A new Flexera Community experience is coming on November 25th. Click here for more information.

- Flexera Community
- :
- AdminStudio
- :
- AdminStudio and Workflow Manager Release Blog
- :
- AdminStudio Feature Update for Log4j Detection
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
After the recently disclosed Apache Log4j critical vulnerability, the most important question everyone is trying to find an answer for is – are there any applications in my portfolio that are impacted by this log4j vulnerability?
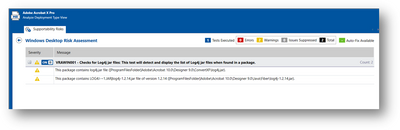
The AdminStudio Feature Update released today adds a new rule for detecting the log4j jar files within a package. This new rule is added under the Windows Risk Assessment test category. To check if a package has log4j jar files, select this rule and click on Execute Tests button in the ribbon bar of Analyze tab. When log4j jar files are found in the package, AdminStudio will display a warning message. You will see the version and installation path of the log4j file in the warning message if it is possible to fetch the information from the package. Based on the version of the log4j found in a package, you must further assess if the disclosed vulnerability applies to the detected version.
For certain packages, AdminStudio may not extract all the information that is required to check for the presence of log4j files, for such packages, a warning message will be displayed to alert you that the assessment was incomplete. It is advised you take a different approach for assessing such packages.
This update is released for AdminStudio 2021, AdminStudio 2021 R2, and AdminStudio 2021 R2 Service Pack 1. You will be able to download the update patch file from the Product and License Center. Please follow the below steps to download and apply the patch on AdminStudio:
- Login to Product and License Center and download the update patch file (.exe) and the SQL script file (.sql). Please refer to the table below to identify the correct patch file name and the SQL script file applicable for your version of AdminStudio:
| Version | Patch File Description | Patch File Name (.exe) | SQL Script File Description | SQL Script File Name (.sql) |
| AdminStudio 2021 | AdminStudio 2021 Log4j Patch | AdminStudio2021Log4jPatch.exe | AS2021R2 Log4j Rule Script | AS2021R2Log4jRuleScript.sql |
| AdminStudio 2021 R2 | AdminStudio 2021 R2 Log4j Patch | AdminStudio2021R2Log4jPatch.exe | AS2021R2 Log4j Rule Script | AS2021R2Log4jRuleScript.sql |
| AdminStudio 2021 R2 Service Pack 1 | AdminStudio 2021 R2 SP1 Log4j Patch | AdminStudio2021R2SP1Log4jPatch.exe | AS2021R2 SP1 Log4j Rule Script | AS2021R2Log4jRuleScript.sql |
The below screenshot shows the patch and SQL script files for AdminStudio 2021 R2 and AdminStudio 2021 R2 SP1:
- On the SQL Server, where the AdminStudio catalog is hosted, execute the SQL script file (.sql) applicable to your version of AdminStudio. This script will add the new rule for checking log4j files in the catalog.
- On the AdminStudio installed machine, close AdminStudio Application Manager and stop the AdminStudio Host process from the System Tray
- Install the downloaded patch file (.exe) applicable to your version of AdminStudio.
- Start AdminStudio Application Manager and connect to the catalog.
- A new rule for detecting Log4j files should now be available under the Windows Risk Assessment category. It is important to note that this new rule can be executed only on the packages which are imported into the catalog after this update patch is installed on AdminStudio.
At this point, our goal was to give a quick solution to help you detect log4j vulnerable files in the packages you manage for your immediate attention. We will continue monitoring updates on this vulnerability and add enhancements to this solution as and when applicable.
For the status of impacted Flexera products, please see this announcement.
- AdminStudio 2024 R2 in AdminStudio and Workflow Manager Release Blog
- AdminStudio 2024 in AdminStudio and Workflow Manager Release Blog
- Information on FLEXnet Connect Servers Unavailable Notification in AdminStudio's 'Check for Updates’ feature in AdminStudio Knowledge Base
- AdminStudio 2023 R2 Service Pack 1 in AdminStudio and Workflow Manager Release Blog
- AdminStudio 2023 in AdminStudio and Workflow Manager Release Blog