- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review – May 2020
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
Secunia Research issued 448 advisories for 80 unique vendors in 253 products and 336 unique versions, and issued 76 rejected advisories. A 28% decrease in the total number of advisories from the previous month.
The number of updates for browsers is increasing—no Zero-day advisories in May.
Secunia advisories combine vulnerabilities for the same products together for easy consumption and decision making. 76 advisories were rejected so that security teams can focus on the correct priorities.
Browsers
The frequency for Brower advisories and updates is growing each month and usually need multiple update cycles.
Two highly critical advisories were issued for Google Chrome. Similarly, two highly critical advisories for Mozilla Firefox each.
One advisory for Microsoft Internet Explorer 11.x and 9.x, and Mozilla Thunderbird.
Call to Action
Keep your browsers updated due to exposure.
- Update Mozilla Firefox 75.x and 68.x ESR.
- Update Google Chrome to the latest version.
- Install the updates for Internet Explorer 11.x and 9.x that were shipped with Patch Tuesday.
Operating Systems:
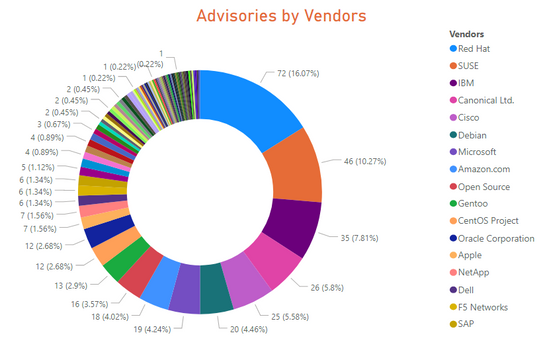
- 21 advisories for Red Hat Enterprise Linux 6,7,8 and 44 advisories for Fedora 30 and 31.
- 26 advisories for Ubuntu 14.04, 16.04 and 18.04
- 45 advisories for SUSE Linux Enterprise Linux Server (SLE) version 11 through 15
- 12 advisories for Oracle Linux 6 and 7.
- 20 advisories for Debian 10.x and GNU/Linux 9.x.
- 12 advisories for CentOS 6.x and 7.x.
- 18 advisories for Amazon Linux AMI and 2.
- 4 advisory for Microsoft Client and Server Operating systems. One for each Microsoft OS pair.
Advisories by Vendors
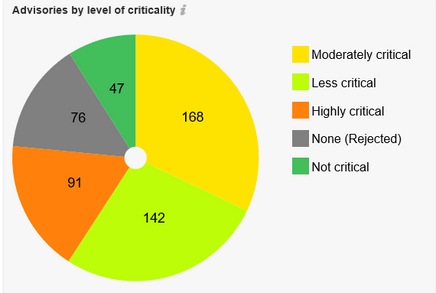
Advisories by Criticality
Secunia Advisory criticalities are further explained at this link.
Count of Advisories versus Attack Vector.
A large proportion of vulnerabilities (68%) can be exploited from remote – usually the case.
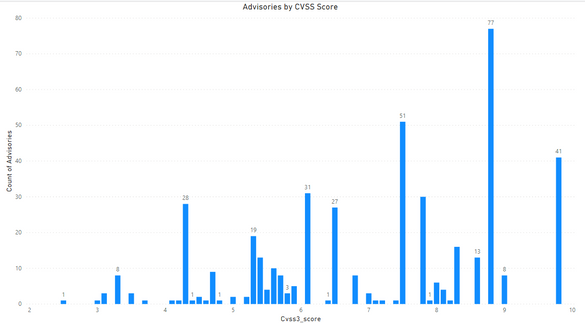
Advisories by CVSS Score
CVSS v3 is the industry standard to define the severity of the vulnerabilities, its exploitability, impact metrics, and environmental metrics.
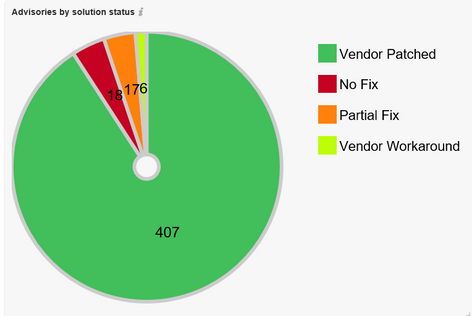
Advisories by Solution Status
Threat Score
The criteria for Threat Score calculation are outlined at this link.
Ransomware, Malware, and Exploit Kits:
5 instances of kinsing , Loncom, and Mandrake with CVE-2020-6819 and CVE-2020-6820 related to Mozilla Firefox, ESR, Thunderbird, and Seamonkey. Similarly, Amazon Linux, Fedora, CentOS has shipped updates for these software.
CVE-2020-1048 can be exploited by Stuxnet malware. Vulnerability results in the elevation of Privileges in Windows Print Spooler services in Microsoft Windows Server 2019, 2016, 2012, 2008, and Windows 7, 8.1, and 10.
- Historically Linked to Ransomware: 7 (1.12%)
- Historically Linked to Malware: 50 (8.03%)
- Linked to a Recent Cyber Exploit: 44 (7.06%)
- Related to a Historical Cyber Exploits: 189 (30.34%)
- Included in Penetration Testing Tools: 186 (29.86%)
Conclusion
The number of advisories decreased from the last month. However, the frequency of operating systems and browser patches is increasing.
A complete list of vulnerabilities affected versions, criticality, threat score, and relevant patch information are available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Monthly Vulnerability Insights: March 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - February 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - January 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - December 2023 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - November 2023 in Software Vulnerability Management Blog