This website uses cookies. By clicking Accept, you consent to the use of cookies. Click Here to learn more about how we use cookies.

Turn on suggestions
Auto-suggest helps you quickly narrow down your search results by suggesting possible matches as you type.
- Flexera Community
- :
- Spider
- :
- Spider Knowledge Base
- :
- Set up Active Directory LDAPS and LDAP Signing
Subscribe
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Subscribe
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
Subscribe
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Description
This article covers setting up "Secure" Active Directory connection, LDAP over SSL (LDAPS) and LDAP signing. The lab was setup with Security Options > Domain controller: LDAP server signing requirements & Network security: LDAP server signing requirements as Require signing. Microsoft is releasing an update (LDAP channel binding and LDAP signing) to increase security with communication between LDAP clients and Active Directory domain controllers.Spider supports LDAPS and LDAP signing polices.
The default port for LDAP is port 389, but LDAPS uses port 636 and establishes SSL/TLS upon connecting with a client.
For initial setup, please refer to the User Manual section 8.5.1 for setting up Active Directory.
The document will be revised for LDAP channel binding.
Resolution
Please follow these steps.
- Set domain policy up for LDAP Server signing requirements.
- Log on Spider as the Administrator into the Default (0) Mandator.
- Open System and then Active Directories.
- Open Default Mandator.
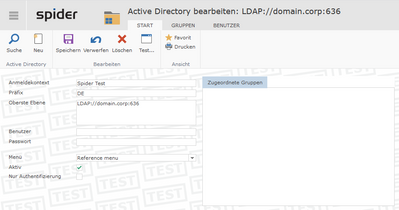
- In the Top Level parameter the standard will be set to your domain settings such as "LDAP://domain.corp" to enable LDAPS, adjust the parameter to "LDAP://domain.corp:636".
- Restart the Spider Core Service.
- The Windows authentication login will log on using LDAPS.
For assistance or questions. Please contact Flexera Support.
Mar 02, 2020 09:47 AM - edited Feb 08, 2021 03:37 AM
Labels:
No ratings