The Community is now in read-only mode to prepare for the launch of the new Flexera Community. During this time, you will be unable to register, log in, or access customer resources. Click here for more information.

- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Manager Knowledge Base
- :
- Advanced & Customized Smart Group Reporting in SVM
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
Question
How do you create reporting only on "Insecure" or "End-Of-Life" statuses in Software Vulnerability Manager? How could you utilize your custom filters across all reporting configurations for tracking only the security statuses you are interested to know more about? This article will help you figure that out.
Answer
The answer is Smart Groups. This is the advanced reporting filtering method of the Software Vulnerability Manager that allows users to select only the specific criteria they like to filter their data against, and the resulted output would translate into customized full report based on the criteria.
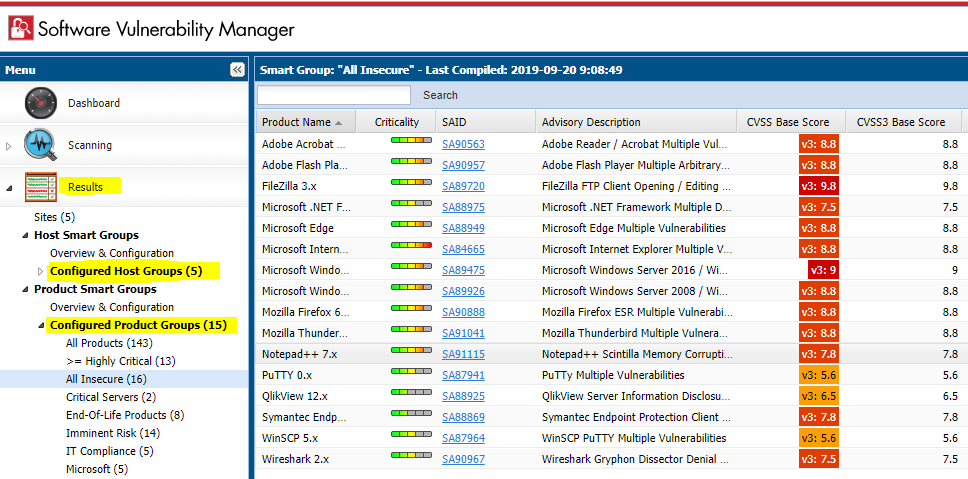
By default, the SVM solution includes default Smart Groups for each Smart Group type. These are:
- "All Hosts" smart group under the "Host Smart Groups" menu.
- "All Products", "All Insecure", "End-of-Life Products" under the "Product Smart Groups" menu.
- "All Advisories" under the "Advisory Smart Groups" menu.
Under each of the main Smart Group categories, you'll find "Overview and Configuration".
This menu lets you create additional Smart Groups based on your custom criteria (Custom SGs).
You have a wide array of choices to pick from in three different criteria categories (host, product, SAID).
Criteria from different categories cannot be mixed up, but the choice is more than enough as it is.
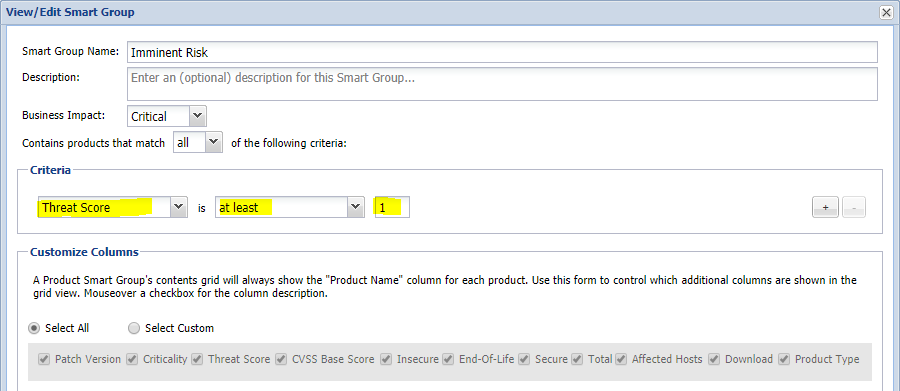
For instance, the following Product Smart Group tracks products which have Threat Intelligence score higher than 0, which in reality represents the applications that carry the imminent risk of exploitation.
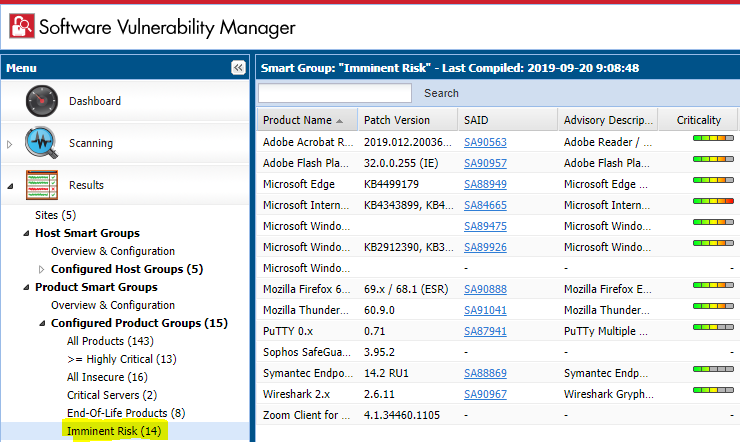
The configuration of this custom smart group is rather simple, but yet so much effective as a filter:
You can find more useful examples of different Smart Group configurations in the Software Vulnerability Manager Best-Practice Guide by Flexera available for download from this direct link at the Flexera Learning Center. You will need to login to the learning center with your Flexera Community account prior to being allowed to download the document.
So far, you've seen examples of using reporting through the core smart group functionality. This already should be helping you establish a routine method of tracking vulnerabilities of high interest to the business, and vulnerabilities with particularly high impact to your environment, by setting the appropriate filters in your groups logically to align with the scenarios you would wish to cover.
But this is not all, not at all!
Limit Dashboard Reporting only to Custom Smart Group filters
As you have created enough useful smart groups, customize your dashboard by building different profiles and saving them accordingly. This will help you switch quickly between management views and gain immediate visibility over your entire estate from different angles to help you prioritize better.
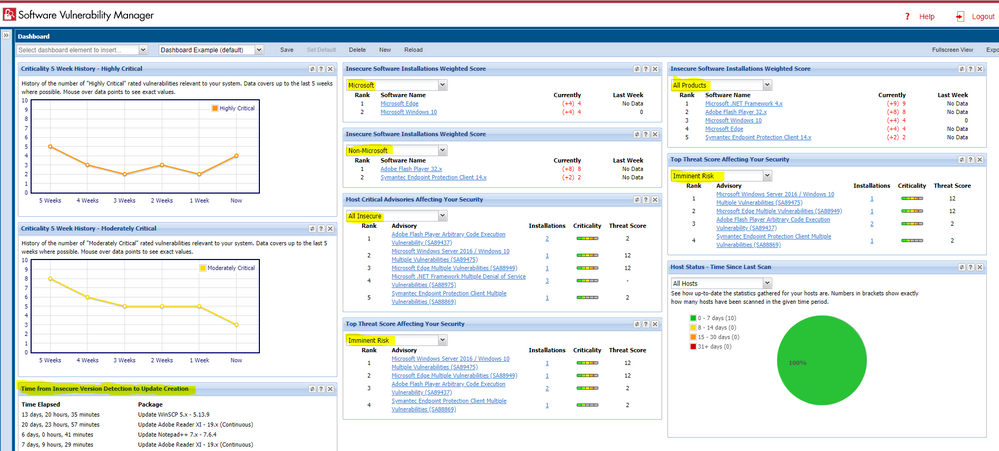
Dashboard Customization Flexibility
You can duplicate portlets when you need the same data for two different filters, or you can use totally different portlets but filter them through the same filter as the next example shows.
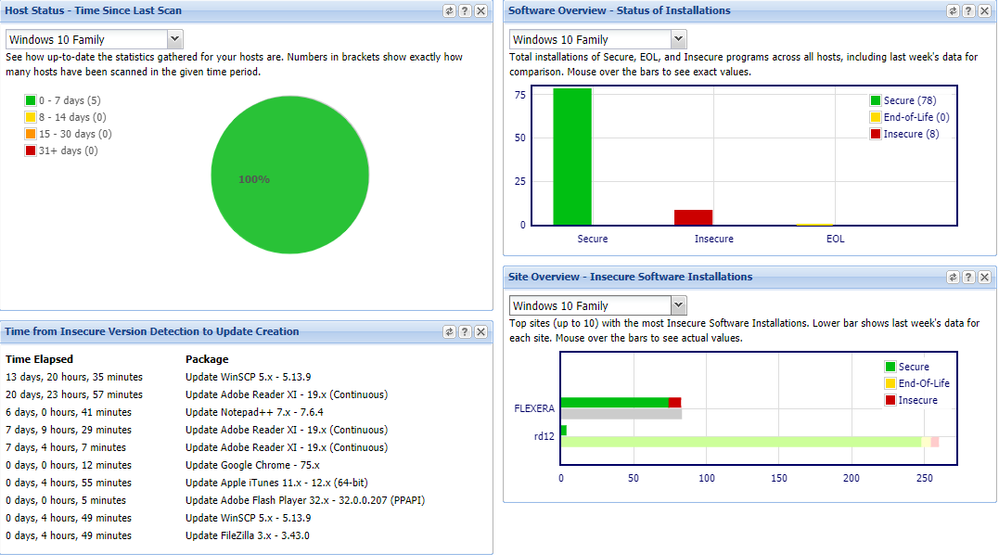
PDF Customization with Smart Groups
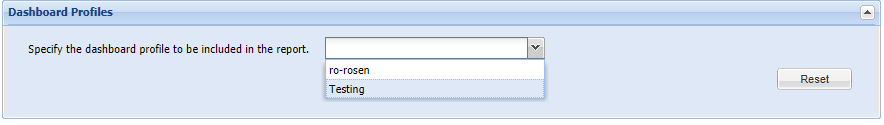
You can similarly to Dashboard customize your PDF reports to only produce the data limited to the criteria of every of your configured Host and Product smart groups. The following visual example shows how to select a Smart Group as a filter, and the rest of the report configuration depends on your needs.
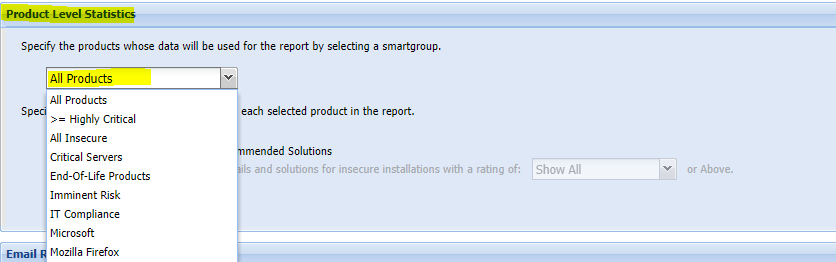
After setting up the preferred Smart Group filter, go ahead and enable the level of details for your programs. Consider how much actual results the Smart Group contains because you would want to avoid issuing a report that has too many details in it against an SG that has too broad criteria applicability. This is mostly useful for concrete filtering and tracking of special cases and scenarios.
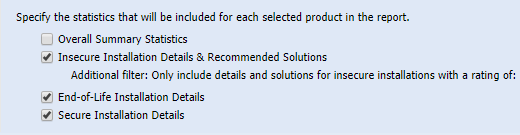
Finally, besides filtering your application details (or host ones if you used Host Smart Group filters instead), you can also include your actual Dashboard profile that stores yet another customized 'picture' of the environment that is utilizing more custom smart filters for maximum report customizations.
These are the basics of achieving a very customized and useful reporting utilizing Smart Groups filters. The rest is entirely up to you to configure as much Smart Groups as you wish for as many scenarios that you find sense to monitor and diligently address. The following additional Appendix includes more useful Smart Group examples to get you started.
Appendix A - More Custom Smart Group Examples
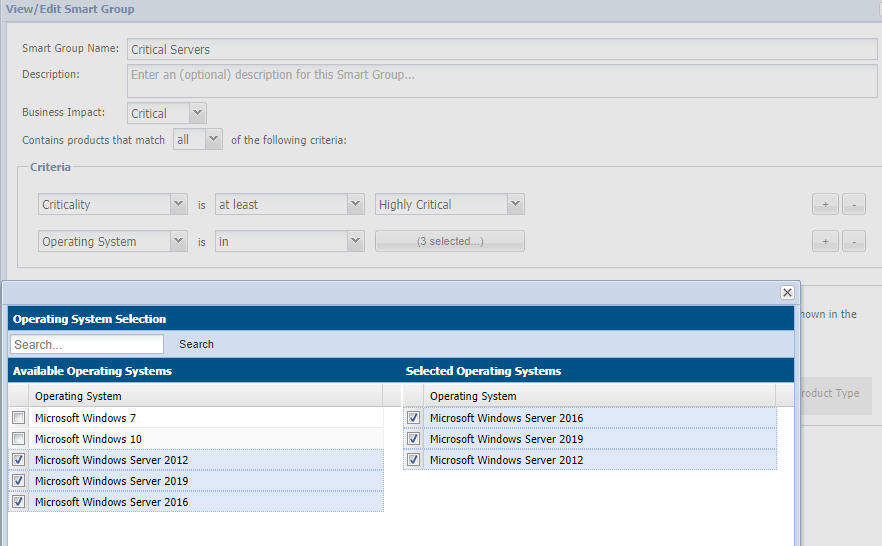
Critical Infrastructure Boundary Example
You can customize reports and dashboards that focus on your critical server infrastructure – vulnerabilities in the underlying Windows OS – using this smart group. To date in 2019, most Zero-Days are found in Microsoft’s OS software. It is critically important to maintain at least one view of those.
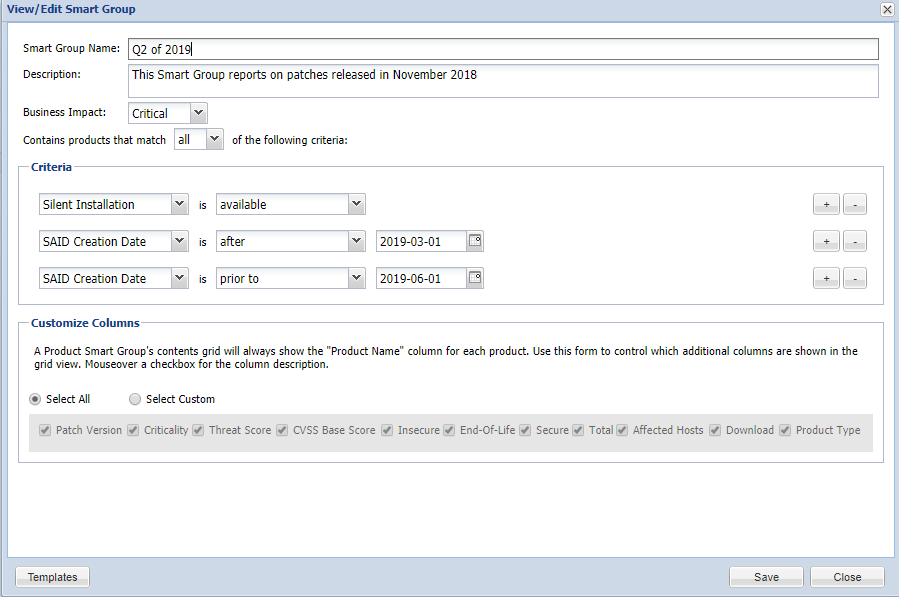
Tracking of Silently Installable Patches released in Q2
You can find out what patches have been released in the Q2 of 2019, or H1/H2, etc. This is a good way to keep track of what have been the latest security patches provided Out-of-the-box in the package system of the SVM, and you can also keep that as a log of the newest released updates (as numbers will update as new versions are released).
IT Compliance Quick Smart Group Configuration
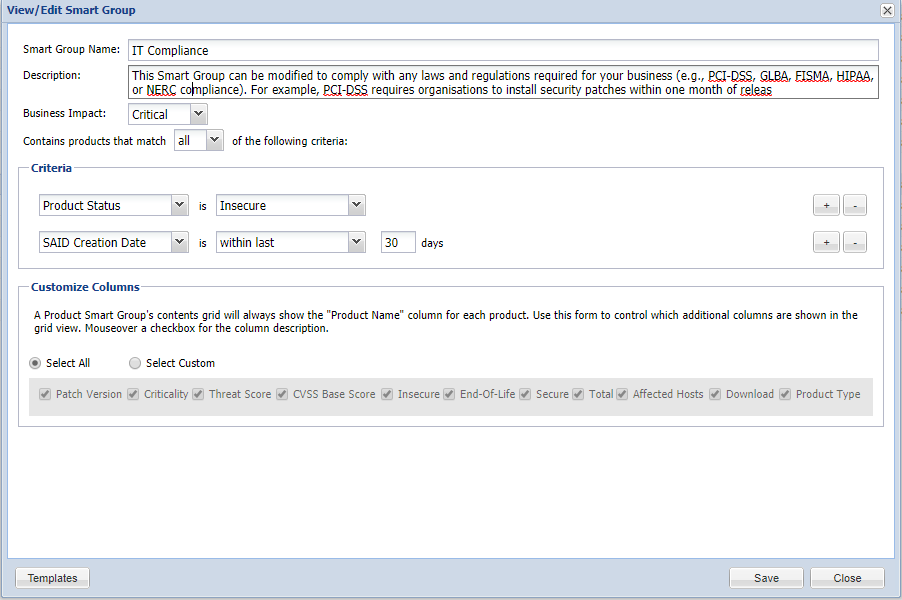 Example of SG configuration that helps you follow up on your compliance statuses
Example of SG configuration that helps you follow up on your compliance statuses
Smart Group for Non-Microsoft Patches
After you configure this group by using the “Not In” condition to remove all Microsoft apps (search for Microsoft, but also Windows for best results), the output will display only your third-party packages.
Therefore, this boundary will allow you to create Dashboards and reports which sum statistics only for third-party software taking Microsoft out of the equation.
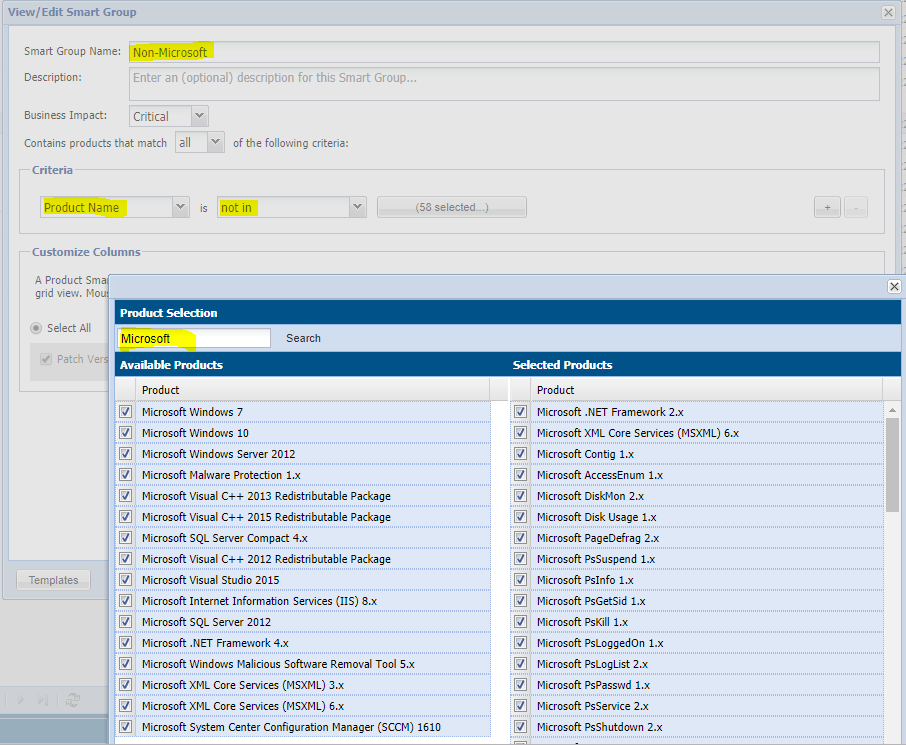
You can create the same SG, but utilize the “In” condition while selecting all the same Microsoft apps, and this other SG will then show only Microsoft programs. Thus, you can switch the filters on the Dashboard to see differences, or simply build and save 2 different Dashboards with your favorite portlets that focus on each of the software types.
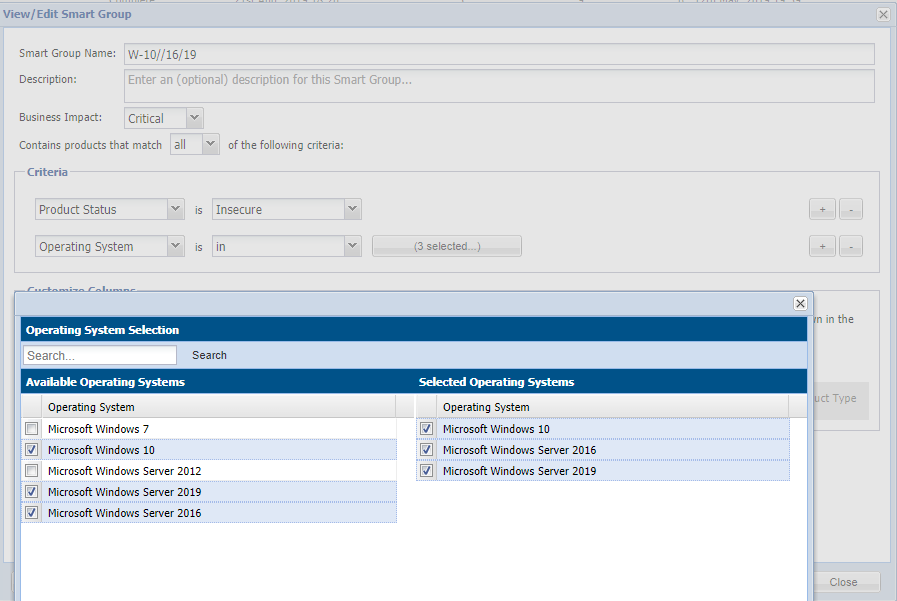
Tracking of Vulnerabilities found on the Windows W10 Platform
This smart group configuration can be helpful to track Windows 10 –level systems and OS vulnerabilities.
Sep 20, 2019 07:20 AM - edited Sep 20, 2019 07:30 AM