- Flexera Community
- :
- Flexera One
- :
- Flexera One Knowledge Base
- :
- Configure Okta for SSO access to Flexera One
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Configuring Okta for single sign-on (SSO) to Flexera One allows you to access Flexera One through Okta using the same set of login credentials. This improves usability, security, regulatory compliance, and makes application access and password management easier to control.
Create a SAML application
- Log in to Okta’s Administrator Console using your Okta account’s administrator credentials.
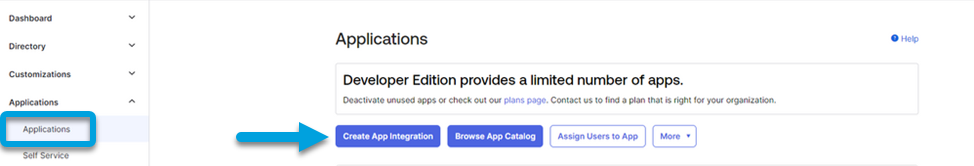
- Click Applications, then select Applications from the dropdown menu.
- Select Create App Integration.
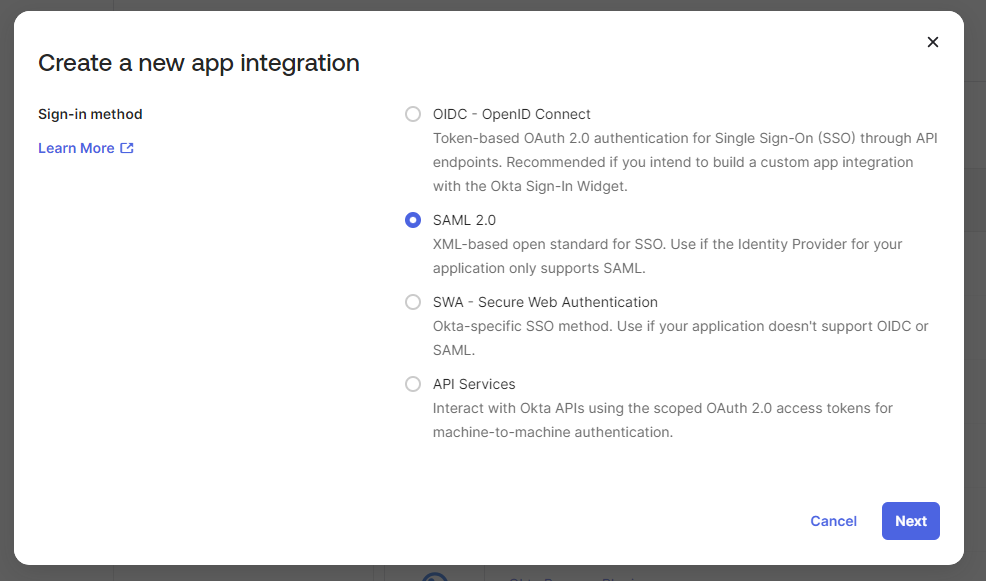
- Select SAML 2.0 from the Sign-in method options and click Create.
- On the Create SAML Integration screen’s General Settings section, complete and save the following fields:
- App name
- App logo (optional)
- App visibility
- Click Next.
Configure SAML settings
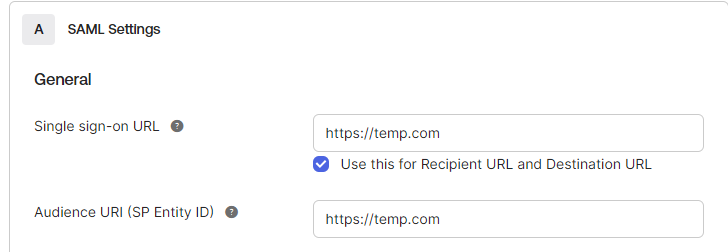
- Enter temporary values for Single sign-on URL and Audience URI (SP Entity ID)
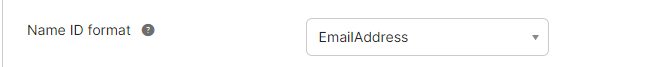
- Set the Name ID format to EmailAddress.
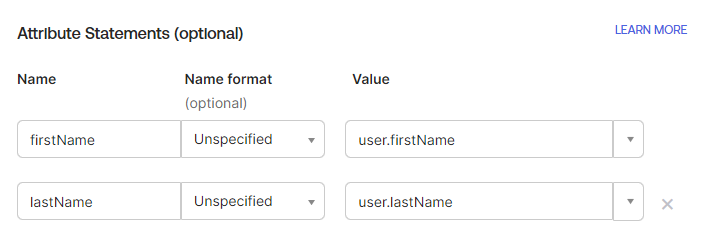
- Replace the fields firstName and lastName with your name. This allows you to enable Just-in-Time (JIT) Provisioning.
NOTE: JIT Provisioning automates user creation and Group Sync to synchronize groups from their Identity Providers (IdP) to Flexera One, automatically adding users to Flexera One when they log in.
- In the Feedback section, select I'm an Okta customer adding an internal app then click Finish
Create an identity provider
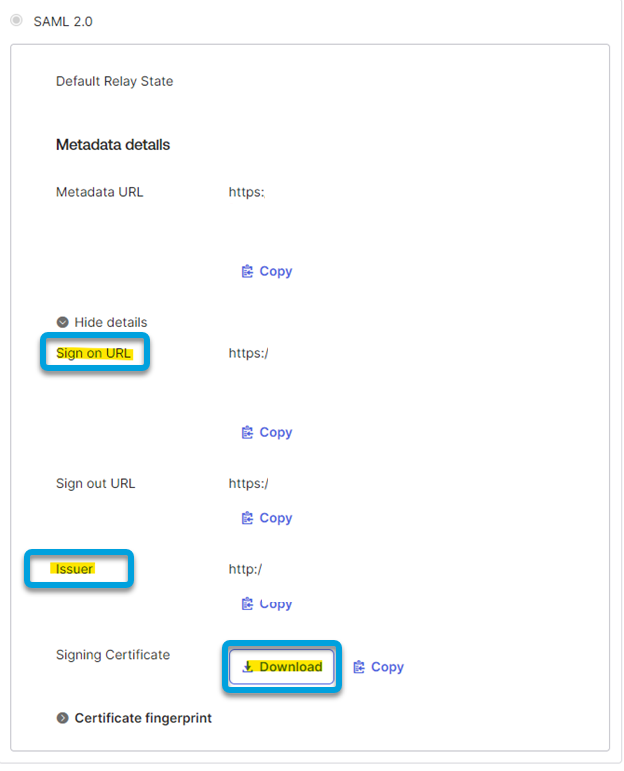
- Expand the SAML 2.0 section to see all the metadata details. Copy the Sign-on URL and Issuer and then download the Signing Certificate.
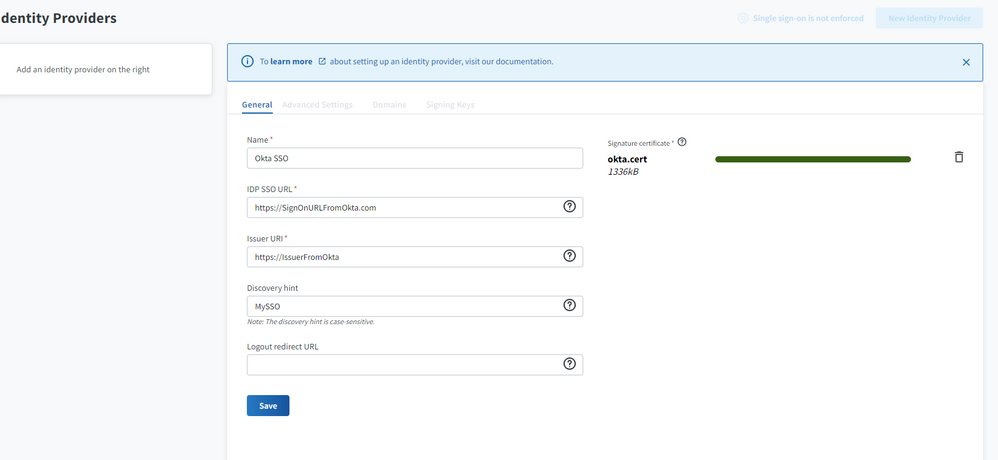
- Navigate to Administration > Identity Providers.
- Enter a name for your provider. In the IDP SSO URL field, enter the Sign-on URL you copied earlier. Repeat this step for the Issuer URI field.
-
NOTE: You can also enter a Discovery hint, which will be used to initiate SSO from the Flexera One login page, and a Logout redirect URL, where the user will be redirected to when they log out of Flexera One if they signed in with SSO.
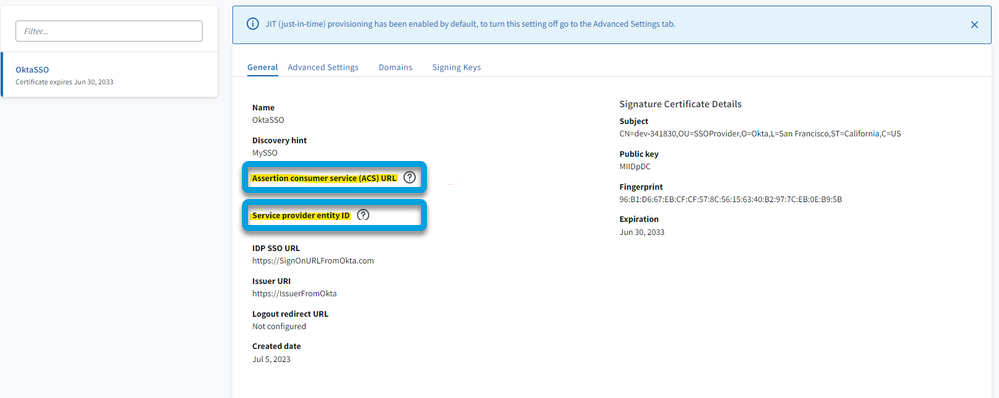
- To the right, upload the Signing Certificate you downloaded from Okta.
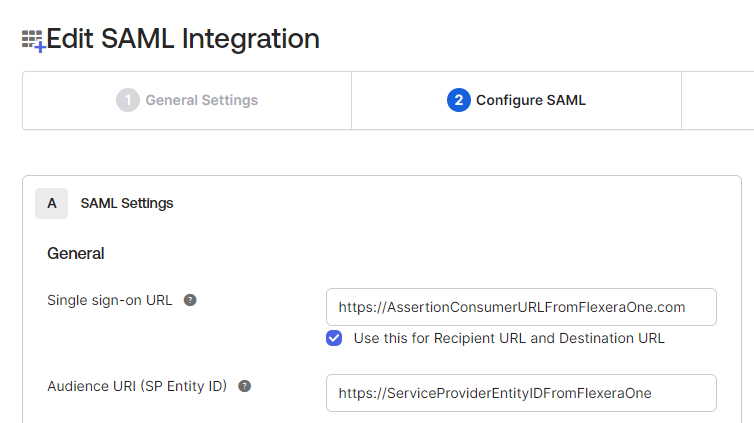
- Copy the Assertion consumer service (ACS) URL and the Service provider entity ID values.
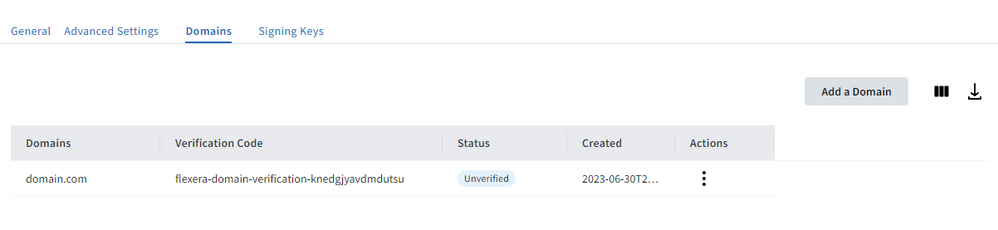
- Navigate to the Domains tab above and enter the domain of the email addresses for your users. This generates a code that you need to add to your domain name system to verify the domain.
- Return to the SAML Application in Okta. Under Configure SAML, update the Single sign-on URL (Assertion consumer service URL) and Audience URI (Service provider entity ID) with the values from Flexera One that you copied earlier.
Learn More
After testing, you can enforce SSO to require your organization’s users to log in through SSO.
More information about JIS Provisioning can be found on the Flexera Documentation page Just-in-Time Provisioning.
To verify your domain, follow the steps provided in Verifying a Domain with a TXT Record.
Jul 25, 2023 01:06 PM