- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Management Blog
- :
- Monthly Vulnerability Review – August 2020
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
In August, 425 advisories were issued for 354 unique versions of 258 products from 70 different vendors.
Two Zero-day vulnerabilities were reported by Microsoft, including one which was known to it for more than one and half year.
Microsoft’s August Patch Tuesday and vulnerabilities in other third party vendors and products are part of this months’ blog.
Zero-Day
Two Zero-day advisories were reported in Microsoft Windows and Internet Explorer 9 and 11.
CVE-2020-1464 is dubbed as “Windows Spoofing” vulnerability. Microsoft Windows uses code signing certificates to authenticate a software’s integrity and verify its publisher. A flaw in the system keeps a signature valid even after appending any content to the end of a Windows installer (.msi). It is dangerous in particular with .jar files which can be used for malicious purpose. Java loads its required resources in a single request. If the attacker successfully appends a malicious JAR file to a signed MSI installer; Microsoft Windows wouldn’t complain and validates the software. Just double-clicking on the file can result in successful exploitation. [1]
The security researchers informed Microsoft approximately one an half year ago, but it decided not to patch the vulnerability at the time. The fix was shipped in August’s Patch Tuesday.
CVE-2020-1380 was also fixed in August Patch Tuesday. The vulnerability is detected in Internet Explorer 9 and 11. It uses the ‘use after free’ bug in IE’s JavaScript ‘Just-in-time engine. Reportedly, the vulnerability can be exploited by merely visiting a specially crafted website. Refer to SA97055 for more details.
Call to Action
- Deploy patches offered in Microsoft August’s Patch Tuesday release.
Operating Systems:
Secunia advisories for different Operating systems are as below:
- Fedora: 28
- Red Hat Enterprise Linux: 11
- Debian: 16
- Amazon Linux: 10
- Ubuntu: 29
- SUSE Linux: 47
- Oracle Linux: 15
- CentOS Advisories: 6
- Microsoft OS Advisories (Including one Zero-day): 4
Top Vendors with the most Advisories
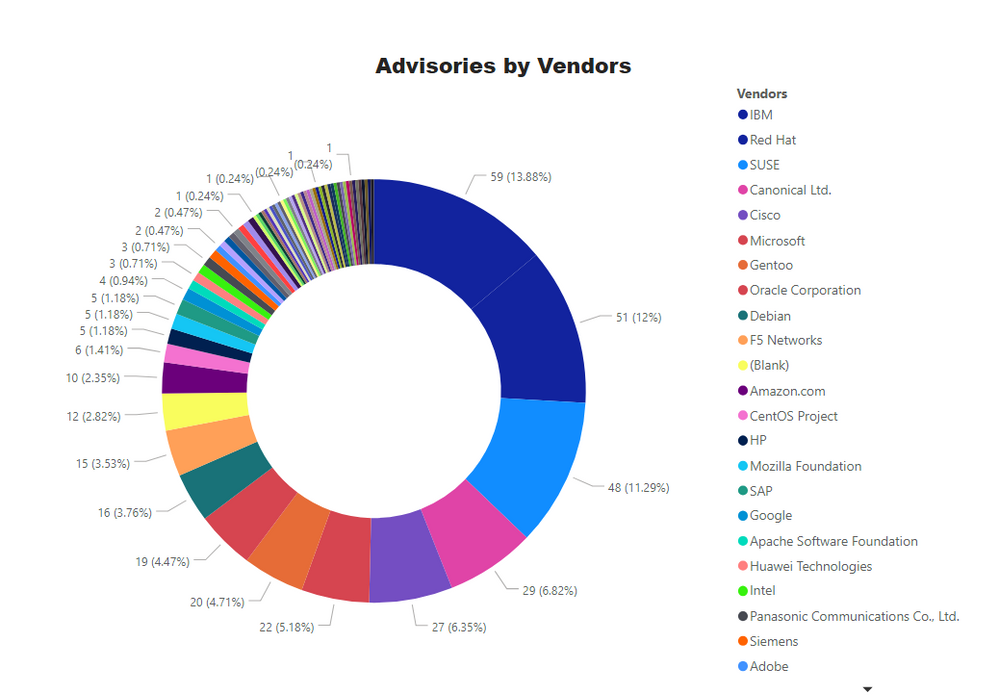
Key Points
- IBM has topped with the 59 advisories in its various products like WebSphere, Tivoli, and other financial software.
- Red Hat has second-highest advisories because we treat RHEL and Fedora under the same vendor.
- 48 Advisories for SUSE with 47 for SLES 11. 12, and 15 versions.
- Canonical Ltd. ranked fourth with advisories for Ubuntu 12.04, 14.04, 16.04, and 18.04.
- Cisco is fifth with most advisories for its 9000 and 300 series switches, 6000 series routers and one for widely used WebEx.
- Microsoft is in sixth place with 22 advisories. More details are in the Patch Tuesday section.
Advisories for Browsers
- Microsoft Internet Explorer (version 9 & 11): 2 Advisories.
- Microsoft Edge (HTML Based - Legacy): 1 Advisory
- Microsoft Edge (Chromium Based): 3 Advisories
- Google Chrome: 3 Advisories
- Mozilla Firefox: 3 Advisories
- Mozilla Thunderbird – 2 Advisories
Microsoft Patch Tuesday
Microsoft issues security patches for its products on every second Tuesday of the month known as Patch Tuesday. On 11th August – Second Tuesday of August, Microsoft issued advisories for these software:
- Microsoft Windows
- Microsoft Edge (EdgeHTML-based)
- Microsoft Edge (Chromium-based)
- Microsoft ChakraCore
- Internet Explorer
- Microsoft Scripting Engine
- SQL Server
- Microsoft JET Database Engine
- .NET Framework
- ASP.NET Core
- Microsoft Office and Microsoft Office Services and Web Apps
- Microsoft Windows Codecs Library
- Microsoft Dynamics
A complete list of all applicable updates for August’s Patch Tuesday is here
Patch Tuesday KBs
4 Secunia Advisories cover updates for each OS pair.
|
KB Article |
Applies To |
|
Windows 10 Version 1809, Windows Server 2019 |
|
|
Windows 10, version 2004 |
|
|
Windows 10, version 1607, Windows Server 2016 |
|
|
Windows Server 2012 (Security-only update) |
|
|
Windows 8.1, Windows Server 2012 R2 (Monthly Rollup) |
|
|
Windows 7, Windows Server 2008 R2 (Security-only update) |
|
|
Windows 8.1, Windows Server 2012 R2 (Security-only update) |
|
|
Windows 7, Windows Server 2008 R2 (Monthly Rollup) |
|
|
Windows Server 2008 Service Pack 2 (Monthly Rollup) |
|
|
Windows Server 2012 (Monthly Rollup) |
|
|
Windows Server 2008 Service Pack 2 (Security-only update) |
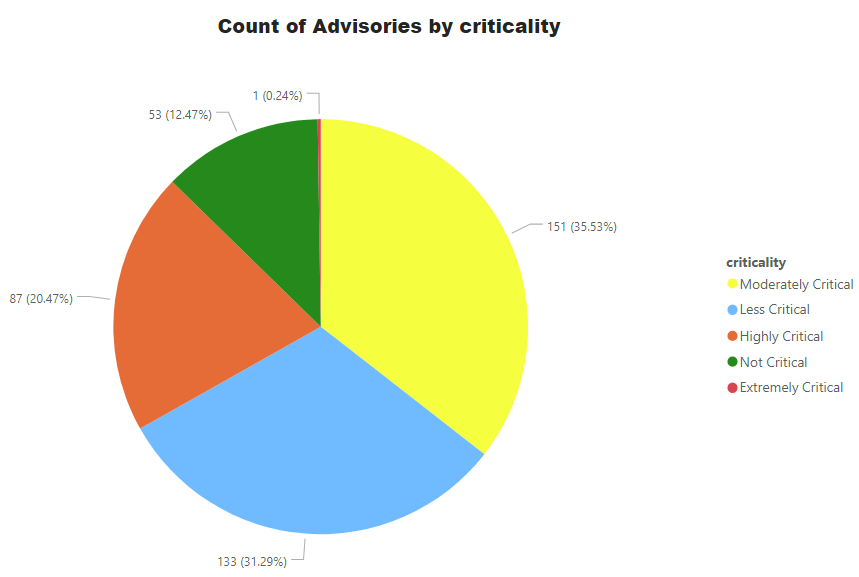
Advisories by Criticality
For easy understanding of Operations teams and management, Secunia Advisories are ranked into 5 simple and easy to understand criticalities. Secunia research follows a meticulous process which involves detailed analysis, peer review, and a QA process – among other things. Our customers can depend on the intelligence without indulging into more minute details of CVSS, impact and attack vector. All of these factors are considered during the ranking process. Further explained at this link.
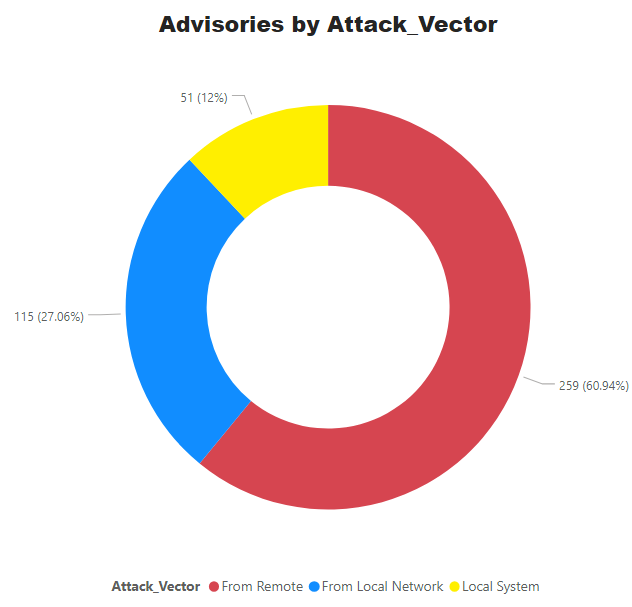
Advisories by Attack Vector.
65% of vulnerabilities can be exploited from remote, which makes the remediation efforts even more critical.
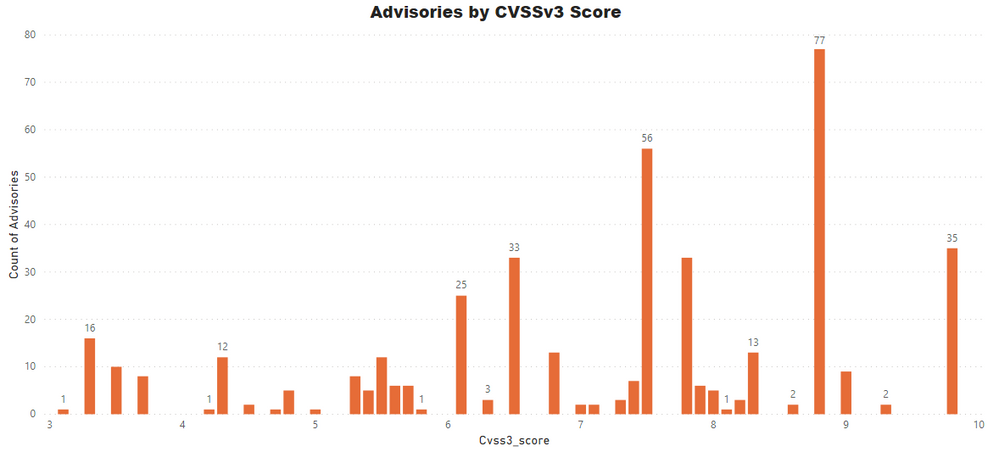
Advisories by Average CVSS Score
A CVSS score is a metric used to measure the severity of a vulnerability. CVSS v3 specifications and the criteria details are at this link.
CVSS ranges from 0 to 10. 0 being the lowest and 10 being the highest score; the advisories spread is as below:
CVSS 3 Score
- Advisories with Low CVSS3 under 4.0: 35 (8.24%)
- Advisories with Mid CVSS3 range 4-7: 134 (31.53%)
- Advisories with High CVSS3 range 7-10: 256 (60.24%)
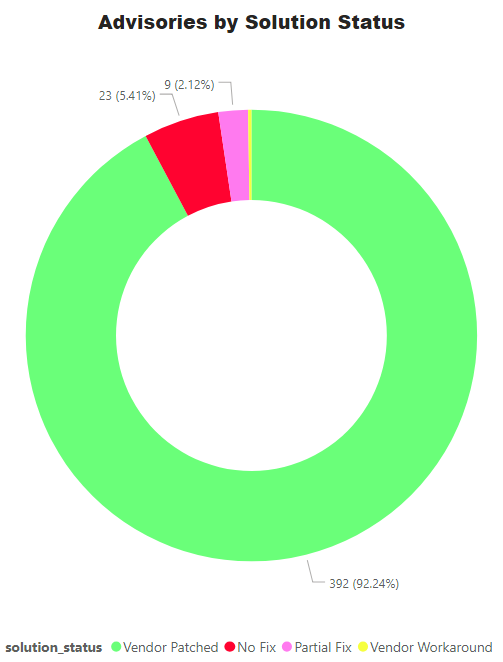
Advisories by Solution
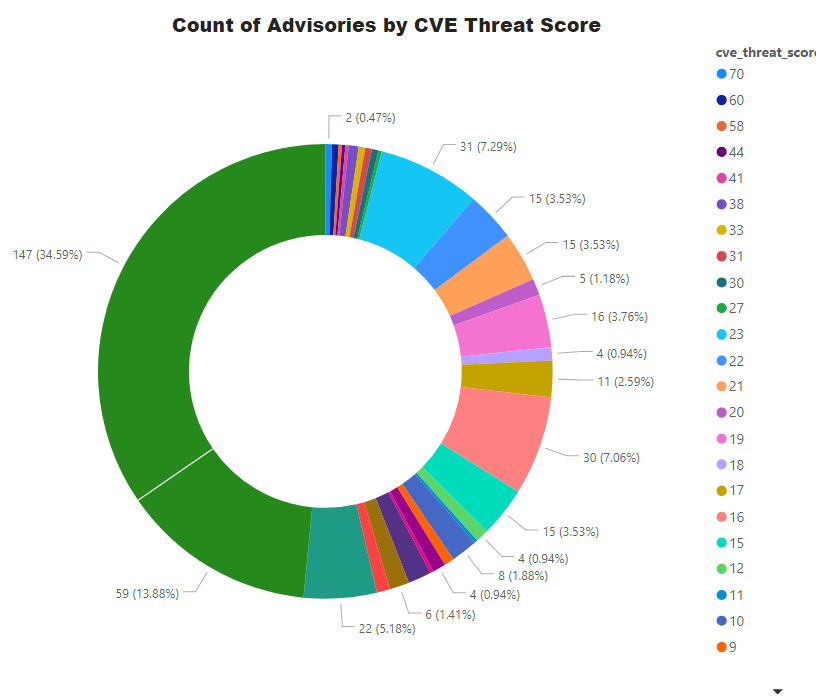
Threat Score
Like many other things in life, not every vulnerability is created equal. For the ease of our customers, we provide threat score as an add-on which helps in decision making and prioritization. Higher the score; bigger the risk!
Threat score is calculated based on criticality and its linkage to a recent or historical threat of either remote trojan horse, ransomware, used in penetration testing tools, availability of exploit kit, and cyber exploit. Each rule triggers an increase in the threat value. A detailed explanation of Threat Score calculation is available at this link.
- Advisories with positive Threat Score (1+): 278 (65.41%)
- None Threat Score SAIDs (=0): 147 (34.59%)
- Low-Range Threat Score SAIDs (1-12): 119 (28.00%)
- Medium-Range Threat Score SAIDs (13-23): 142 (33.41%)
- High-Range Threat Score SAIDs (24-44): 12 (2.82%)
- Critical-Range Threat Score SAIDs (45-70): 5 (1.18%)
- Very Critical Threat Score SAIDs (71-99): 0 (0.00%)
Ransomware, Malware, and Exploit Kits:
Statistics clearly shows us that software vulnerabilities have a clear relationship with malware, cyber exploits and notorious ransomware. Remediating these vulnerabilities reduces exposure to these threats. Security is a multi-prong approach where one size fits all or one tool to rule them all is not enough. Just like with network, we require multiple layers of protection; similarly, we need to remediate known vulnerabilities along with a reputable anti-malware system.
- Historically Linked to Ransomware: 05 (1.18%)
- Historically Linked to Malware: 63 (14.82%)
- Linked to a Recent Cyber Exploit: 70 (16.47%)
- Related to a Historical Cyber Exploits: 193 (36.24%)
- Included in Penetration Testing Tools: 275 (40.80%)
Conclusion
More than 60% of vulnerabilities can be exploited from remote while massively 92% advisories have a vendor patch while only 5% have either no fix or an upgrade option is available.
Most malware relies on vulnerabilities in everyday use software. Patching effort minimizes the risk and exposure. For Microsoft Windows environment, always deploy the Patch Tuesday and any out of band security updates. Don’t ignore third-party software as more than 86% of vulnerabilities are found in software other than Microsoft.
A complete list of vulnerabilities, affected software, criticality, threat score, and relevant patch information is available in the Software Vulnerability Research and Software Vulnerability Manager solutions from Flexera.
References:
[1] https://blog.virustotal.com/2019/01/distribution-of-malicious-jar-appended.html
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.
- Monthly Vulnerability Insights: March 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - February 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - January 2024 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - December 2023 in Software Vulnerability Management Blog
- Monthly Software Vulnerability Insights - November 2023 in Software Vulnerability Management Blog