A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review – April 2020
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
623 advisories for 91 unique vendors in 406 products and 512 unique versions, while issued 107 rejected advisories. An increase of 40% advisories from the previous month.
Zero-day vulnerabilities in Mozilla Firefox and 3 Extremely Critical advisories were reported in Microsoft Operating systems.
Red Hat kept its position as a top vendor with the most amount of vulnerabilities, and Microsoft also held its 6th position.
Kinsing and Loncom are the most prevalent malware, mainly affecting open-source operating systems and Mozilla Firefox.
Zero-Day
Two zero-day vulnerability was reported in Mozilla Firefox with CVE-2020-6819 and CVE-2020-6820 in Mozilla Firefox 68.x and 74.x. The vulnerabilities are linked to malware, cyber exploits, and used in penetration testing tools.
Three extremely critical advisories were issued for each set of Microsoft Operating systems. These advisories were part of Patch Tuesday. All advisories had a positive threat score, which means they were linked to malware and cyber exploits.
Call to Action
- Update Mozilla Firefox 74.x to 74.0.1 and 68.x to 68.6.1.
- Deploy Patch Tuesday as soon as they are released, but particularly for April. These patches shouldn’t be delayed too late for regular patch cycles.
Operating Systems:
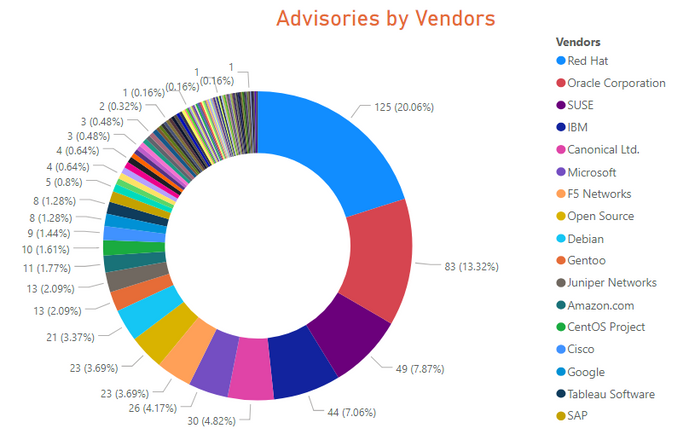
- 125 advisories for Red Hat Enterprise Linux 7,8, and Fedora 30 and 31.
- 30 advisories for Ubuntu 14.04, 16.04 and 18.04
- 49 advisories for SUSE Linux Enterprise Linux Server (SLE) version 11 through 15
- 39 advisories for Oracle Linux 6 and 7 and two advisory for Oracle Solaris.
- 21 advisories for Debian 10.x and GNU/Linux 9.x.
- 10 advisories for CentOS 6.x.
- 11 advisories for Amazon Linux AMI and 2.
- 1 advisory for each of the Microsoft Client and Server Operating systems.
Advisories by Vendors
Key Points
- Operating systems are always among top products with most vulnerabilities.
- Microsoft had 26 advisories. Out of band patches were issued for Microsoft Edge and Office 2019/O365.
- Networking products are non-operating products with the most vulnerabilities. These include F5 Networks, Juniper Networks, and Cisco.
Call to Action
- Install the relevant patches for operating systems.
- Now that everyone is using remote connectivity tools, make sure to update your Cisco WebEx Meeting Desktop app and Recording player applications.
- Network equipment shouldn’t be ignored as they are the first line of defense against external attacks.
- Update F5 BIG-IP Access Policy Manager (APM).
- Update Juniper Junos OS 12.x, 14.x, 15.x,18.x, and 19.x.
- Cisco 5500 Series Wireless Controller, IP Phone 8800, and 7800 Series.
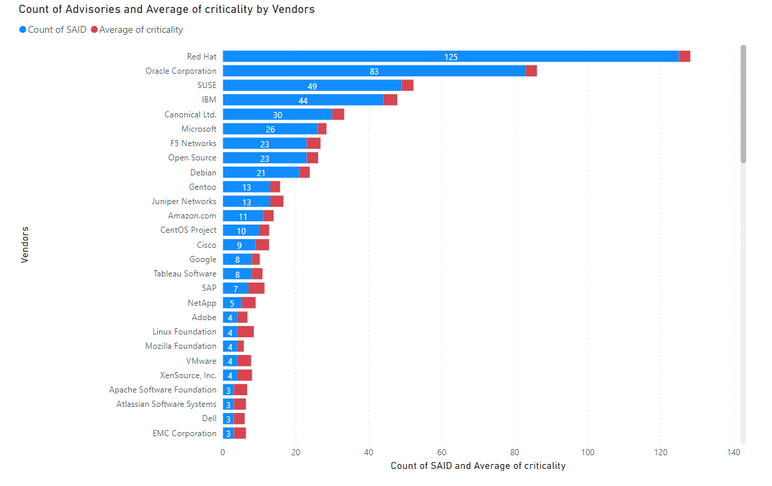
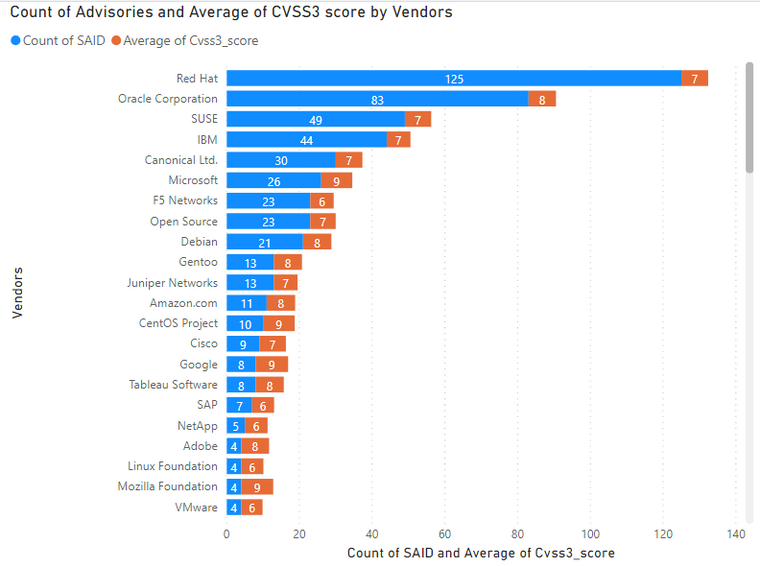
Average Criticality per Vendor
5 being the highest criticality, the below graph shows the average criticality per vendor, which is sorted based on the number of advisories.
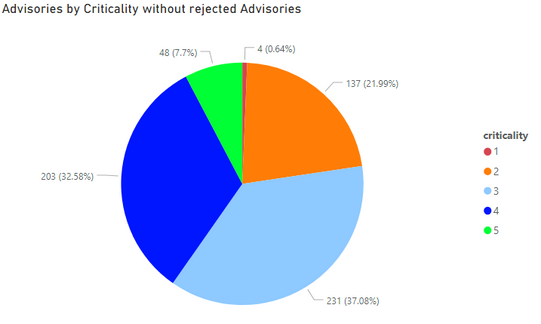
Advisories by Criticality
Secunia Advisory criticalities are further explained at this link.
If we remove Rejected advisories, then the criticality spread looks like as shown below.
Count of Advisories versus Attack Vector.
65% of vulnerabilities can be exploited from remote, which makes the remediation efforts even more critical.
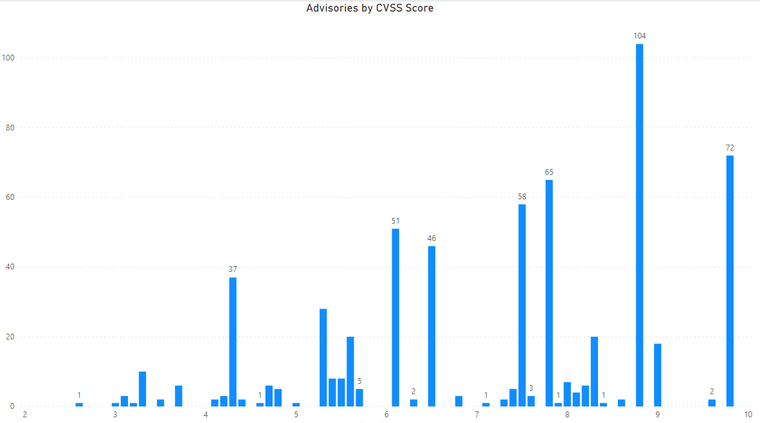
Advisories by Average CVSS Score
A CVSS score is a metric that is used to measure the severity of a vulnerability. CVSS3 specifications and the criteria details can be found at this link.
CVSS 3 Score
- Advisories with Low CVSS3 under 4.0: 24 (3.85%)
- Advisories with Mid CVSS3 range 4-7: 228 (36.60%)
- Advisories with High CVSS3 range 7-10: 371 (59.55%)
Here we rank the Vendors and average of CVSS scores for the vulnerabilities reported in their relevant advisories.
Advisories by Solution
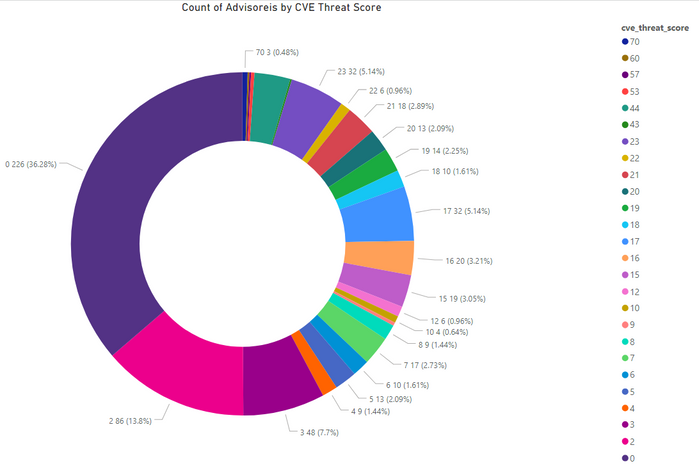
Threat Score
The criteria for Threat Score calculation is outlined at this link.
- Advisories with positive Threat Score (1+): 397 (63.72%)
- None Threat Score SAIDs (=0): 226 (36.28%)
- Low-Range Threat Score SAIDs (1-12): 204 (32.74%)
- Medium-Range Threat Score SAIDs (13-23): 164 (26.32%)
- High-Range Threat Score SAIDs (24-44): 22 (3.53%)
- Critical-Range Threat Score SAIDs (45-70): 7 (1.12%)
- Very Critical Threat Score SAIDs (71-99): 0 (0.00%)
Ransomware, Malware, and Exploit Kits
17 instances of kinsing and Loncom with CVE-2020-6819 in Oracle, Red hat Linux, SUSE and CentOS, Fedora, and Mozilla Firefox and Thunderbird.
4 instances of SafeStrip (Fake Antivirus), Snatch Ransomware, Mdrop, and Xhelper (Adware) in CentOS, Oracle Linux, and RedHat with CVE-2019-17666.
- Historically Linked to Ransomware: 6 (0.96%)
- Historically Linked to Malware: 59 (9.47%)
- Linked to a Recent Cyber Exploit: 111 (17.82%)
- Related to a Historical Cyber Exploits: 267 (42.86%)
- Included in Penetration Testing Tools: 212 (34.03%)
Conclusion
The number of advisories is steadily increasing month over month - 67 % increase since February 2020. Zero and extremely critical vulnerabilities should be pathed on an emergency basis and shouldn’t wait for a regular patch cycle.
A complete list of vulnerabilities affected versions, criticality, threat score, and relevant patch information are available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera.
- Monthly Vulnerability Insights: October 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: September 2024 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: August 2024 in Software Vulnerability Management Blog
- SVM August 2024 Update in Software Vulnerability Management Release Blog
- Monthly Vulnerability Insights: July 2024 in Software Vulnerability Management Blog