- Flexera Community
- :
- Flexera One
- :
- Flexera One Blog
- :
- Better IT visibility for better threat defense
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
It’s no secret that information technology is in rapid flux. Digital transformation and the demands of a post-COVID world are causing software asset management (SAM) and configuration management databases (CMBD) to evolve toward a hybrid view of what IT truly encompasses.
IT asset management (ITAM) and SAM teams continue to manage the complex on-premises processes of lifecycle and vulnerability management, and their purview must expand to include SaaS and cloud inventory data. And don’t forget about application rationalization for sprawling assets, maintaining security from vulnerabilities and aligning to business service units in order to understand IT’s impact on the organization.
Needless to say, you’re juggling a lot—but you don’t have to figure it all out alone. The Flexera 2021 State of IT Visibility Report sheds light on what’s happening with information technology and the data that supports the wide array of business initiatives around the world. This inaugural report illuminates how you can do more with the data you already have to facilitate solutions that drive business results.
ITFM, cloud often get left out
The Flexera State of IT Visibility Report gathers the thinking of more than 300 global technology decision-makers about IT infrastructure, asset management, vulnerability posture and industry trends. It combines this detailed respondent information with the industry expertise and data of Flexera’s Secunia Research and Technopedia teams to highlight pain points and areas of opportunity for IT visibility and vulnerability mitigation.
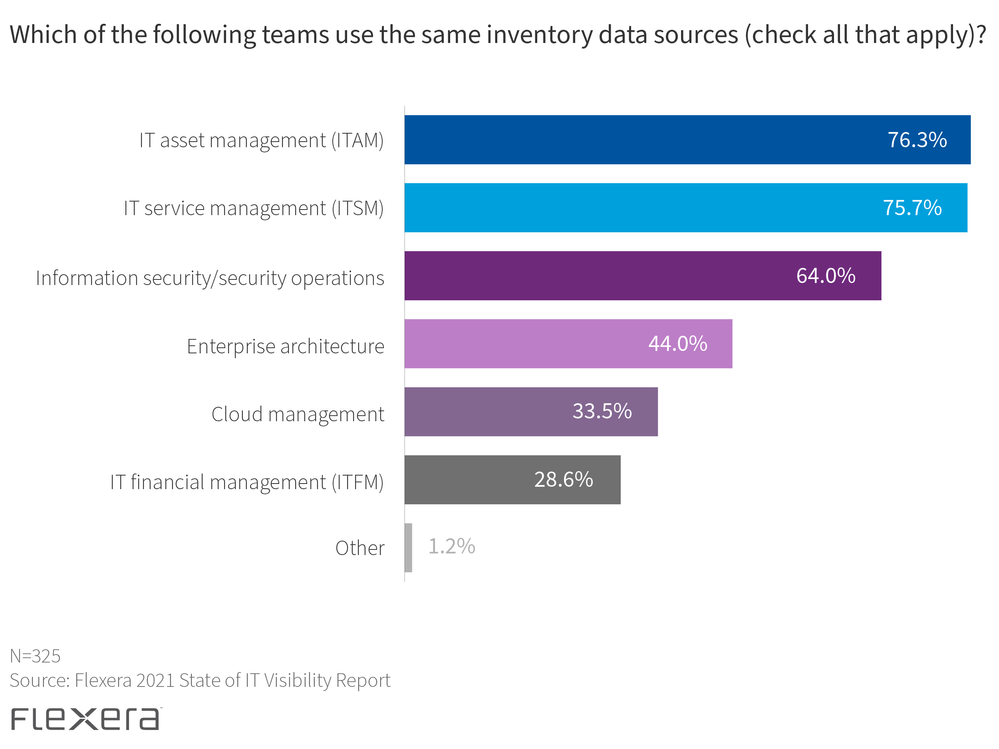
Nearly 80 percent of respondents reported moderate to over-communication between ITAM and security operations (SecOps) teams when it came to vulnerability and risk mitigation practices. Over 75 percent said they share data sources between ITAM and IT service management (ITSM).
That’s great for ITAM, SecOps and ITSM, but it’s important to expand that foundational data to other teams across the organization. The report showed that IT financial management (ITFM), enterprise architecture (EA) and cloud management teams weren’t receiving the same level of communication or data sharing. Contrary to popular belief, cloud should be integrated with traditional ITAM processes, as insight into the on-premises estate is especially helpful for your cloud migration and resource management efforts.
A looming threat landscape requires collaboration
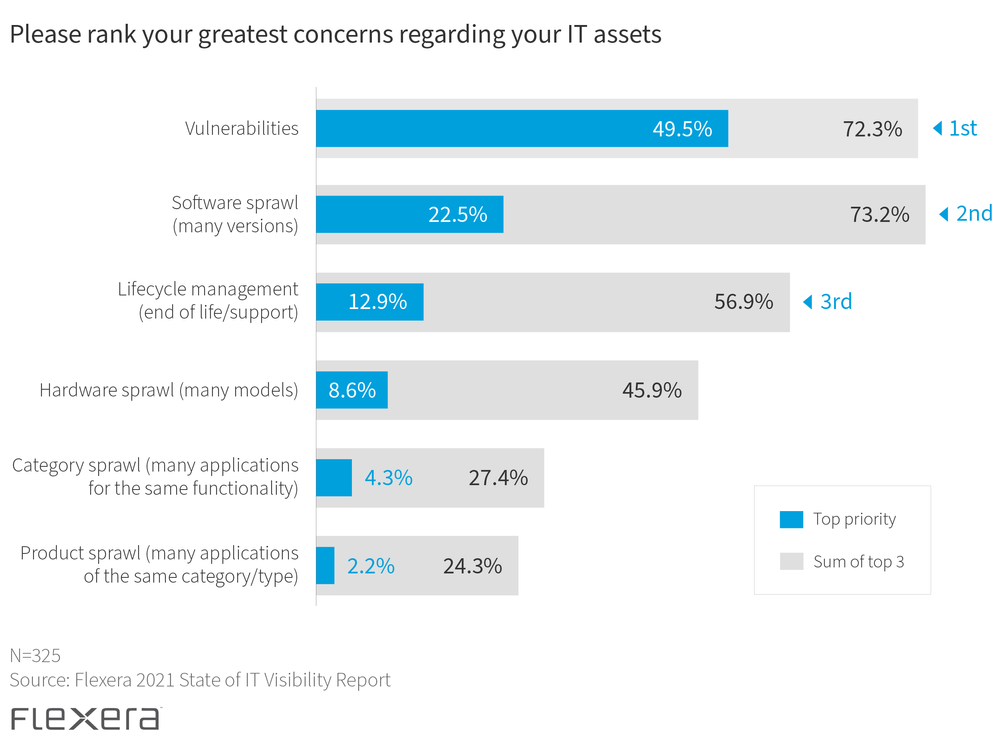
You already know that keeping IT assets secure is a top priority. And with several high-profile breaches in 2020 and 2021, it’s no surprise that the top concern from survey respondents for their IT assets is vulnerabilities. Software sprawl and lifecycle management round out the top three concerns.
These all tie together when thinking about how SAM, CMDB and other IT initiatives are becoming interdependent in an evolving hybrid IT estate. Knowing where you’re at risk—whether from a direct breach, software or hardware that’s become vulnerable due to obsolescence or an overabundance of application installations in your organization—helps you save time, money and other valuable resources that drive your business.
Don’t judge a book by its cover
A good place to start when assessing the vulnerability of your IT environment is with assets that are at end of life (EOL) or end of support (EOS). It’s correctly assumed that most of these are vulnerable, but some carry more risk than others.
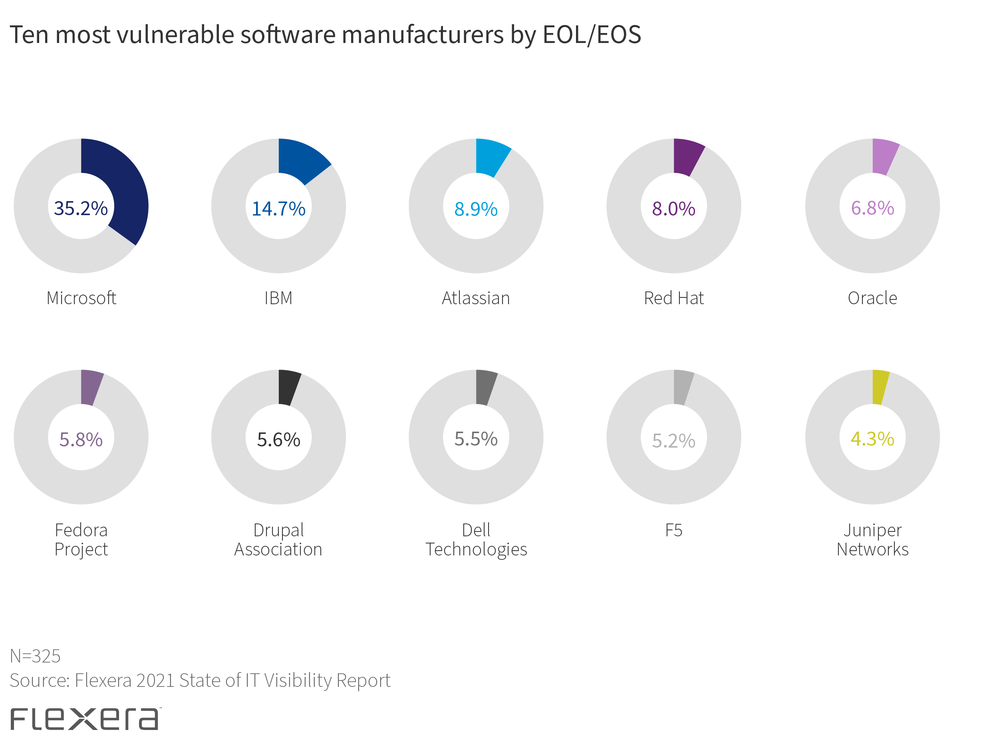
For example, the Flexera State of IT Visibility Report found that Micro Focus and VMware were among the top five vendors for most EOL/EOS software assets in 2021—but neither make the top ten when connecting unique vulnerabilities to EOL/EOS. These unique vulnerabilities are those associated with a minor version software release.
What’s the useful insight? Not all IT assets reaching EOL/EOS are created equal—and each manufacturer presents varying degrees of vulnerability that shouldn’t be assumed by the volume of products reaching EOL/EOS.
So where should you start?
Every IT environment is unique. Microsoft and IBM rank most vulnerable when it comes to EOL/EOS, but your organization may have a higher investment in other vendors. With this in mind, it’s important to understand not only which vendors are prevalent in each environment, but also which categories are most vulnerable and critical for your organization.
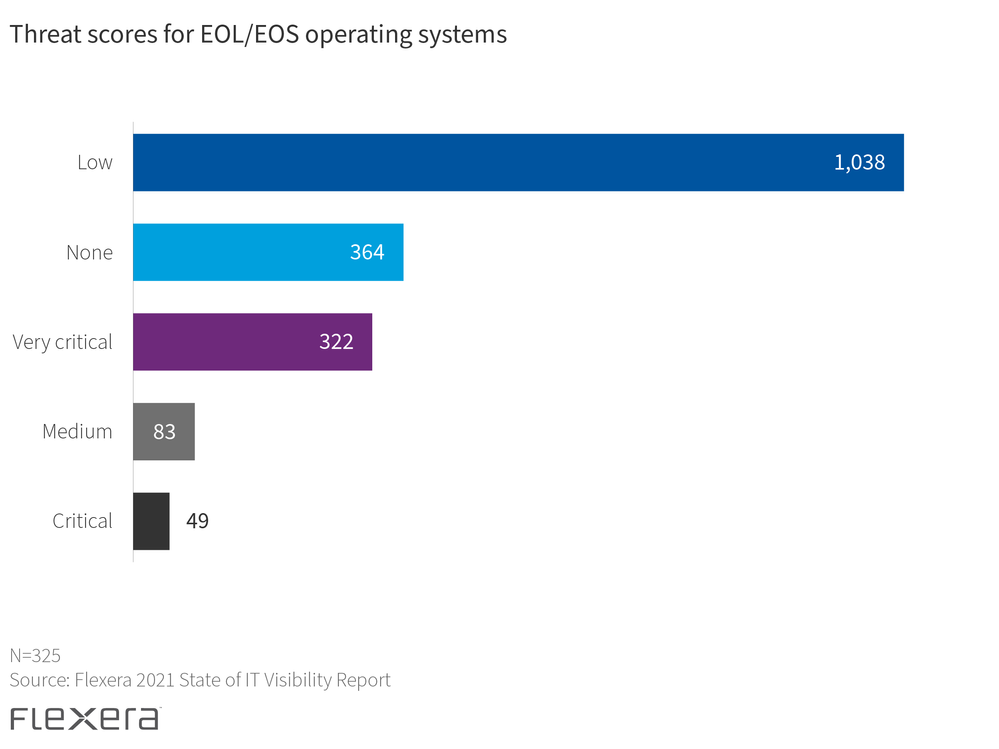
For example, the report ranks operating systems as the most vulnerable and second-most critical category of EOL/EOS software. Secunia Research has determined that an overwhelming number of vulnerabilities in operating systems are rated as low-level threat severity.
When most people hear something is a “low-level threat” they typically put it out of sight, out of mind—it’s automatically deemed a lower priority. Low-level threat severity, however, doesn’t mean that an attacker won’t breach your organization—there are 1,038 unique vulnerabilities through which they can gain access—but it does tell us that there is a lower likelihood of any one of these vulnerabilities being exploited.
This doesn’t mean that you’re out of the woods just yet. Because an overwhelming majority of EOL/EOS operating systems have this threat level, it’s still essential to focus on this area. Focusing only on high and very critical threat severity means you’ll miss out on the mass of vulnerabilities in need of remediation by overlooking these low-level threats—and don’t forget that they’re still actively being exploited in the wild. You can then dive further into which operating systems specifically carry the most vulnerabilities at that level and prioritize your remediation efforts by locating where those systems are installed within your organization.
For many more insights and complete survey results, download the Flexera 2021 State of IT Visibility Report.
You must be a registered user to add a comment. If you've already registered, sign in. Otherwise, register and sign in.