- Flexera Community
- :
- FlexNet Manager
- :
- FlexNet Manager Knowledge Base
- :
- How do I generate my own signed certificate for use with Beacon Monitor?
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
- Article History
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Introduction
The built-in functionality of BeaconMonitorConfigurationTool.exe bundled with Beacon Monitor, is enough for simple certificate management:
- to generate a self-signed certificate and private key pair.
- to generate a key file, then using OpenSSL (using openssl req: generate a certificate signing request (CSR).
However, for more control over generating the certificate it may be preferable or offer greater flexibility, to use a 3rd party tool such as OpenSSL to generate the request. Other tools are also possible, but for the purposes of this guide OpenSSL is primarily used and the CA is Windows Certification Authority.
OpenSSL can be installed easily using Chocolately package manager (https://chocolatey.org/install) or installed manually, to install OpenSSL using Chocolately:
choco install openssl
Outcome
The outcome of this should be a CA-signed certificate and key pair:
- The key should be generated in PKCS#8 format, other formats such as PKCS#1 are unsupported.
- The certificate should not be encrypted.
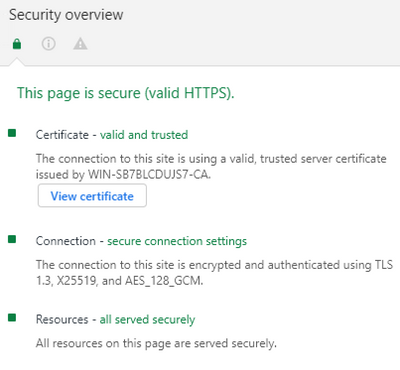
The result should be a 'valid and trusted certificate' and no warning related to the certificate in any supported browser:
Procedure
- Open a PowerShell window and create a new folder for the new key, cert, etc:
New-Item -ItemType Directory mycert
Set-Location mycert - Create an OpenSSL config file (config.cnf) in the same directory with the contents, adjust as appropriate:
[req_distinguished_name] countryName = GB stateOrProvinceName = Merseyside localityName = Cheshire organizationName = Flexera commonName = mybeacon.flexera.com [req] distinguished_name = req_distinguished_name default_bits = 2048 req_extensions = v3_req prompt = no [v3_req] basicConstraints = CA:FALSE keyUsage = nonRepudiation, digitalSignature, keyEncipherment subjectAltName = @alt_names [alt_names] DNS.1 = mybeacon.flexera.com
- Generate a new PKCS#8 private key:
openssl genpkey -out key.pem -algorithm RSA -pkeyopt rsa_keygen_bits:2048
Alternatively use BeaconMonitorConfigurationTool.exe to generate the key (delete cert.pem after running):.\BeaconMonitorConfigurationTool.exe generate-cert -ca false
- Create the certificate signing request (CSR):
openssl req -new -out server.req -key key.pem -config config.cnf
-
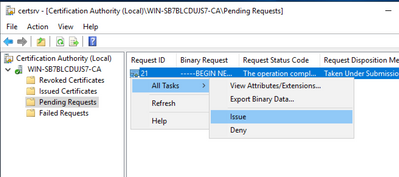
Copy the server.req to the CA and issue the certificate:
-
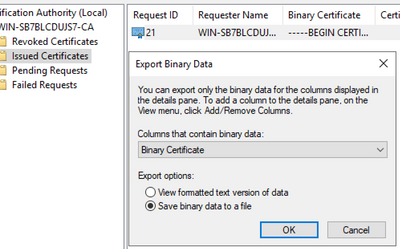
Export the Binary Certificate as server.cer:
- Copy the certificate back to the Beacon Monitor and use OpenSSL to change the encoding from binary DER to ASCII PEM:
openssl x509 -inform der -in server.cer -out cert.pem
-
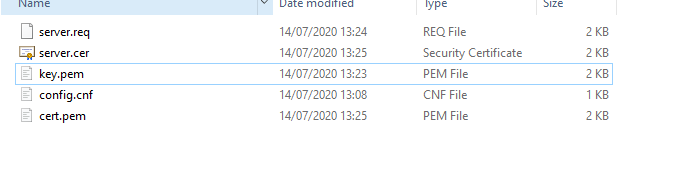
You should have the following files when you're done. You need cert.pem and key.pem:
- Copy the files to the Beacon Monitor Certificate folder and restart the service, check that the certificate now shows as valid and trusted. If it does not, there could be several reasons (this list is not exhaustive):
- The CA may not be trusted by the accessing client machine.
- The common name in the certificate is different to the domain in the URL, and the name is also missing from the Subject Alternative Name (SAN). For example if the machine's IP and not hostname is used to access the Beacon Monitor and the IP is not present in the certificate then this will generate a certificate warning.
- The date on the certificate has expired or is not valid yet.
- The CA has revoked the certificate and the CA has a Certificate Revocation List (CRL) which is accessible.
- The certificate algorithm is not considered secure by the browser.
Jul 16, 2020 07:14 AM - edited Jul 16, 2020 07:17 AM