same amount had a vendor suggested workaround.
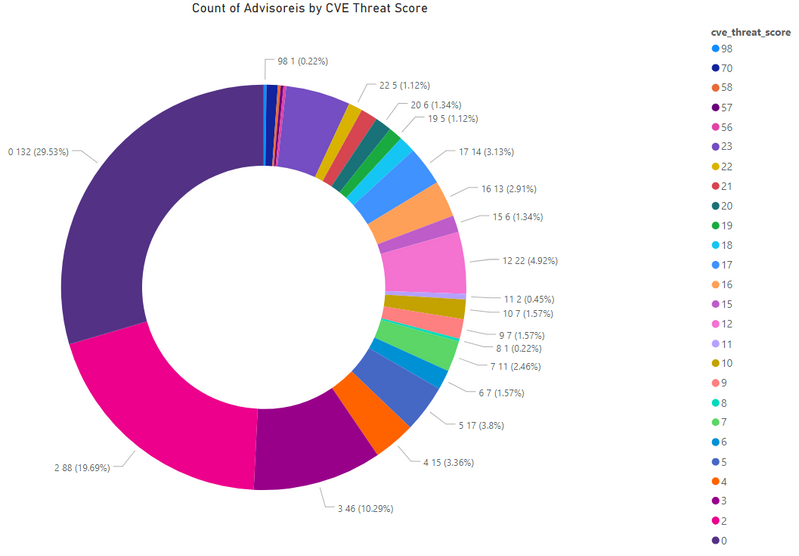
Threat Score
A detailed threat score helps security professionals to make the right decision when faced with multiple vulnerabilities at the same time.
- Advisories with positive Threat Score (1+): 315 (70.47%)
- None Threat Score SAIDs (=0): 132 (29.53%)
- Low-Range Threat Score SAIDs (1-12): 223 (49.89%)
- Medium-Range Threat Score SAIDs (13-23): 84 (18.79%)
- High-Range Threat Score SAIDs (24-44): 0 (0.00%)
- Critical-Range Threat Score SAIDs (45-70): 7 (1.57%)
- Very Critical Threat Score SAIDs (71-99): 1 (0.22%)
Ransomware, Malware, and Exploit Kits:
4 instances of MyKing Botnet with CVE-2019-12418 in Ubuntu, Gentoo, and Debian, SUSE, Red Hat JBoss.
- Historically Linked to Ransomware: 6 (134%)
- Historically Linked to Malware: 45 (10.07%)
- Linked to a Recent Cyber Exploit: 49 (10.96%)
- Related to a Historical Cyber Exploits: 251 (56.15%)
- Included in Penetration Testing Tools: 185 (41.39%)
Conclusion
There was an increase of 20% in advisories in March as compared to February. Relying on Patch-Tuesday to update Microsoft Operating system and products is not enough. An extremely critical advisory was issued as out-of-band for all Microsoft Operating systems.
A comprehensive information system is required, which can help to prioritize remediation based on the actual risk and exploit vector. A complete list of vulnerabilities affected versions, criticality, threat score, and relevant patch information are available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera.
- Monthly Vulnerability Insights: October 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: September 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: August 2024 in Software Vulnerability Management Blog
- SVM August 2024 Update in Software Vulnerability Management Release Blog
- Monthly Vulnerability Insights: July 2024 in Software Vulnerability Management Blog