
- Flexera Community
- :
- Software Vulnerability Management
- :
- Software Vulnerability Manager Knowledge Base
- :
- Delete obsolete patch packages created in WSUS by Software Vulnerability Manager
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Summary
The article describes the steps necessary to clean up and remove old third-party packages created by the Software Vulnerability Manager 2018 (SVM) from your local Windows Server Update Services (WSUS) server. While this reference is helpful is designed to help you with your SVM installation, you should redirect any questions about WSUS to Microsoft forums.
Synopsis
With the use of the SVM over time, the number of packages created in WSUS begins to stack up and take up valuable disc space on the server that is facilitating the WSUS role.
Simply declining and deleting package in SVM does not remove the packages from the \UpdateServicePackages folder where SVM packages reside. This article describes how to reclaim disk space used by these packages.
Discussion
Method 1
Clean up any old or irrelevant packages from the SVM web Interface under the Patching > Available menu
- Go through the created packages and determine which packages are no longer relevant. For example, every package older than the latest "Patched Version" is now vulnerable and should be considered for removal.
- Decline and then Delete the old or irrelevant package entries you see listed the Available menu.
If you are using System Center Updates Publisher (SCUP), it may be necessary to run the cleanup wizard for SCUP:
To clean up your WSUS database from old package metadata information:
- Open the WSUS console from Server Manager and navigate to the Options area.
- Select the Server Cleanup Wizard.
- Run the Server Cleanup Wizard.
Run WsusUtil with the parameter listunreferencedpackagefolders and delete packages that it lists.
- Open a CMD shell window as an Administrator
- Execute:
cd "C:\Program Files\Update Services\Tools" WsusUtil.exe listunreferencedpackagefolders > c:\temp\deletefolders.txt - Open C:\temp\deletefolders.txt and see the declined and deleted from SVM packages.
- Remove the beginning lines of the file that read:
The following folders are not referenced by any of the updates in your WSUS server. - In front of each remaining line add: rmdir /q /s
For example: rmdir /q /s C:\Sources\WSUS\UpdateServicesPackages\598ecbc7-2208-401b-9f0c-8eb57488aee - Save the file with the name deletefolders.cmd.
- Double-click on the deletefolders.cmd file to run it to delete unreferenced packages from the filesystem.
Method 2
The following PowerShell commands can be used delete all the third-party packages from your WSUS server:
[Reflection.Assembly]::LoadWithPartialName("Microsoft.UpdateServices.Administration")
$wsus = [Microsoft.UpdateServices.Administration.AdminProxy]::GetUpdateServer();
$wsus.GetUpdates() |
Where { $_.UpdateSource -ne "MicrosoftUpdate" } |
ForEach-Object {
$wsus.DeleteUpdate($_.Id.UpdateId.ToString())
Write-Host $_.Title removed
}
These commands should be executed on your WSUS server with administrator rights.
Workaround
The packages you've so far deleted were patches that you removed from your SVM interface, patches not being used by WSUS and patches that are tagged with Declined status.
Sometimes this will not be enough though.
- In the event, you installed new WSUS on top of your old one and you configured new certificates for your new installation, you may end up 'leaving behind' updates that are still active.
- Since Update Packages are signed with certificates, patches published previously having been signed with older (currently unused certificate):
- These may not be visible in SVM
- These same patches will not be seen in the WSUS Server Console either.
- These packages are physically present at \UpdateServicesPackages and they may remain Approved.
- They may as well be distributed by WSUS to Clients (or synced with Downstream servers) as long as the Clients are suitable for these updates and request it.
- These patches were signed with a certificate that is no longer used.
- Therefore, you can't reuse the patches. You can't Decline them either. You can't even see them in SVM. They became unusable (and soon there will be new versions anyway.
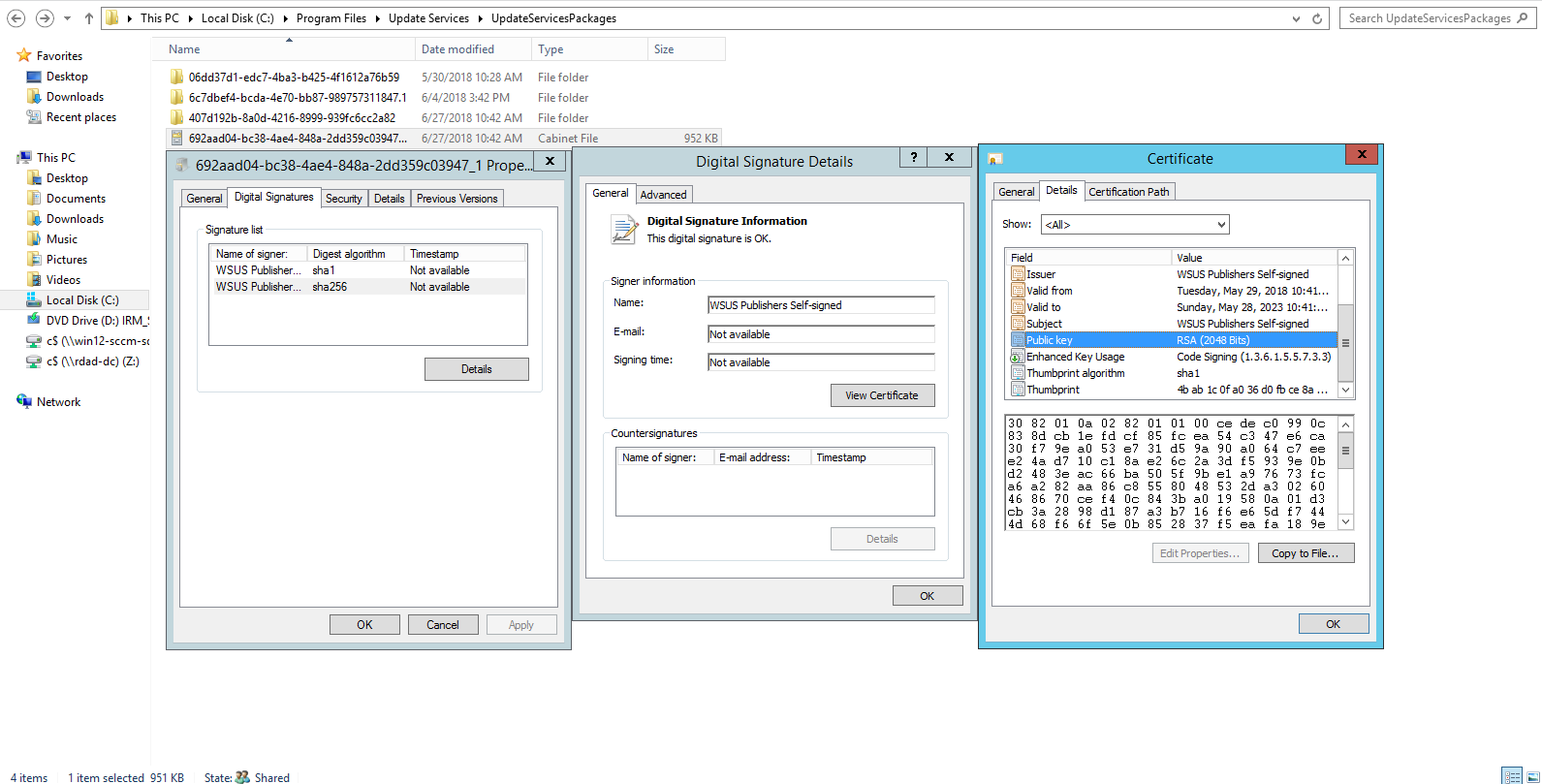
- You must force the deletion of all patches by physically going to C:\Program Files\Update Services\UpdateServicesPackages\ and deleting those.
- If you have a doubt which patches (sitting in folders with long numerical ID names) are to be deleted, then:
- Enter one of the GUID folders
- Find the.CAB file that has the same name as the GUID
- Right-click and select properties
- Open 'Digital Signatures' TAB
- Double-click on the certificate in the middle window
- Select 'View Certificate' in the new window
- Select 'Details' in the new (third) window and find the Serial Key field.
- The 'serial key' is unique and it will show you if the certificate that code-signed this package is the one you are using in your domain actively.
- You can open MMC > File > Add or Remove Snap-In > Certificates > Local Computer on the WSUS.
- Enter the 'WSUS' folder and check the certificate's serial key there. This is the certificate you currently use.
- Do not delete any patches signed with your current certificate - delete patches signed with a certificate that is not in the WSUS Certificate store.
- If you have a doubt which patches (sitting in folders with long numerical ID names) are to be deleted, then:
- You must force the deletion of all patches by physically going to C:\Program Files\Update Services\UpdateServicesPackages\ and deleting those.
- Therefore, you can't reuse the patches. You can't Decline them either. You can't even see them in SVM. They became unusable (and soon there will be new versions anyway.
- Since Update Packages are signed with certificates, patches published previously having been signed with older (currently unused certificate):
on
Jan 28, 2019
07:10 PM
- edited on
Jul 26, 2021
12:45 AM
by
![]() ChrisG
ChrisG
![]()
