- Flexera Community
- :
- FlexNet Manager
- :
- FlexNet Manager Knowledge Base
- :
- Set up SSH key pair authentication on UNIX systems
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Mark as New
- Subscribe
- Mute
- Permalink
- Report Inappropriate Content
- Article History
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
In some environments, password authentication isn’t an option because credentials change often and are difficult and time-consuming for administrators to keep track of. Password authentication can also be a security concern when storing username and password combinations with root-level permissions on production devices in supplementary systems.
Flexera provides a solution for these situations by supporting SSH key pair authentication. This process relies on asymmetric cryptographic algorithms to generate a pair of separate keys. In key pair authentication, a public RSA key is stored on the device to be inventoried, and the matching private key is held in the password stored on the beacon. The SSH key pair authentication process uses remote execution or zero-footprint. Nothing is permanently installed on the target inventory device.
Some things to keep in mind when setting up key pair authentication:
- Don’t store the private key in a public location.
- Save the private key with a secure passphrase.
- Password Manager keeps a duplicate of the private key file in an encrypted form when using the default FlexNet Beacon vault. However, the original is still required if you need to reconfigure Password Manager.
Set up key pair authentication
- Generate key pairs in OpenSSH format (generated with ssh-keygen) or PuTTY format (generated with PuTTYgen.exe). The key generator creates two files, one public key to be stored on the device to be inventoried and one private key stored on the beacon.
For information on generating key pairs, see OpenSSH or PuTTY’s documentation.
- Below is an example of the command to generate key pairs with OpenSSL:
openssl genrsa -des3 -out private.pem 2048
openssl rsa -in private.pem -outform PEM -pubout -out public.pem
- The location to insert the public key varies depending on your SSH implementation. For example, for OpenSSH, the public key is entered as a one-line entry in the HOME_DIRECTORY/.ssh/authorized_keys file, where HOME_DIRECTORY is the home directory of the UNIX user listed in Password Manager for the credential. This user only needs basic user permissions on the device.
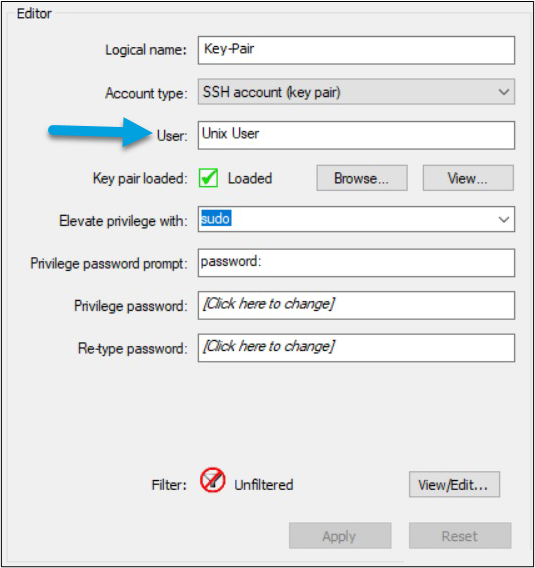
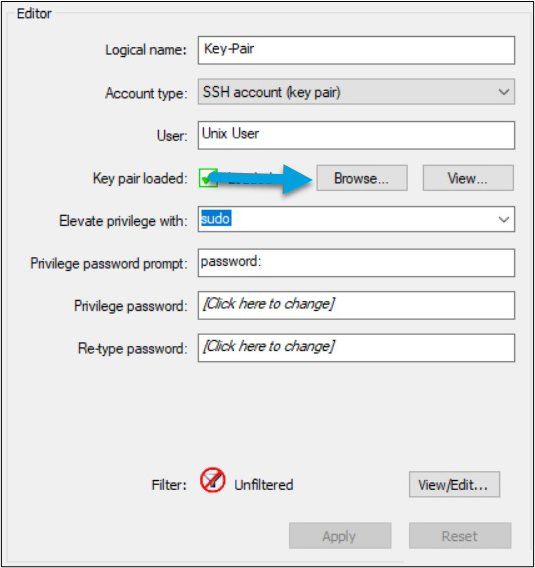
- The private key is imported into the credentials through the GUI by selecting Browse… and navigating to the private key file you generated earlier.
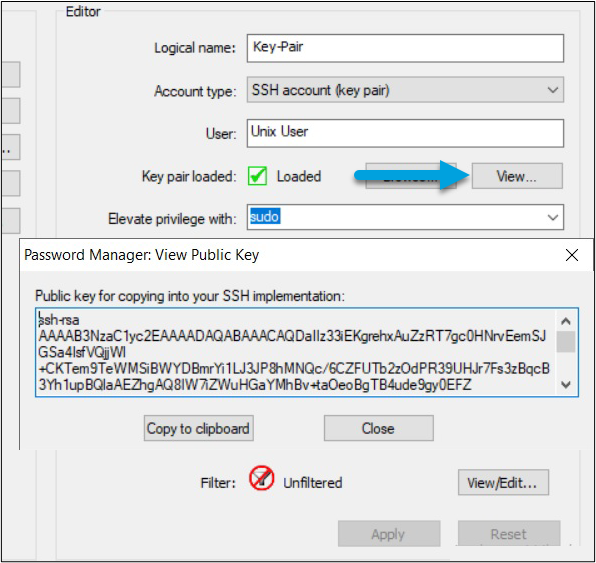
- Use the View... button to see the public key. Copy and paste it to the appropriate location on target devices.
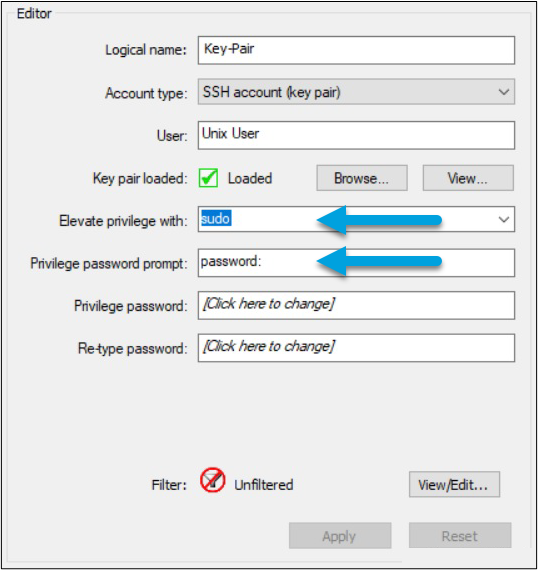
- Elevate privileges for the user so inventory will run successfully. You can do this in one of the two following ways.
- The SUDO command lets you impersonate the Root profile for a single command. To use this command:
- Specify “sudo” in the Elevate privilege with field of the Password Manager configuration screen.
- The SUDO command lets you impersonate the Root profile for a single command. To use this command:
IMPORTANT: Don’t edit the /etc/sudoers file directly. Always use Visudo. Otherwise, you may corrupt the file, leading to an unusable system.
-
- Enter the “sudo” password for that account. Specify any password prompt the UNIX operating system would use when prompting for the “sudo” password.
Or
- You can configure the UNIX account not to require a password to elevate privileges.
- Edit the /etc/sudoers file and add your username with the NOPASSWD option.
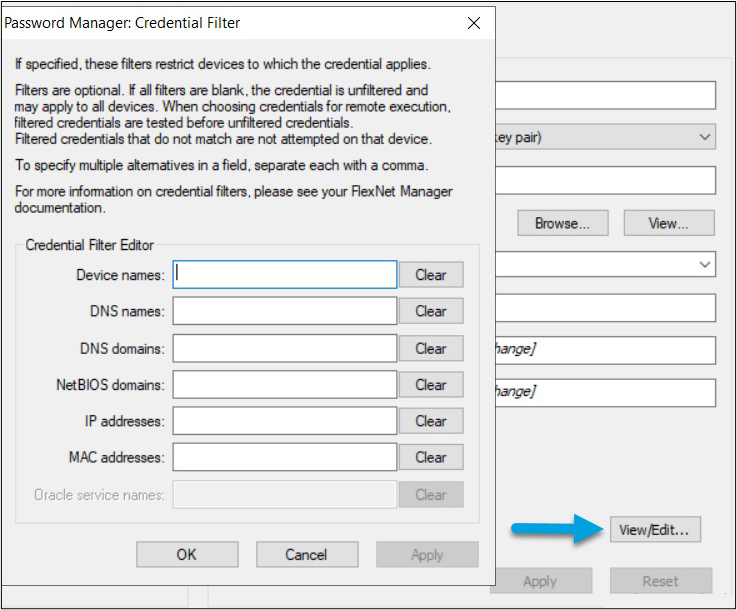
- To ensure you target specific devices, select View/Edit... to enable the filter and specify the IP addresses of your target devices.
-
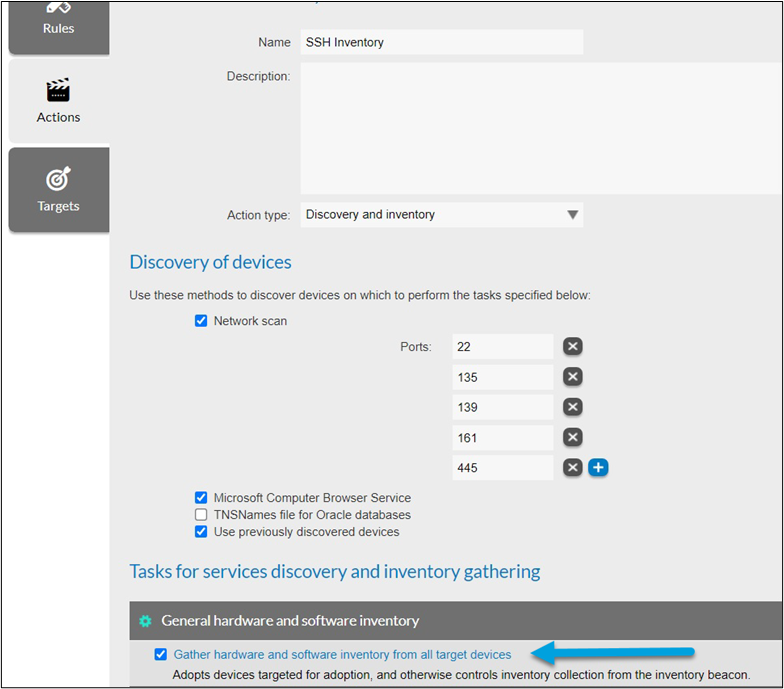
- In FlexNet Manager Suite, create a Discovery and Inventory rule (Discovery & Inventory > Discovery and Inventory Rules > Create a rule) with the target(s) specified.
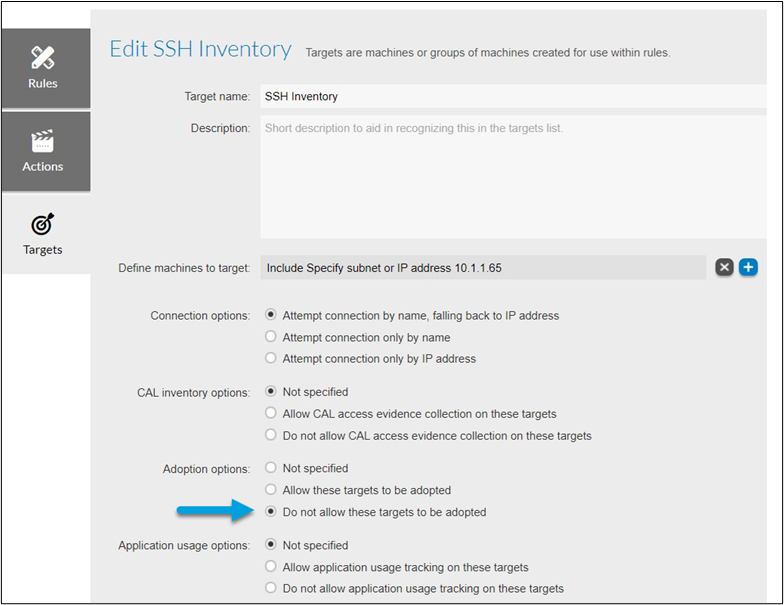
- In the target configuration, select Do not allow these targets to be adopted.
- In FlexNet Manager Suite, create a Discovery and Inventory rule (Discovery & Inventory > Discovery and Inventory Rules > Create a rule) with the target(s) specified.
on
Jun 25, 2020
10:57 AM
- edited on
Apr 21, 2023
09:08 AM
by
![]() HollyM
HollyM
![]()