- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review – September 2020
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
In September, Secunia Research at Flexera issued 514 advisories for 389 unique versions of 289 products from 69 different vendors.
Apache Struts and Microsoft Exchange Server had notable vulnerabilities with a high threat score.
Since we can’t patch everything due to the sheer volume of vulnerabilities, prioritize remediation efforts from a risk management perspective. Threat intelligence is a crucial parameter in risk analysis.
Zero-Day and Highly Critical Vulnerabilities
No Zero-day advisory in September.
However, 78 highly critical advisories with 63 had a CVSS score between 9 and 10. Majority of these were for RedHat, SUSE, Microsoft SharePoint, and Exchange.
Apache Struts
Two highly critical vulnerabilities were reported in Apache Struts 2.5.22 and prior versions. CVE-2019-0230 with CVSS oft 9.8 where an error when applying forced OGNL evaluation inside a Struts tag attribute can be exploited to execute arbitrary code via a specially crafted request. CVE-2019-0233 with CVSS 7.5 where an error when handling file uploads can be exploited to cause a DoS condition via a specially crafted request. Both vulnerabilities are linked to malware and used in recent and historic cyber exploits.
In September, advisories are released for other software that uses the Apache Struts framework, namely IBM Sterling File Gateway, IBM Tivoli Netcool/OMNIbus Web GUI, and F5 BIG IP Application Acceleration Manager (AAM). In the coming months, we would probably see other vendors releasing patches or at least acknowledgement of these CVEs in their software.
Microsoft Exchange Server
CVE-2020-16875 has a threat score of 82, but Microsoft states that exploitation is highly unlikely. The patch KB4577352 was released as part of Patch Tuesday on September 8th. However, the advisory was updated on September 17th. It affects Microsoft Exchange Server 2016 and 2019. An error related to Microsoft Exchange software when handling objects in memory can be exploited to corrupt memory and subsequently execute arbitrary code with system privileges via a specially crafted email sent to the Microsoft Exchange server.
Operating Systems
Secunia advisories for different Operating systems are as below:
- Fedora: 18
- Red Hat Enterprise Linux: 64
- Debian: 11
- Amazon Linux: 20
- Ubuntu: 46
- SUSE Linux: 43
- Oracle Linux: 15
- CentOS Advisories: 3
- Microsoft OS Advisories: 4
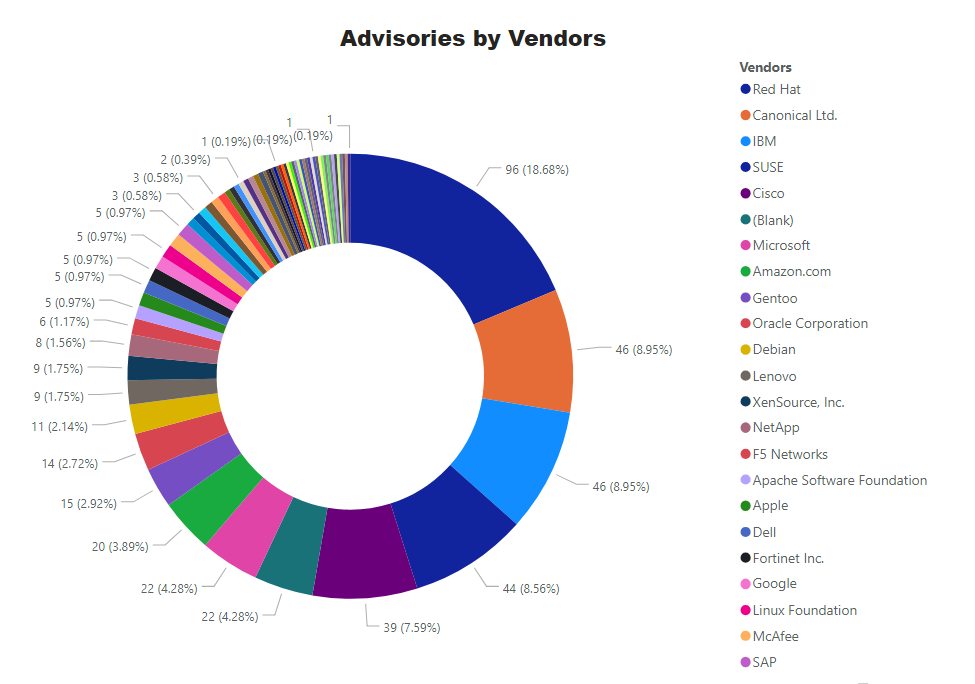
Top Vendors with the most Advisories
Key Points
- Red Hat had the highest number of advisories with 96 in total. However, 64 for RHEL and 18 for Fedora. Rest of the advisories for Ansible line of Products., RedHat JBoss,
- Canonical Ltd. has second-highest advisories with 46 advisories for Ubuntu 12.04, 14.04, 16.04, and 18.04.
- IBM ranks third and most notable vulnerability in its WebSphere software. An advisory SA93203 which was issued in January but CVE-2020-4578 was added, and solution section was updated.
- SUSE at fourth with most vulnerabilities SLES flavour version 11,12, and 15.
- Cisco is kept its position at fifth with most advisories for its IOS 12.x, 15.x, IOS XE 3.x.x, and Jabber among others.
- Open Source software at the sixth level. Most vulnerabilities in Django REST, QEMU, OpenSSL, and WordPress.
- Microsoft is in sixth place with 22 advisories. More details are in the Patch Tuesday section.
Advisories for Browsers
- Microsoft Internet Explorer (version 9 & 11): 1 Advisory.
- Microsoft Edge (HTML Based - Legacy): 1 Advisory
- Microsoft Edge (Chromium Based): 3 Advisories
- Google Chrome: 2 Advisories
- Mozilla Firefox: 2 Advisories
- Mozilla Thunderbird – 1 Advisory
Microsoft Patch Tuesday
On September 8th – Second Tuesday of September, Microsoft issued advisories for these software:
- Microsoft Windows
- Microsoft Edge (Edge HTML-based)
- Microsoft Edge (Chromium-based)
- Microsoft Chakra Core
- Internet Explorer
- SQL Server
- Microsoft JET Database Engine
- Microsoft Office and Microsoft Office Services and Web Apps
- Microsoft Dynamics
- Visual Studio
- Microsoft Exchange Server
- SQL Server
- ASP.NET
- Microsoft OneDrive
- Azure DevOps
A complete list of all applicable updates for August’s Patch Tuesday is here [1]
Patch Tuesday KBs
A digest of Patch Tuesday is listed here [2]
|
KB Article |
Applies To |
|
SharePoint Foundation 2013 |
|
|
SharePoint Enterprise Server 2013 |
|
|
SharePoint Foundation 2010 |
|
|
Windows 10 Version 1809, Windows Server 2019 |
|
|
Windows 10, version 2004 |
|
|
Windows 10, version 1903, Windows Server version 1903, Windows 10, version 1909, Windows Server version 1909 |
|
|
Windows 10, version 1607, Windows Server 2016 |
|
|
Windows Server 2012 (Monthly Rollup) |
|
|
Windows Server 2012 (Security-only update) |
|
|
Windows 7, Windows Server 2008 R2 (Monthly Rollup) |
|
|
Windows 7, Windows Server 2008 R2 (Security-only update) |
|
|
Windows Server 2008 Service Pack 2 (Monthly Rollup) |
|
|
Windows 8.1, Windows Server 2012 R2 (Monthly Rollup) |
|
|
Windows Server 2008 Service Pack 2 (Security-only update) |
|
|
Windows 8.1, Windows Server 2012 R2 (Security-only update) |
|
|
Exchange Server 2019, Exchange Server 2016 |
|
|
SharePoint Server 2019 |
|
|
SharePoint Enterprise Server 2016 |
|
|
SharePoint Foundation 2013 |
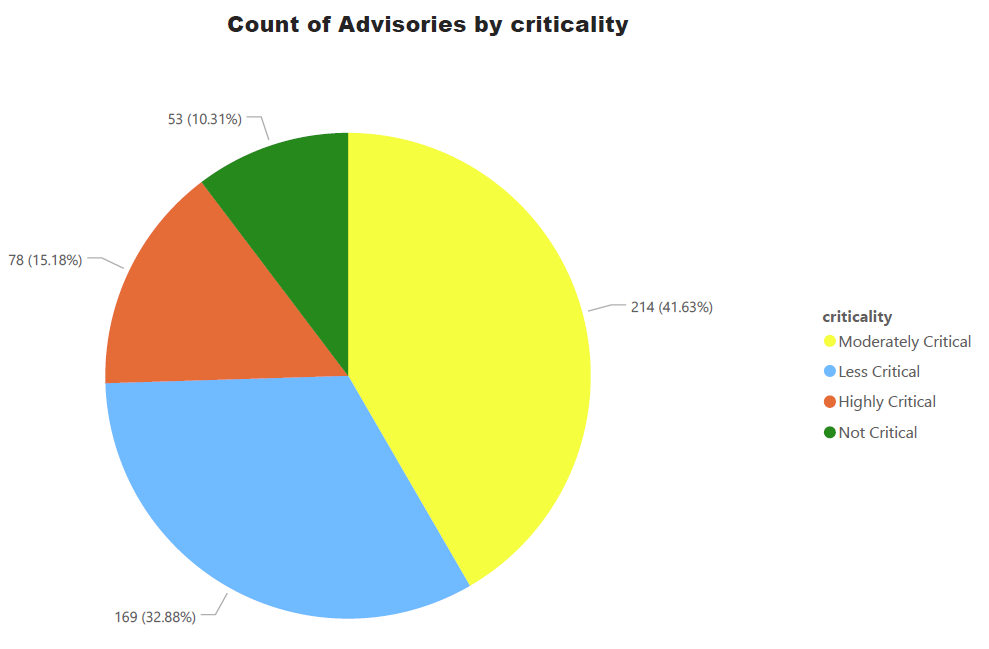
Advisories by Criticality
For easy understanding of Operations teams and management, Secunia Advisories are ranked into 5 simple and easy to understand criticalities. Secunia research follows a meticulous process which involves detailed analysis, peer review, and a QA process – among other things. Our customers can depend on the intelligence without indulging into more minute details of CVSS, impact and attack vector. All of these factors are considered during the ranking process. Further explained at this link.
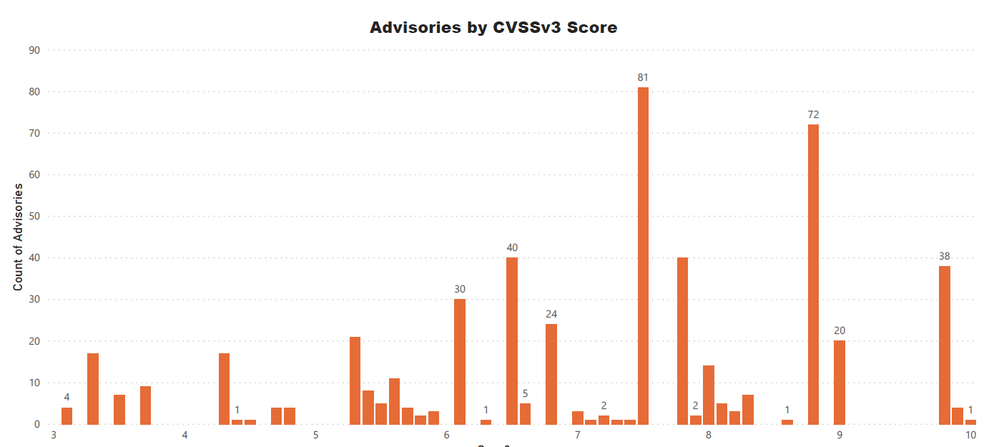
Advisories by Average CVSS Score
A CVSS score is a metric used to measure the severity of a vulnerability. CVSS v3 specifications and the criteria details are at this link.
CVSS ranges from 0 to 10. 0 being the lowest and 10 being the highest score; the advisories spread is as below:
CVSS 3 Score
- Advisories with Low CVSS3 under 4.0: 35 (8.24%)
- Advisories with Mid CVSS3 range 4-7: 134 (31.53%)
- Advisories with High CVSS3 range 7-10: 256 (60.24%)
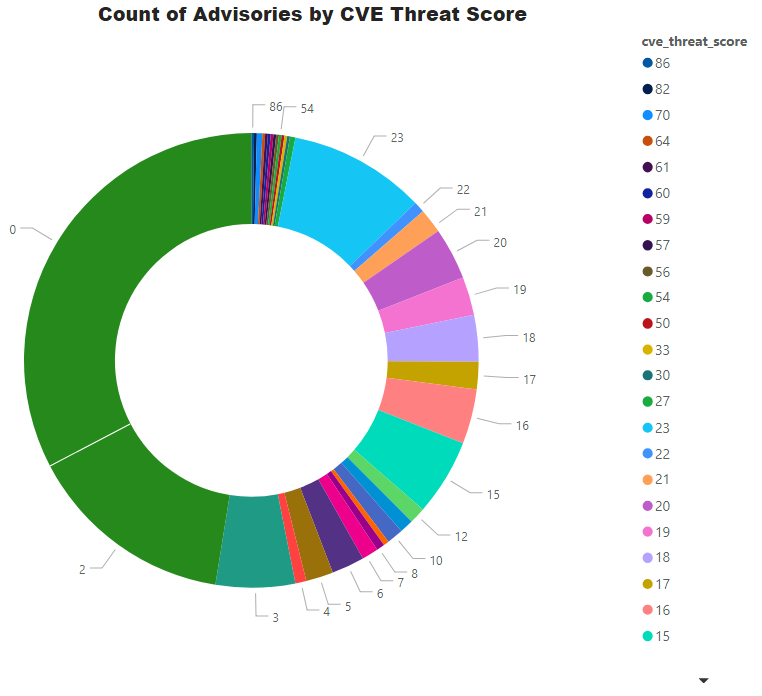
Threat Score
Threat score is calculated based on criticality and its linkage to a recent or historical threat of either remote trojan horse, ransomware, used in penetration testing tools, availability of exploit kit, and cyber exploit. Each rule triggers an increase in the threat value. A detailed explanation of Threat Score calculation is available at this link.
Advisories with positive Threat Score (1+): 346 (67.32%)
- None Threat Score SAIDs (=0): 168 (32.68%)
- Low-Range Threat Score SAIDs (1-12): 159 (30.93%)
- Medium-Range Threat Score SAIDs (13-23): 171 (33.27%)
- High-Range Threat Score SAIDs (24-44): 4 ( 0.78%)
- Critical-Range Threat Score SAIDs (45-70): 10 ( 1.95%)
- Very Critical Threat Score SAIDs (71-99): 2 ( 0.39%)
Ransomware, Malware, and Exploit Kits
- Historically Linked to Ransomware: 10 (1.95%)
- Historically Linked to Malware: 54 (10.51%)
- Linked to a Recent Cyber Exploit: 89 (17.32%)
- Related to a Historical Cyber Exploits: 229 (44.55%)
- Included in Penetration Testing Tools: 199 (38.72%)
Conclusion
Patch Tuesday should be applied as soon possible after its initial release. Most organization focus on client and Server Operating system patches, but we have noticed that a lot of critical patches are released for software like Exchange, Office, and SharePoint.
Once the vulnerabilities in common frameworks are discovered, the software that uses or redistributes the software also issues patches for their versions. However, the process can take time and leaves the software vulnerable to attack as the exploit or POC are usually available for the base vulnerability.
Threat score is an essential parameter in risk analysis, and most organization ignores risk management and choose to patch a predefined set of software – which is a dangerous approach. We will discuss remediation from a risk management perspective in the next episode of the blog.
A complete list of vulnerabilities, affected software, criticality, threat score, and relevant patch information is available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera. Stay Secure!
References:
[2] https://portal.msrc.microsoft.com/en-us/security-guidance/releasenotedetail/2020-Sep
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Monthly Vulnerability Insights: March 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - February 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - January 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - December 2023 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - November 2023 in Software Vulnerability Management Blog