- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review – October till Mid November 2020
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
This review is a combination of advisories issued in September up to mid - November. We want to issue the review in the week of Patch Tuesday as most companies have a patch cycle right after the Patch Tuesday.
In September, Secunia Research at Flexera issued 550 advisories for 317 different products. Up until 15th fo November, 323 advisories for 186 products.
In September, 3 Zero-day advisories in Google Chrome, Microsoft Edge, and FreeType. Up until mid of November, 4 Zero-day advisories were issued
Zero-Day and Highly Critical Vulnerabilities.
Definition of a Zero-day Vulnerability: A zero-day is a vulnerability which is being exploited in the wild on the day or prior its public disclosure. The vulnerability may or may not have a patch.
There is much confusion in security communities
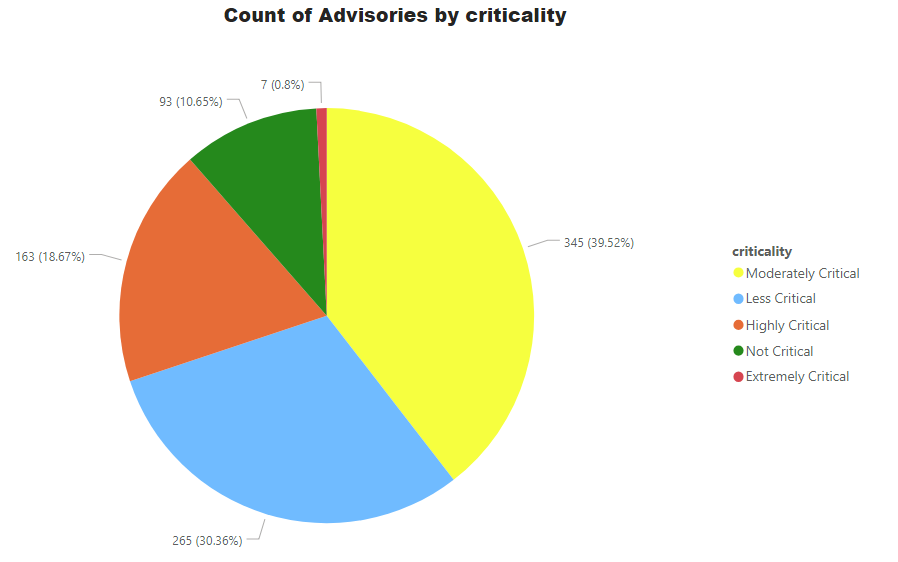
Three zero-day in September and 4 zero-day until Mid-November. 97 highly critical in September and 66 in November so far.
Google Chrome
Three zero-day advisories in two consecutive months. Two zero-days in the first two weeks of November.
In September, a zero-day vulnerability was reported in the version 86.x. Three use-after-free error within media, PDFium, and printing can be exploited to execute arbitrary code. At the time, 86.0.4240.111 was a recommended update. However, another zero-day was reported on November the 2nd and version 86.0.4240.183 was a recommended solution. Yet again, another zero-day was reported on November the 11th in the previous version.
Call to Action: Upgrade to 86.0.4240.198.
Microsoft Edge Chromium
Multiple vulnerabilities were reported in Chromium which can be exploited that can result in system access.
Call to Action: Update to version: 86.0.622.51
Apple IOS and macOS
A zero-day vulnerability related to FontParser can be exploited to execute arbitrary code via a specially crafted font. A vulnerability in facetime can be exploited to send video in group facetime calls without knowing. It is advised to
Call to Action: Upgrade to version 12.4.9
A zero-day vulnerability is reported in the macOS kernel, which can be exploited to disclose memory contents.
Call to Action: Update to macOS Catalina 10.15.7 Supplemental Update, macOS Catalina 10.15.7 Update, Security Update 2020-006 Mojave, or Security Update 2020-006 High Sierra.
Microsoft Windows 7 and Server 2008
Multiple vulnerabilities were reported in Windows 7 and Server 2008, which can be exploited to disclose sensitive version, DOS attack, escalation of privileges and system access.
Call to Action: Install the KB4586827, KB4586805, KB4586807, KB4586817.
Operating Systems:
Secunia advisories for different Operating systems are as below:
- Fedora: 39
- Red Hat Enterprise Linux: 83
- Debian: 21
- Amazon Linux: 64
- Ubuntu: 62
- SUSE Linux: 61
- Oracle Linux: 48
- CentOS Advisories: 7
- Microsoft OS Advisories: 9
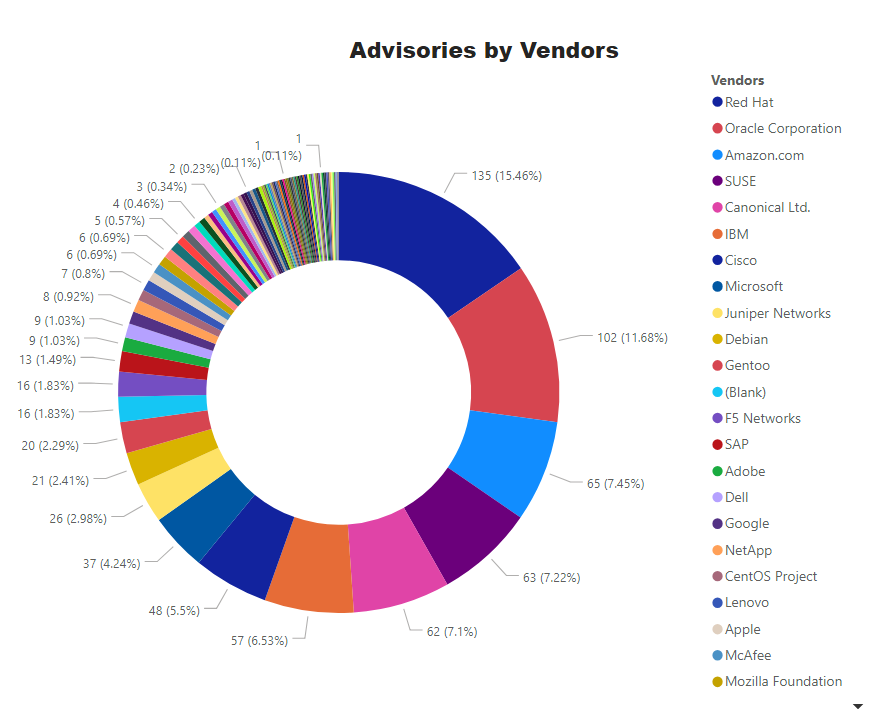
Top Vendors with the most Advisories (September till Mid November)
Advisories for Browsers
- Microsoft Internet Explorer (version 11): 1 Advisory.
- Microsoft Edge (HTML Based - Legacy): 1 Advisory
- Microsoft Edge (Chromium Based): 4 Advisories
- Google Chrome: 7 Advisories
- Mozilla Firefox: 3 Advisories
- Mozilla Thunderbird – 2 Advisory
Microsoft Patch Tuesday - October
On September 8th – Second Tuesday of September, Microsoft issued advisories for these software:
- Microsoft Windows
- Microsoft Office and Microsoft Office Services and Web Apps
- Microsoft JET Database Engine
- Azure Functions
- Open Source Software
- Microsoft Exchange Server
- Visual Studio
- PowerShellGet
- Microsoft .NET Framework
- Microsoft Dynamics
- Adobe Flash Player
- Microsoft Windows Codecs Library
A complete list of all applicable updates for August’s Patch Tuesday is here [1]
Patch Tuesday KBs
A digest of Patch Tuesday is listed here [2]
|
KB Article |
Applies To |
|
Windows 10 Version 1809, Windows Server 2019 |
|
|
Windows 10, version 1903, Windows Server version 1903, Windows 10, version 1909, Windows Server version 1909 |
|
|
Windows 10, version 2004 |
|
|
Windows 10 |
|
|
Windows 10, version 1709 |
|
|
Windows 10, version 1803 |
|
|
Windows 7, Windows Server 2008 R2 (Monthly Rollup) |
|
|
Windows 10, version 1607, Windows Server 2016 |
|
|
Windows 8.1, Windows Server 2012 R2 (Monthly Rollup) |
|
|
Windows Server 2012 (Security-only update) |
|
|
Windows 8.1, Windows Server 2012 R2 (Security-only update) |
|
|
Windows Server 2008 Service Pack 2 (Monthly Rollup) |
|
|
Windows Server 2012 (Monthly Rollup) |
|
|
Windows Server 2008 Service Pack 2 (Security-only update) |
|
|
Windows 7, Windows Server 2008 R2 (Security-only update) |
|
|
Exchange Server 2019, Exchange Server 2016, Exchange Server 2013 |
Microsoft Patch Tuesday - November
On the second Tuesday of November the 10th, Microsoft issued advisories for these software
- Microsoft Windows
- Microsoft Office and Microsoft Office Services and Web Apps
- Internet Explorer
- Microsoft Edge (EdgeHTML-based)
- Microsoft Edge (Chromium-based)
- ChakraCore
- Microsoft Exchange Server
- Microsoft Dynamics
- Microsoft Windows Codecs Library
- Azure Sphere
- Windows Defender
- Microsoft Teams
- Azure SDK
- Azure DevOps
- Visual Studio
|
KB Article |
Applies To |
|
4486714 |
SharePoint Server 2019 |
|
4486717 |
SharePoint Server 2016 |
|
4586781 |
Windows 10, version 2004, Windows Server version 2004, Windows 10, version 20H2, Windows Server version 20H2 |
|
4586786 |
Windows 10, version 1903, Windows Server version 1903, Windows 10, version 1909, Windows Server version 1909 |
|
4586793 |
Windows 10 Version 1809, Windows Server 2019 |
|
4586805 |
Windows 7, Windows Server 2008 R2 (Security-only update) |
|
4586807 |
Windows Server 2008 (Monthly Rollup) |
|
4586808 |
Windows Server 2012 (Security-only update) |
|
4586817 |
Windows Server 2008 (Security-only update) |
|
4586823 |
Windows 8.1, Windows Server 2012 R2 (Security-only update) |
|
4586827 |
Windows 7, Windows Server 2008 R2 (Monthly Rollup) |
|
4586830 |
Windows 10, version 1607, Windows Server 2016 |
|
4586834 |
Windows Server 2012 (Monthly Rollup) |
|
4586845 |
Windows 8.1, Windows Server 2012 R2 (Monthly Rollup) |
|
4486714 |
SharePoint Server 2019 |
|
4486717 |
SharePoint Server 2016 |
|
4588741 |
Microsoft Exchange Server 2013, Microsoft Exchange Server 2016, Microsoft Exchange Server 2019 |
|
|
|
|
|
|
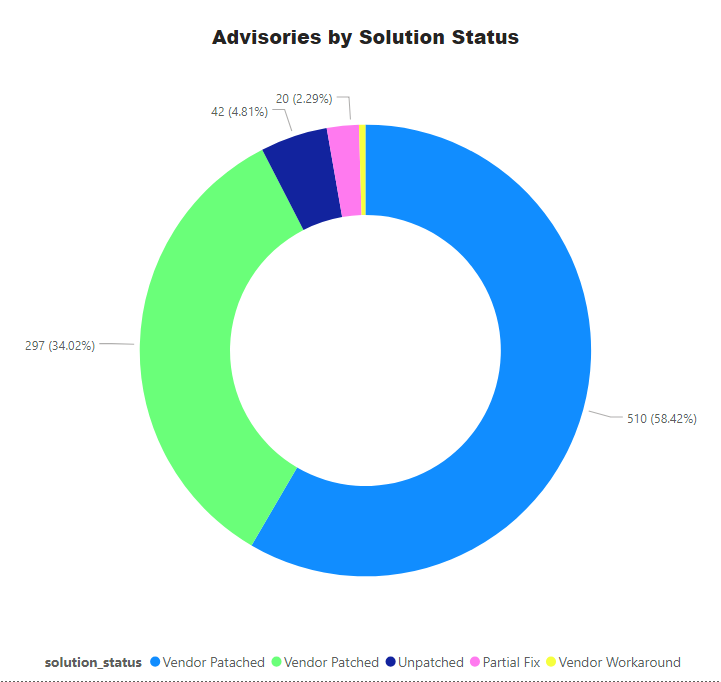
Advisories by Average CVSS Score
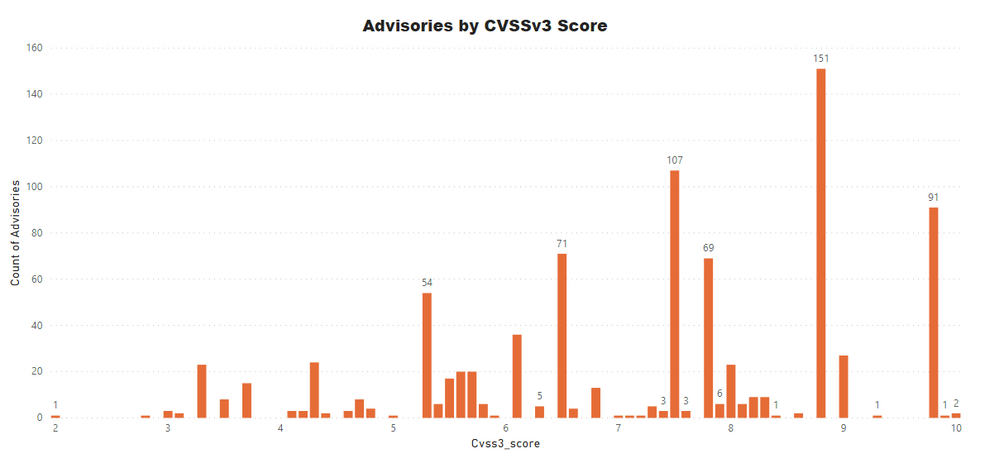
A CVSS score is a metric used to measure the severity of a vulnerability. CVSS v3 specifications and the criteria details are at this link.
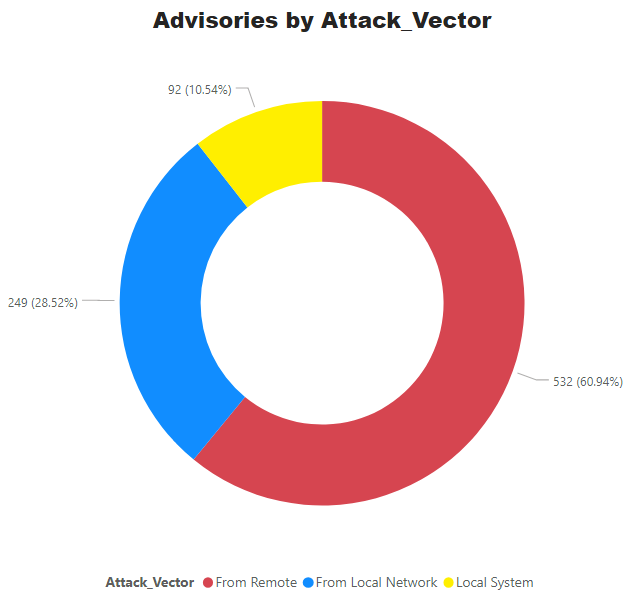
CVSS ranges from 0 to 10. 0 being the lowest and 10 being the highest score; the advisories spread is as below:
CVSS 3 Score
- Advisories with Low CVSS3 under 4.0: 53 (6.07%)
- Advisories with Mid CVSS3 range 4-7: 301 (34.48%)
- Advisories with High CVSS3 range 7-10: 519 (59.45%)
Threat Score
Threat score is calculated based on criticality and its linkage to a recent or historical threat of either remote trojan horse, ransomware, used in penetration testing tools, availability of exploit kit, and cyber exploit. Each rule triggers an increase in the threat value. A detailed explanation of Threat Score calculation is available at this link.
- Advisories with positive Threat Score (1+): 591 (67.70%)
- None Threat Score SAIDs (=0): 282 (32.30%)
- Low-Range Threat Score SAIDs (1-12): 150 (17.18%)
- Medium-Range Threat Score SAIDs (13-23): 393 (45.02%)
- High-Range Threat Score SAIDs (24-44): 33 ( 3.78%)
- Critical-Range Threat Score SAIDs (45-70): 5 ( 0.57%)
- Very Critical Threat Score SAIDs (71-99): 10 ( 1.15%)
Ransomware, Malware, and Exploit Kits:
.
- Historically Linked to Ransomware: 10 (1.15%)
- Historically Linked to Malware: 108 (12.37%)
- Linked to a Recent Cyber Exploit: 188 (21.53%)
- Related to a Historical Cyber Exploits: 341 (39.06%)
- Included in Penetration Testing Tools: 399 (45.70%)
Conclusion
The number of vulnerabilities is increasing, so we need to leverage threat intelligence to prioritize the patching effort. Install Patch Tuesday as soon as possible after testing it. Zero-days should be delayed, and an emergency change request/window should be introduced.
A complete list of vulnerabilities, affected software, criticality, threat score, and relevant patch information is available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera. Stay Secure!
References:
[2] https://msrc.microsoft.com/update-guide/releaseNote/2020-Oct
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Monthly Software Vulnerability Insights - November 2023 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - October 2023 in Software Vulnerability Management Blog
- 2022 Flexera Annual Vulnerability Review Report in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: December 2022 in Software Vulnerability Management Blog
- Monthly Vulnerability Insights: November 2022 in Software Vulnerability Management Blog