- Revenera Community
- :
- Code Insight
- :
- Code Insight Knowledge Base
- :
- How do I enable SSL for FlexNet Code Insight?
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
How do I enable SSL for FlexNet Code Insight?
How do I enable SSL for FlexNet Code Insight?
Summary
This article provides instructions for enabling SSL.Synopsis
This article provides instructions for...
- Generating a key and keystore with the keytool command
- Configuring FlexNet Code Insight to use SSL with the keystore
- Purchasing a certificate from a Certificate Authority
- Using a self-signed certificate
Discussion
Generate a key and keystore with the keytool command
-
Generate a new keystore with a private key. The keystore and key passwords must be the same.
cd <palamida>/tomcat keytool -genkey -alias palamida -keyalg RSA -keystore palamida.jks -keysize 2048 -
After entering the password, you need to have the value of the hostname for the value of first and last name:
What is your first and last name? Unknown: <fully-qualified-network-accessible-hostname-of-core-server> eg. palamidacore.corp.com - Be sure to make a backup of the keystore. cp -i palamida.jks palamida.jks.originalKey
Configure Palamida to use SSL with the keystore
-
Copy the example SSL Tomcat configuration to tomcat/conf
cp -i conf/server.xml conf/server.xml.backup cp https/server.xml conf/server.xml -
Edit conf/server.xml with the keystore settings:
keystoreFile="palamida.jks" keyAlias="palamida" keypass="<your keystore/key password>"NOTE: If using Palamida 6.6.x, use keystorePass instead of keypass. Also, see this article to avoid Diffie-Hellman errors.
keystorePass="<your keystore/key password>" -
Edit bin/catalina.sh to turn on SSL in the Palamida application in the $JAVA_OPTS:
-Dpalamida.ssl=true -
Edit $palamida/config/core/core.properties to use https URLs.
If this is the core server:
core.server.url = https://palamidacore.corp.com:8888/palamida/If this is a scan server:
scan.server.<ALIAS>.web = https://palamidascan.corp.com:8888/palamidaScanEngine
To purchase a certificate from a Certificate Authority
NOTE: Before you import your purchased certificate into the keystore, you may need to import the certificate vendor's chain of trust. Consult your vendor's instructions (for example, Entrust certificates).
-
Generate a signing request from the keystore that you created above.
keytool -certreq -file palamida.csr -alias palamida -keystore palamida.jks -
Send the palamida.csr file to your certificate authority. Place the certificate file returned by the authority palamida.crt in $palamida/tomcat and import it into the keystore.
keytool -import -file palamida.crt -trustcacerts -alias palamida -keystore palamida.jks
To use a self-signed certificate
NOTE: This applies only if you did not purchase a certificate as above.
-
Export the public certificate from the keystore that you created above:
keytool -export -file palamida.crt -alias palamida -keystore palamida.jksAlternatively, users can use openssl to obtain the certificate if the server is running. For example:
openssl s_client -connect palamida.corp.com:8888 -showcerts < /dev/null > palamida.crt -
Send the palamida.crt file to all users who will access the system. They will need to import that certificate in order to access Palamida.
-
Import the certificate to the browser or system key database to avoid browser warning.
For Windows users:
Open your web browser's advanced security settings and import the certificate into the browser's keystore as a trusted certificate.
For Mac users:
(a). Open Applications > Utilties > Keychain Access and import the palamida.crt file into the login certificate keychain:
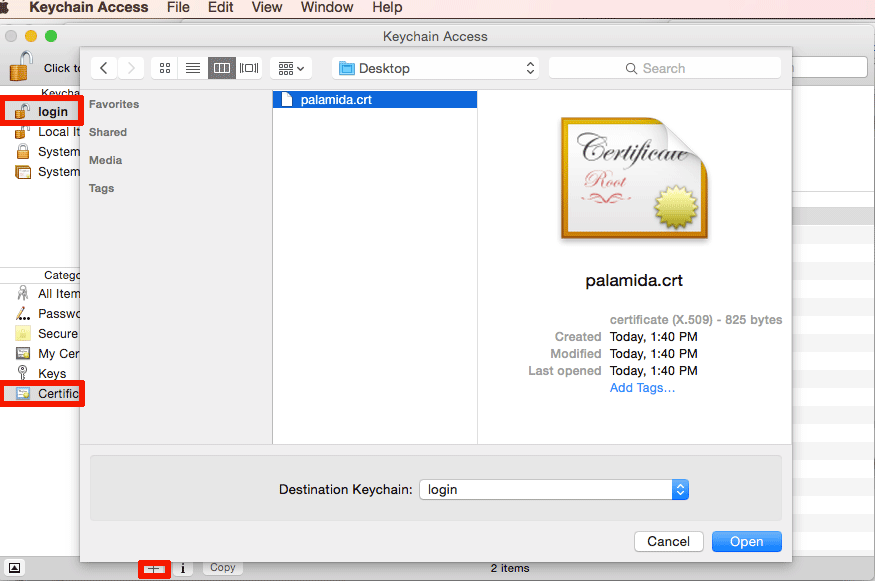
(b). When prompted, click Always Trust.
(c). Open the imported certificate and specify Always Trust for SSL:
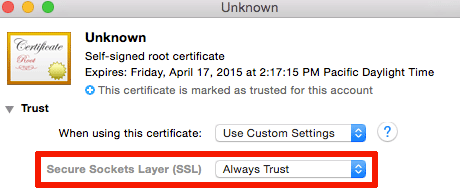
-
For client machines that will access the Detector application, they must import the certificate to the cacerts file in their Java JRE installation.
For Windows users:
(a). Locate the JRE installation, for example C:\Program Files\Java\jre7 and place the palamida.crt file in the lib\security sub-directory.
(b). Run cmd as Administrator and import the certificate:
cd "C:\Program Files\Java\jre7" cd lib\security copy cacerts cacerts.original ..\..\bin\keytool -import -file palamida.crt -keystore cacerts -storepass changeitType yes when prompted to trust the certificate.
For Mac/Linux users:
(a). Locate the JRE installation, for example /Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home and place the palamida.crt file in the lib/security sub-directory.
(b). Open a terminal and import the certificate:
cd "/Library/Internet Plug-Ins/JavaAppletPlugin.plugin/Contents/Home" cd lib/security sudo cp -i cacerts cacerts.original sudo ../../bin/keytool -import -file palamida.crt -keystore cacerts -storepass changeitType yes when prompted to trust the certificate.
For users of Palamida 6.8 and later:
It is also necessary to import the certificate to the cacerts file in the Java JDK installation on the Core and Scan servers (in standalone installations, of course, there will be only one JDK). This can be done with the following commands:
cd $JAVA_HOME/jre/lib/security sudo cp -i cacerts.original sudo ../../bin/keytool -import -alias palamida -file palamida.crt -keystore cacerts -storepass changeit
Additional Information
- see $palamida/tomcat/https/readme.txt in the application folder.
- see the Apache Tomcat documentation for generating a Java keystore.
- you can set a JRE runtime parameter on client machines to use a specific cacerts file:
-Djavax.net.ssl.trustStore=/path/to/cacerts - to debug certification path issues you can set the runtime paratmers:
-Djava.security.debug=certpath -Djavax.net.debug=trustmanager