A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- Spider
- :
- Spider Knowledge Base
- :
- Flagging Software Products
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Different roles in organizations are responsible for the healthiness of the organizations network infrastructure. From time to time, unwanted software can be discovered, which may harm the network or could violate the company’s legal requirements.
Therefore, responsible employees will have to find ways to identify, asses and if needed to remove the software from the affected devices.
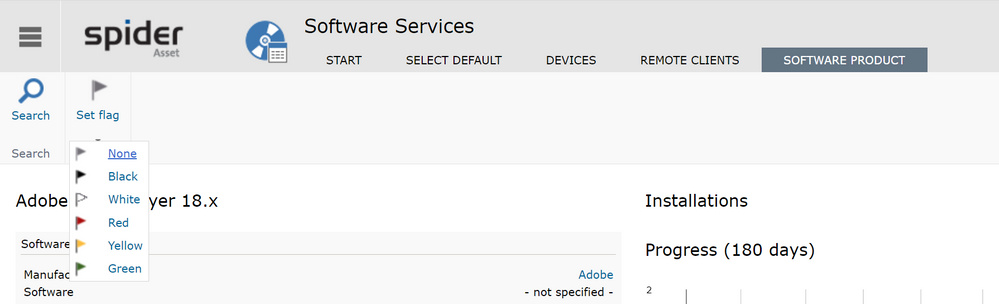
Spider’s capabilities on recognized software products have been enhanced to support the cleaning process for potential vulnerable software. Since Spider 6.4.5, recognized software products can be marked with flags, so that they get a user defined category.
Mark a software product with a specific color simply by choosing one of the flags from the drop down menu in the software products details page.
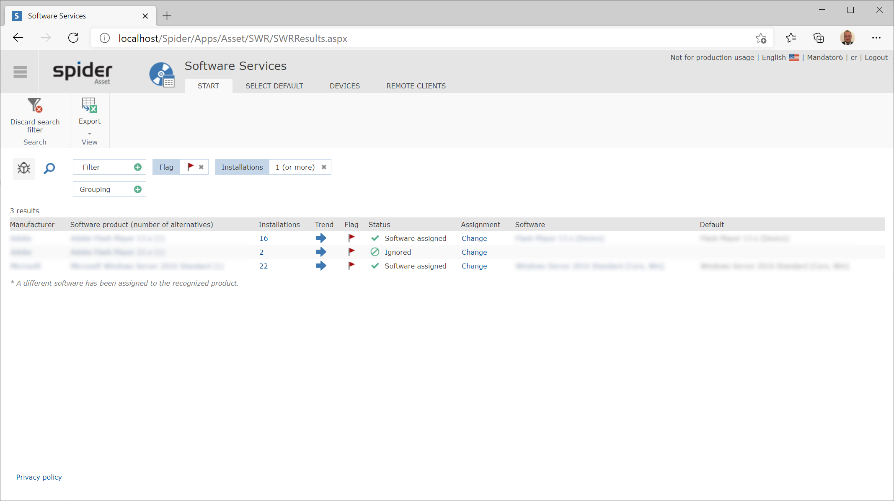
The flags have been integrated to the search page for recognized software products. With that, the software products can be easily filtered to identify risky software installations.
In this example, the search page is filtered for red flagged software products, that have at least one installation.
By doing so, you get a list of red marked software products, so you can iterate easily through the potentially risky installations.
Use cases to considerIn some cases, the SAM manager or the hardware asset manager wants to track specific installed applications for several reasons, e.g. blocked applications or applications that should be updated to a higher version. Categorizing recognized software products to enable, work off and track the classification process my also be an option.
|
There is moreVulnerable installations that may harm your network may not only occur as simple installations. Have you thought about vulnerabilities management? See here how Flexera One is handling these problems https://www.flexera.com/products/software-vulnerability-manager.html |
Jul 01, 2022 09:20 AM