An error occurred with the SVM's SC2012 plugin
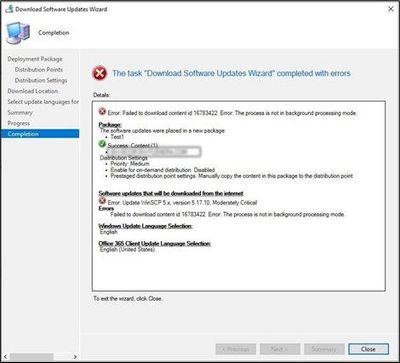
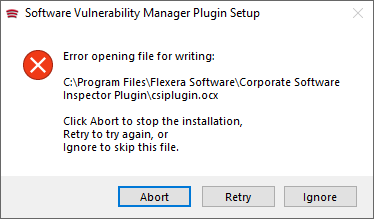
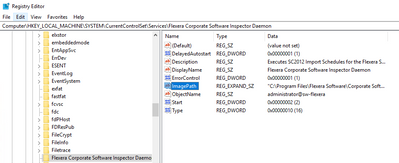
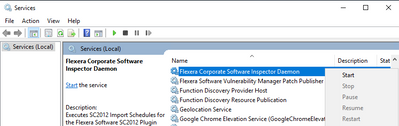
Summary You might get the following error while running/connecting to the SVM Plugin for the SCCM Console. Cause The above error occurs when either the website URL is not added to Trusted Sites and / or the following components are missing from the...