
- Flexera Community
- :
- Foundation / CloudScape
- :
- Foundation / CloudScape Release Blog
- :
- Balsam: Product Release Q1 2019
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
More Signal, Less Noise
The power of discovery lies not in confirming what you know, but in understanding what you don't know. Modern IT environments are incredibly complex. Getting the data you need quickly and surfacing mission critical obstacles is paramount to success.
Our team has been heads down over the past quarter making it easier for you to sift through the noise, deliver brand new lines of analysis and visualization, and keep your environment more secure.
Introducing our Balsam Release.
This update includes features to improve discovery, prioritize security threats, and give you the tools to align IT with the business.
Click the links below to learn more about each feature
Security Module
Information without context is just data. Many platforms can deliver you data, we place that data in context.
There is a big difference between:
“My server is connecting to anonymous proxies.”
-and-
“My HR department’s employee database is connecting to anonymous proxies, and Sara owns it.”
We are passionate about delivering meaningful insights to our users. Our new Security Module combines with the context of applications, business services, and departments to make your data actionable.
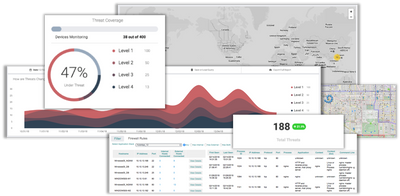
NIST & OVAL Integration
We now integrate into the NIST and CIS OVAL CVE repositories. This enables us to determine vulnerabilities on Linux packages (RHEL, SUSE, Debian, Ubuntu, Oracle, and CentOS).
Geolocation
All incoming and outgoing internet connections will be mapped globally. Understand where your users are, and if they are accessing your applications from high-risk areas or anonymous proxies.
Threat Levels & Reports
Along with a new page for the Threat data, we are introducing a way to rank and prioritize servers in the environment based on their behaviors. E.g. Servers that have existing CVEs with a network attack vector and connect to the internet are of higher priority.
New Dashboard
When it's hard to see the forest for the trees, we raise you above the sprawl to see your environment in ways never before possible.
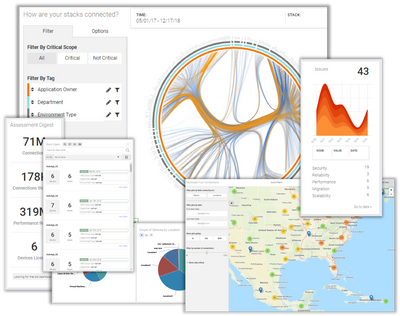
Our new dashboard will present a clearer and more meaningful view of the entire network. We are surfacing metrics about the size of the data lake, how it is changing, and including quick views into threats, stacks, and geolocation.
We believe in making visually compelling experiences for our users to lead to "aha!" moments and drive quicker time to value. Who knew your environment could be so elegant?
The Orb
See the entirety of your environment. Understand which departments, teams, business units are integrated. Understand where you may have risk on personnel or opportunities to share data better.
Assessment and Stack Digests
The size and complexity of your data lake is one of the most important, and hard to understand parts of an assessment. We are providing our users high level overviews of the size of their assessment and how data collection is changing.
Threats & Geolocation
We're placing new features from our Security module on the dashboard to give users quick insight into their threat assessment, as well as provide an interactive map to give visualization to user distribution.
Enhanced Asset Discovery
Discovery is central to RISC Networks' purpose. This key first step begins the transformation of the unknown to the known.
Understanding and managing this transformation can be difficult, time consuming, and frustrating. We are shipping a feature set designed to:
- Save you considerable time by speeding up troubleshooting
- Get better insight into the distribution of devices in your network
- Easily share and report on devices in the environment
Additionally, by scheduling discoveries weekly you can now track and report on changes in the environment for purposes of asset management and cloud migration tracking.
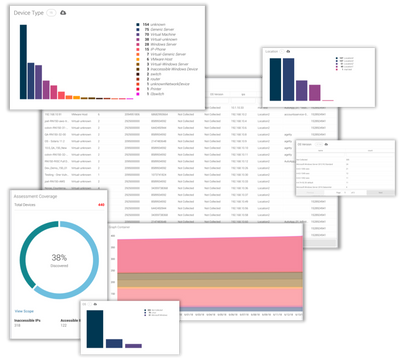
Centralized Reporting
We have brought all your assets to one report for you to quickly search, filter, and report on. We're also introducing the ability for you to save and share your page layouts with other users.
Error & Resolution Page
We created an Assets Errors page to significantly reduce the time it takes to troubleshoot network access. This page will surface all device errors we encounter during discovery. We are also adding a suggested resolution so you can quickly share it the network and server admin teams.
Change Over Time
Know when devices existed and see how your locations, device types, and OS distributions are changing. This will give you visibility into progress toward a migration goal or simply how the environment is changing.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Q1 2022 Releases for Cloud Migration (Foundation/Cloudscape) in Foundation / CloudScape Release Blog
- Dogwood: Product Release Q3 2019 in Foundation / CloudScape Release Blog
- Cedar: Product Release Q2 2019 in Foundation / CloudScape Release Blog
- Aspen: Product Release Q4 2018 in Foundation / CloudScape Release Blog

