- Revenera Community
- :
- FlexNet Operations
- :
- FlexNet Operations Forum
- :
- Re: decrypting signed_access_request response
- Mark Topic as New
- Mark Topic as Read
- Float this Topic for Current User
- Subscribe
- Mute
- Printer Friendly Page
- Mark as New
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
I am trying to use the signed_access_request endpoint of the cloud licensing server. It is working and returning me a json object with encrypted values. However, I am unable to decrypt them. I am attempting to follow along with CMAPI_UsersGuid chapter 4 "Sample Implementation for Validating Responses" but am getting "ValueError: Could not deserialize key data".
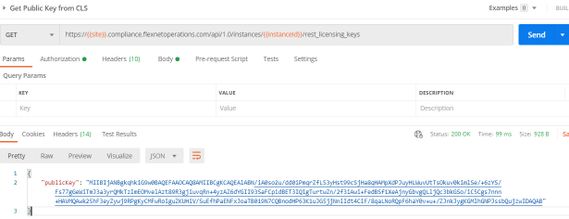
I suspect that I don't have the public key setup correctly for this example code. When I ran my post to rest_licensing_keys, and later a get as well, I got back a json response
{
"publicKey": "VALUE REDACTED"
}
What format is VALUE in? How do I need to convert it to a pem file for the script used in chapter 4?
Thanks for your help.
- Mark as New
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
Hi @mwilliams1 ,
The GET on the /rest_licensing keys endpoint will provide you with the public key that you will used to authenticate the signed responses from server. You should see something similar to:
You will need to save this public key in .pem format which has begin and end public key header and footer tags like the following example:
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAlABN/iA0so2u/dd0iPmqrZfL53yHst99cSjHa8qHAMpXdPJuyHLWuvUtTsOkuv0kimlSe/+6zYS/Fs77gGeWiTmJ3a3yrQMkTzImEOMvelAzt89R3gjiuvqRn+4yzAZ6dYGII93SaFCpidBET3IQigTurtwZn/2f3iAwi+FedBSf1XeAjnyGbvgQLljQc3bkGSo/iC5Cgs7nnn+HAVMQAwk25hF3eyZywj9RPgKyCMFwRoiguZKUHiV/SuEfhPaENFxJoaTB019N7CQBnodHP63K1uJG5jjNniIdt4CiF/8qaLNoRQpF6haY0v+u+/ZJnkJygKGMlhGNPJssbQujzwIDAQAB
-----END PUBLIC KEY-----
Let's call this file public.pem
You then perform your signed access request and get a response similar to:
Save this response to a file, let's call it response.json
Now you should be able to run the python example code to validate the response. Let's call the script Validate.py
python .\Validate.py .\public.pem .\response.json
In my case the raw output is:
b'{\n "requestHostId" : {\n "value" : "JBerthold",\n "type" : "USER"\n },\n "features" : [ {\n "name" : "F1",\n "version" : "1.0",\n "count" : 1,\n "expires" : "2020-11-16T22:53:58.000Z",\n "finalExpiry" : "2023-10-05",\n "vendorString" : "22b5-0d6f-e208-44ab-b1f9-b4dc-c2d0-04f7"\n } ],\n "statusList" : [ ]\n}'
Hope that helps.
Thanks,
Jim
- Mark as New
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
Hi @mwilliams1 ,
There is a recent post that discusses the CMAPI, please see if it helps you out.
Thanks,
Jim
- Mark as New
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
Hi @mwilliams1 ,
The GET on the /rest_licensing keys endpoint will provide you with the public key that you will used to authenticate the signed responses from server. You should see something similar to:
You will need to save this public key in .pem format which has begin and end public key header and footer tags like the following example:
-----BEGIN PUBLIC KEY-----
MIIBIjANBgkqhkiG9w0BAQEFAAOCAQ8AMIIBCgKCAQEAlABN/iA0so2u/dd0iPmqrZfL53yHst99cSjHa8qHAMpXdPJuyHLWuvUtTsOkuv0kimlSe/+6zYS/Fs77gGeWiTmJ3a3yrQMkTzImEOMvelAzt89R3gjiuvqRn+4yzAZ6dYGII93SaFCpidBET3IQigTurtwZn/2f3iAwi+FedBSf1XeAjnyGbvgQLljQc3bkGSo/iC5Cgs7nnn+HAVMQAwk25hF3eyZywj9RPgKyCMFwRoiguZKUHiV/SuEfhPaENFxJoaTB019N7CQBnodHP63K1uJG5jjNniIdt4CiF/8qaLNoRQpF6haY0v+u+/ZJnkJygKGMlhGNPJssbQujzwIDAQAB
-----END PUBLIC KEY-----
Let's call this file public.pem
You then perform your signed access request and get a response similar to:
Save this response to a file, let's call it response.json
Now you should be able to run the python example code to validate the response. Let's call the script Validate.py
python .\Validate.py .\public.pem .\response.json
In my case the raw output is:
b'{\n "requestHostId" : {\n "value" : "JBerthold",\n "type" : "USER"\n },\n "features" : [ {\n "name" : "F1",\n "version" : "1.0",\n "count" : 1,\n "expires" : "2020-11-16T22:53:58.000Z",\n "finalExpiry" : "2023-10-05",\n "vendorString" : "22b5-0d6f-e208-44ab-b1f9-b4dc-c2d0-04f7"\n } ],\n "statusList" : [ ]\n}'
Hope that helps.
Thanks,
Jim
- Mark as New
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
As an aside, I think you guys should update your example in this section to add an exp in the JWT we generate.