A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review – January 2020
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
In January, Secunia Research issued 385 advisories from 76 unique vendors in 276 products and 394 unique versions, which is a decrease of 28.3% from December 2019.
Browsers were once again at the center of Zero-day vulnerabilities, which included Internet Explorer, Mozilla Thunderbird, and Firefox.
Linux type Operating systems were once again among top OS with most vulnerabilities.
Banking Trojan malware ‘Minerva,’ variants of ‘Zeus’ and ‘Flame Pony’ were linked to vulnerabilities in Google Chrome, MS Windows, Ubuntu, RSA Authentication manager – among others.
Zero Days
- Zero-day vulnerabilities in Internet explorer CVE-2020-0674 and CVE-2020-0706 are related to memory corruption errors that can ultimately result in remote execution. These vulnerabilities are linked to Historical and recent Cyber Exploits, malware, and included in penetration testing tools. Internet Explorer Version 9.x, 10.x and, 11.x are vulnerable.
Internet Explorer was unpatched until February’s Patch Tuesday. It resulted in companies and government institutions issuing alerts to their users to avoid using Internet Explorer until patched.
- CVE-2019-17026: A type confusion error when handling information in Mozilla Firefox can be exploited to execute arbitrary code. It has links to historical and recent cyber exploits and penetration testing tools.
- Multiple vulnerabilities were found in Mozilla Thunderbird, where a successful exploit can result in system access, Security bypass, and exposure of sensitive information.
Call to Action
- Install the relevant Microsoft KBs that were shipped with Patch Tuesday in February to patch IE.
- Update Mozilla Firefox to 73.x.
- Update Mozilla Thunderbird to 68.5.
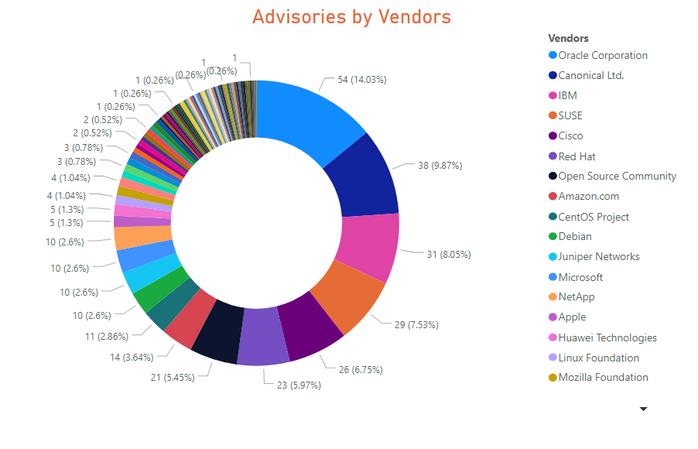
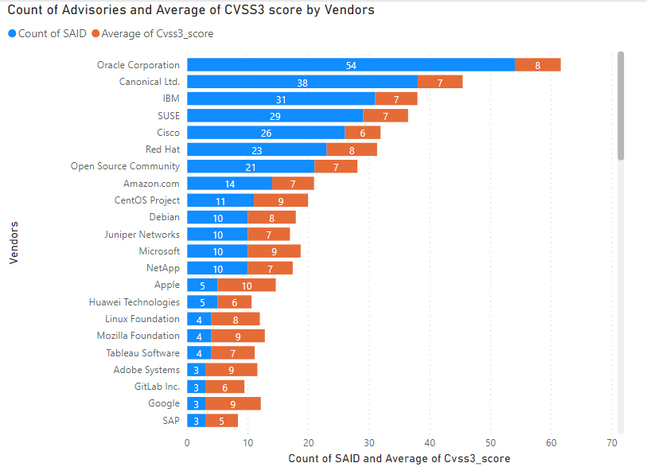
Advisories by Vendors
Key Points
- Oracle topped the list once again, with 51 advisories reported in its products. It was also the top vendor in November last year. Oracle Linux, Java, Solaris were among the well-known software and OS, among others, from the same vendor.
- Canonical Ltd, SUSE, Red Hat, Amazon, CentOS, and Debian were among the top 10 Linux/Unix type Operating systems distributions that had most advisories.
- Twenty-six advisories were issued for Cisco Router, Switches, and IP telephony software.
- Microsoft consistently dropped down and reached the 12th position among most advisories by vendors. However, some high visibility and its prevalence gave it some negative press.
Call to Action
- Install relevant patches from Linux, Ubuntu, IBM, SUSE, and yum update repositories.
- Patch Cisco Routers 6000 series and Switches - mainly 200, 300 and 500 series, and IP telephony software and clients.
- Microsoft issued patches for its software and OS on Patch Tuesday – which is the second Tuesday of the month – Install the Patch Tuesday patches religiously.
Deploy the updates, upgrades, and patches where and when available where required. For a complete list of vulnerabilities, affected versions, criticality, threat score, and relevant patch information is available in the Software Vulnerability Research and Manager tool from Flexera.
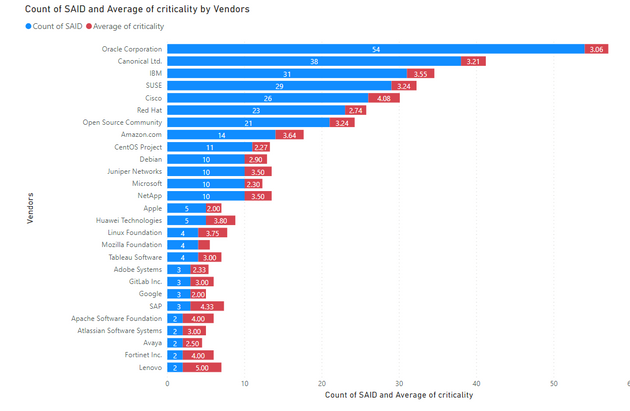
Average Criticality Per Vendor
5 being the highest criticality, the below graph shows the average criticality per vendor, which is sorted based on the number of advisories.
Note: SAID stands for Secunia Advisory ID. Each advisory issued by Secunia research receives a unique identifier. We use the unique SAID number to count the advisories per vendor and the average criticality for all advisories from the same vendor; issued during January.
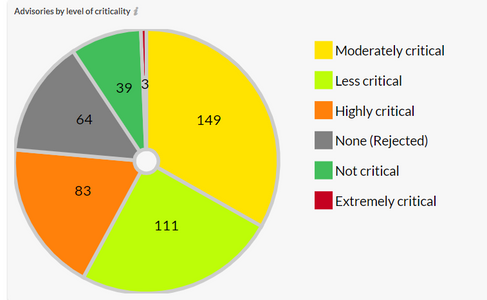
Advisories by Criticality
Secunia Research at Flexera categories the severity of vulnerabilities into five criticalities ranging from Extremely to Not Critical. It helps executives, system administrators, and Non-security people to easily understand the severity of issues.
A key differentiator is that it also rejects vulnerabilities and issue rejection notices if the exploit requires too much effort and no and less value gain. There are multiple criteria used to issue rejection notices. It helps our customers to focus on the actual Risk and threat. Sixty-four rejection notices were issued in January.
3 Critical vulnerabilities were the Zero-days in Internet Explorer, and Mozilla Firefox and Thunderbird.
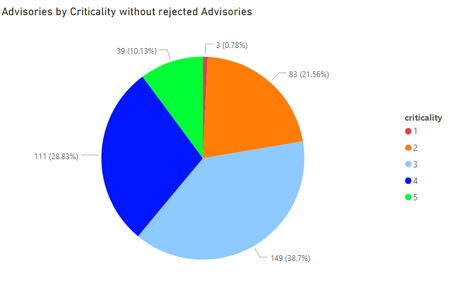
If we remove Rejected advisories, then the criticality spread looks like as shown below.
1. Extremely Critical, 2. Highly Critical 3. Moderately Critical 4. Less Critical 5. Not Critical
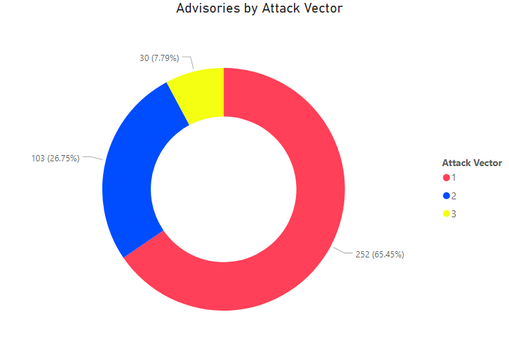
Total Advisories versus Attack Vector
65.5% of vulnerabilities can be exploited from remote, which makes the remediation efforts even more critical.
1. Remote. 2. Local Network. 3. Local System
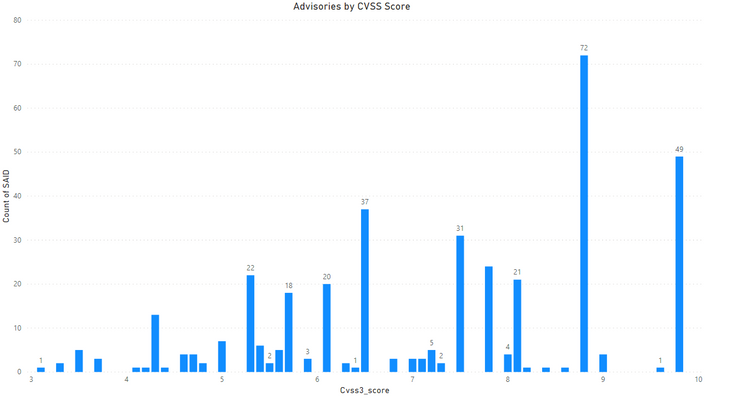
Advisories by Average CVSS Score
CVSSv3 provides insights into the level of severity and criticality. It includes Base Score metrics, temporal score, and Environmental Score. Some parameters are constants and provided by Secunia Research, but some can be changed according to each organization’s needs and sensitivity of the affected asset.
CVSS 3 Score
- SAIDs with Low CVSS3 under 4.0: 11 (2.86%)
- SAIDs with Mid CVSS3 range 4-7: 152 (39.48%)
- SAIDs w/ High CVSS3 range 7-10: 222 (57.66%)
Here we rank the Vendors and average of CVSS scores for the vulnerabilities reported in their relevant advisories.
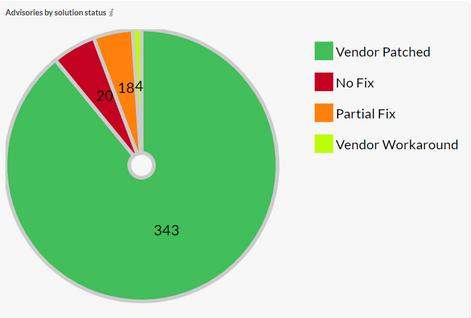
Advisories by Solution
89% of vulnerabilities had a solution, while 42% percent of reset of advisories that didn’t have a full fix had a partial fix.
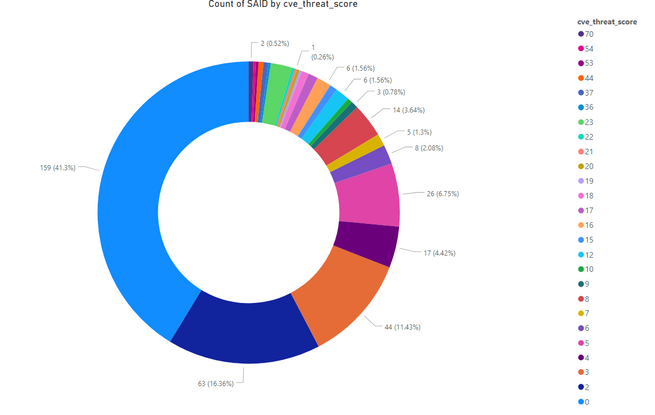
Threat Score
The new feature in Software vulnerability Research and Software Vulnerability Management solutions helps our customers to prioritize and remediate based on the genuine threat and risk landscape.
Oracle Linux update for OpenJDK, Peoplesoft Enterprise, and Debian update for Xen had the highest threat scores of 54 and 70, respectively.
Software Vulnerability Research tool also provides further insights into why a particular vulnerability is scored higher and if it is linked to malware, cyber exploit, ransomware, or linked to vulnerability scanners.
- Advisories with positive Threat Score (1+): 226 (58.70%)
- None Threat Score Advisories (=0): 159 (41.30%)
- Low-Range Threat Score Advisories(1-12): 188 (48.83%)
- Medium-Range Threat Score Advisories (13-23): 29 (7.53%)
- High-Range Threat Score Advisories (24-44): 5 (1.30%)
- Critical-Range Threat Score Advisories (45-70): 4 (1.04%)
- Very Critical Threat Score Advisories (71-99): 0 (0.00%)
Ransomware, Malware, and Exploit Kits
Four instances of vulnerabilities with CVE-2019-2894 and 2 with CVE-2019-13627 were linked to Banking Trojan Minerva found in Ubuntu, Xeros Print Server, RSA authentication Manager, SUSE Linux Enterprise Server.
Vulnerabilities exploited by another banking malware ‘Flame Pony Emotet Mimikatz Zeus’ were found in Microsoft Edge, Google Chrome 79.x.
‘Zeus Chanitor CoinMiner CMRig Miner’ was linked to Ubuntu Linux, which relates to Cryptocurrency mining – as the name suggests.
‘Flame Pony Mimikatz Emotet Zeus’ was linked to vulnerabilities found in Microsoft Windows 10, Server 2016, Server 2019.
- Historically Linked to Ransomware: 4 (1.04%)
- Historically Linked to Malware: 25 (6.49%)
- Linked to a Recent Cyber Exploit: 79 (20.52%)
- Linked to a Historical Cyber Exploits: 187 (48.57%)
- Linked to Penetration Testing Tools: 102 (26.49%)
Conclusion
The number of vulnerabilities keeps increasing over time, which requires targeted efforts from a risk and threat intelligence approach tackling vulnerabilities affecting critical assets in an organization. CISOs, security teams, and administrators struggle to keep up with the ever-changing threat model. A reliable and effective approach to discover, analyze, prioritize, and remediate these vulnerabilities is required.
Deploy the updates, upgrades, and patches where and when available where required. A complete list of vulnerabilities affected versions, criticality, threat score, and relevant patch information are available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera.
- Monthly Vulnerability Insights: October 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: September 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: August 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: July 2024 in Software Vulnerability Management Blog
- SVM On-prem July 2024 Update (SVM installation is now supported in RHEL 8) in Software Vulnerability Management Release Blog