
- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Manager Knowledge Base
- :
- Swap SVM On-Prem SSL certificates [Centos VA] or [RHEL]
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Subscribe to RSS Feed
- Permalink
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
The SVM VA server will generate a self-signed SSL certificate when you choose to use SSL.
These instructions will explain how to swap it for your certificate and key pair.
Synopsis
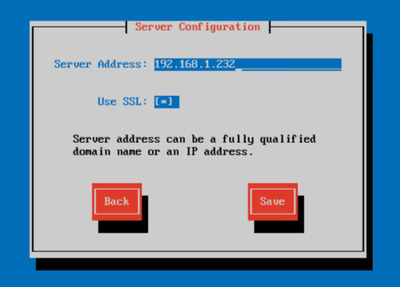
Once you've run through the SVM Virtual Appliance (VA) setup wizard and have selected to use SSL you'll find that the server is set up with a self-signed SSL certificate. In some environments that isn't an ideal solution as the act of propagating the public key from this certificate to all endpoints can be daunting. Below you'll find step by step instructions on how to replace the generated certificate with your own.
1. Obtain and transfer your public and private keys to your SVM VA. Once you have access to the file(s) this can be easily transferred to your server with a tool like WinSCP.
2. If your certificate is packaged together in a PFX file, you can do the following to prepare your public and private key files.
Extract the private key:
openssl pkcs12 -in cert_name.pfx -nocerts -out csi.key
Remove the password from your key, so httpd will start without prompting:
mv csi.key csi.key.secure
openssl rsa -in csi.key.secure -out csi.key
Generate the public certificate:
openssl pkcs12 -in cert_name.pfx -clcerts -nokeys -out csi.crt
If you have a PEM file that has the two keys instead of a pfx you'll want to change the pkcs12 to x509 to match the format of the certificate. If you have another certificate format you'll need to adjust accordingly. Please refer to the openssl manual page for further details
We can find the location for the existing key pair in the virtual host definition for Apache which is found in /etc/httpd/conf.d/secunia-ssl.conf. Here is what the certificates paths look like in virtual host file
SSLCertificateFile /etc/pki/tls/certs/csi.crt
SSLCertificateKeyFile /etc/pki/tls/private/csi.key
The important lines from the virtual host are the SSLCertificateFile and SSLCertificateKeyFile directives. These tell Apache which public and private key to use for the SSL connection and this lets us know what files we need to replace.
4. Remove the existing certificate key pair and replace it with yours.
Begin with deleting the old public key:
rm /etc/pki/tls/certs/csi.crt
Delete the old private key:
rm /etc/pki/tls/private/csi.key
Copy new public key
cp csi.crt /etc/pki/tls/certs/
Copy new private key
cp csi.key /etc/pki/tls/private/
service httpd restartAfter restarting Apache you are all set.
Your connections to the SVM Server will occur using the newly implemented certificate.
Nov 15, 2019 07:31 AM - edited Dec 16, 2019 03:48 AM
