- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review – July 2020
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
In July, Secunia research issued 674 advisories for 83 unique vendors in 361 products and 475 unique versions, while issued 97 rejection notice advisories. An increase of 34.5% advisories from the previous month.
A Zero-day vulnerability was reported in Cisco ASA firewall and FDA products.
Oracle overtook RedHat as a top vendor with most vulnerabilities.
The amount of browsers vulnerabilities and their relevant patches are Achilles’ heel of effective patch management.
Zero-Day
A vulnerability is reported in the web service system that allows remote access to Cisco ASA (Adaptive Security Appliance) – a network firewall and Cisco’s Firepower Threat Defence. An attacker can send a specially crafted HTTP request that can traverse the servers’ file system and also establish an SSL VPN or AnyConnect VPN session to the devices by impersonating another user. A lack of proper input validation causes it. There are reports of a publicly available exploit being used in targeted attacks.
Cisco ASA 9.6 till 9.14 are affected. Secunia Research has issued SA96432, which has further details.
Call to Action
- Cisco ASA running lower than 9.6 version should migrate to the latest supported software 9.6.4.42 or above.
- Versions from 9.6 till 9.14 needs to update to latest versions as described here.
- Cisco FDA 6.2.2 till 6.6.0 are affected and should be updated to the latest fixed released versions as mentioned on the above link.
Operating Systems:
- SUSE Linux = 58
- Amazon Linux = 49
- Ubuntu = 37
- Fedora = 35
- Oracle Linux = 34
- Red Hat Enterprise Linux = 28
- CentOS Advisories = 7
- Microsoft OS Advisories = 7
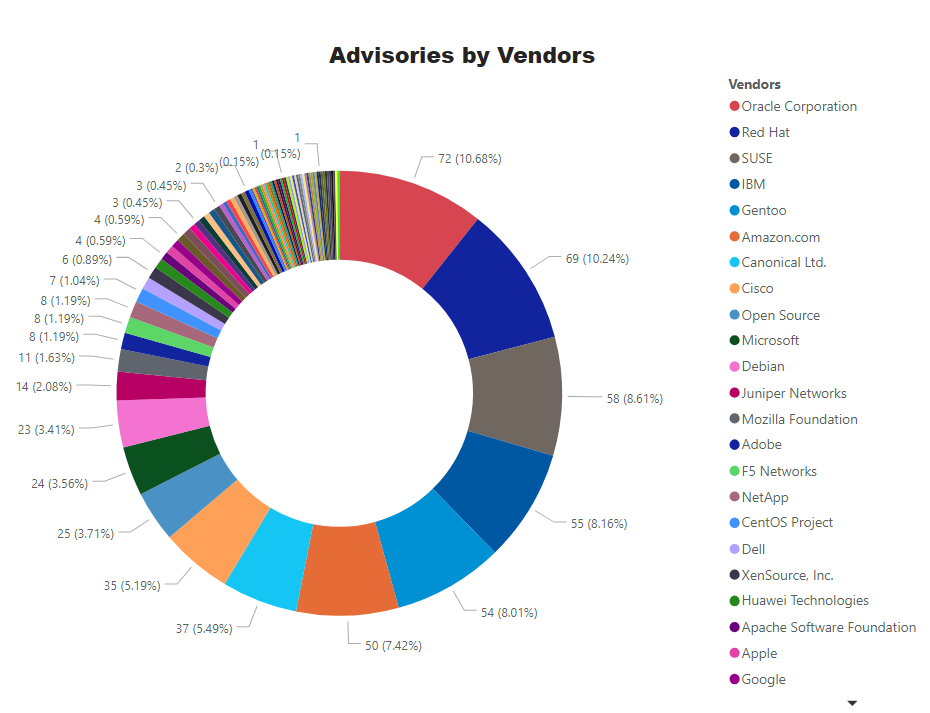
Top Vendors with the most Advisories
Key Points
- Oracle has taken over Red Hat as a top vendor with staggering 72 advisories.
- Microsoft moved down to the 10th place with 24 advisories. 7 for its primary OSes. A highly critical advisory – SA96100 affecting Windows 10 and Server 2019. Out of band patches were issued for Microsoft Edge Chromium.
- Linux/Unix based Operating systems are among the top software with most vulnerabilities – as usual.
Advisories for Browers
- Microsoft Internet Explorer 9 & 11: 1 Advisory - Apply Microsoft Update as listed on the official site
- Microsoft Edge (HTML Based - Legacy): 1 Advisory - Update to the latest version as mentioned in the above link
- Microsoft Edge (Chromium Based): 2 Advisories – Upgrade to 84.0.522.49
- Google Chrome: 2 Advisories – Upgrade to 84.0.4147.125
- Mozilla Firefox: 6 Advisories – Update to version 68.11
- Mozilla Thunderbird – 3 Advisories – Update to 68.11.
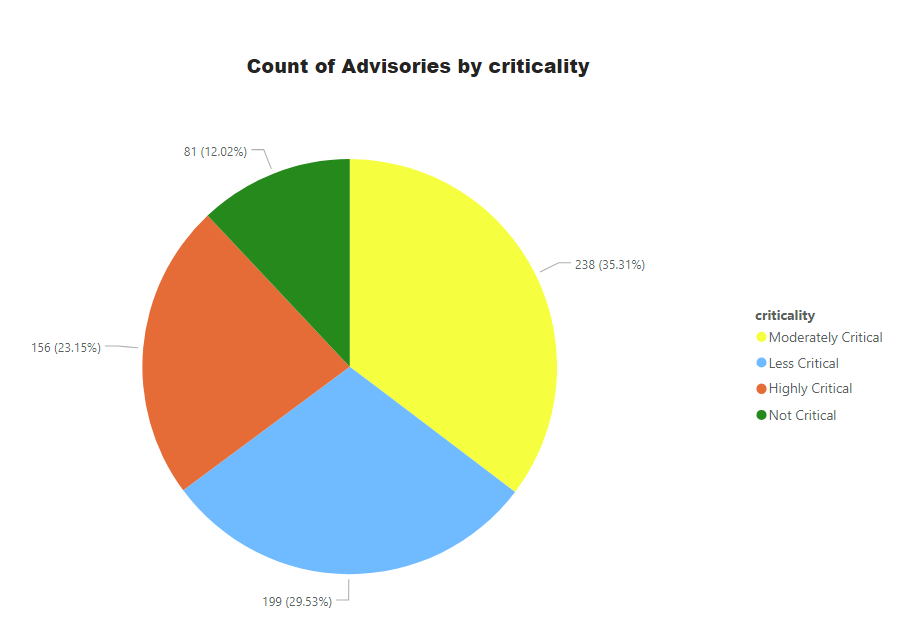
Advisories by Criticality
Secunia Advisory criticalities are further explained at this link.
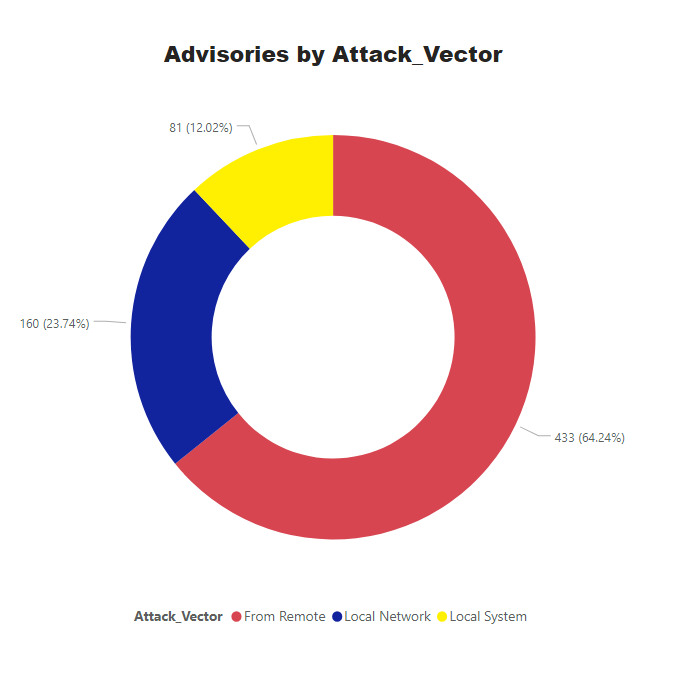
Advisories by Attack Vector.
65% of vulnerabilities can be exploited from remote, which makes the remediation efforts even more critical.
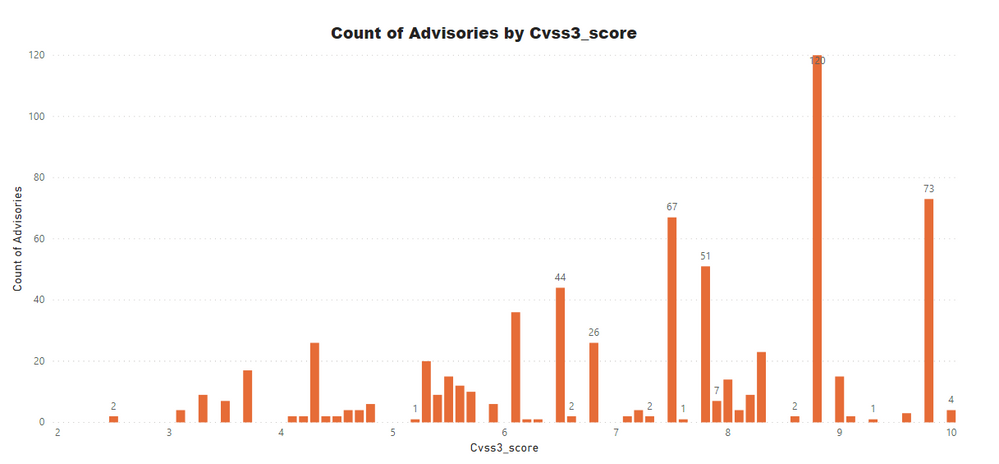
Advisories by Average CVSS Score
A CVSS score is a metric that is used to measure the severity of a vulnerability. CVSS3 specifications and the criteria details can be found at this link.
CVSS ranges from 0 to 10. 0 being the lowest and 10 being the highest score; the advisories spread is as below:
CVSS 3 Score
- Advisories with Low CVSS3 under 4.0: 39 (5.79%)
- Advisories with Mid CVSS3 range 4-7: 231 (34.27%)
- Advisories with High CVSS3 range 7-10: 404 (59.94%)
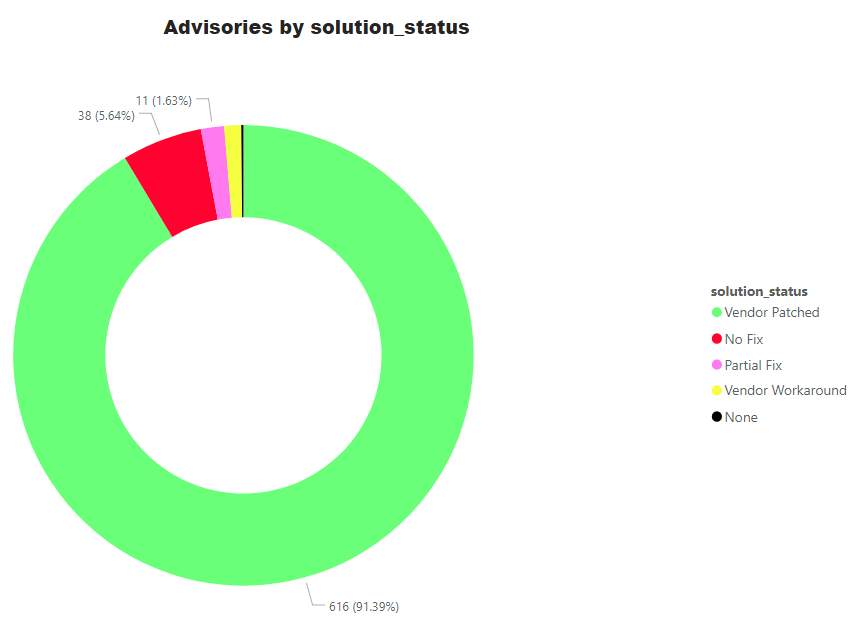
Advisories by Solution
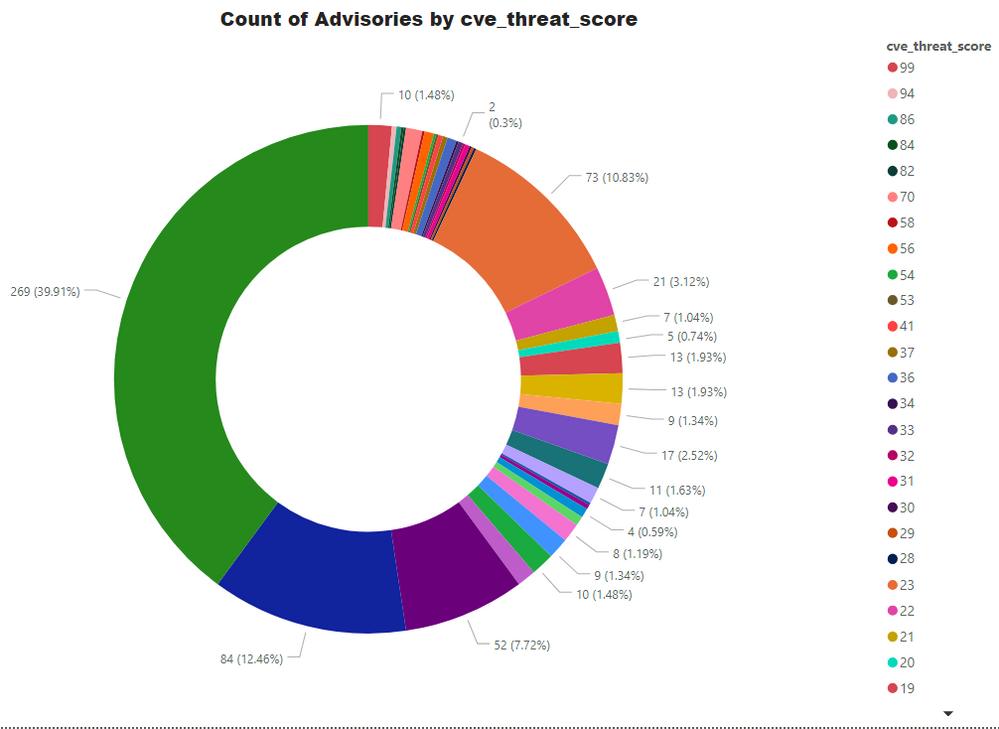
Threat Score
An add-on by Software Vulnerability Research and Software Vulnerability Manager is Threat Intelligence. We give a score from 0 to 100 depending upon its severity, exploit availability, inclusion in penetration testing tools and the likelihood of being exploited. A detailed explanation of Threat Score calculation is available at this link.
- Advisories with positive Threat Score (1+): 405 (60.09%)
- None Threat Score SAIDs (=0): 269 (39.91%)
- Low-Range Threat Score SAIDs (1-12): 189 (28.04%)
- Medium-Range Threat Score SAIDs (13-23): 169 (25.07%)
- High-Range Threat Score SAIDs (24-44): 17 (2.52%)
- Critical-Range Threat Score SAIDs (45-70): 14 (2.08%)
- Very Critical Threat Score SAIDs (71-99): 16 (2.37%)
Ransomware, Malware, and Exploit Kits:
- Historically Linked to Ransomware: 10 (1.48%)
- Historically Linked to Malware: 79 (11.72%)
- Linked to a Recent Cyber Exploit: 86 (12.76%)
- Related to a Historical Cyber Exploits: 255 (37.83%)
- Included in Penetration Testing Tools: 275 (40.80%)
Conclusion
The amount of reported vulnerabilities is on the rise. Linux/Unix based OS are most vulnerable. Browers patches are released from 3 to 6 times a month which makes patching effort quite tricky especially for Google Chrome and Mozilla Firefox. Zero days must be prioritized as a likelihood of an attack is very high.
A complete list of vulnerabilities affected versions, criticality, threat score, and relevant patch information are available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Monthly Vulnerability Insights: March 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - February 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - January 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - December 2023 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - November 2023 in Software Vulnerability Management Blog