- Flexera Community
- :
- Data Platform
- :
- Data Platform Knowledge Base
- :
- How to remediate the Slow HTTP Post vulnerability for Flexera User Console
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Threat:
The web application is possibly vulnerable to a "slow HTTP POST" Denial of Service (DoS) attack. This is an application-level DoS that consumes server resources by maintaining open connections for an extended period of time by slowly sending traffic to the server. If the server maintains too many connections open at once, then it may not be able to respond to new, legitimate connections. Unlike bandwidth-consumption DoS attacks, the "slow" attack does not require a large amount of traffic to be sent to the server – only that the client is able to maintain open connections for several minutes at a time.
The attack holds server connections open by sending properly crafted HTTP POST headers that contain a Content-Length header with a large value to inform the web server how much of data to expect. After the HTTP POST headers are fully sent, the HTTP POST message body is sent at slow speeds to prolong the completion of the connection and lock up server resources. By waiting for the complete request body, the server is helping clients with slow or intermittent connections to complete requests, but is also exposing itself to abuse.
Impact:
All other services remain intact but the web server itself becomes inaccessible.
Solution:
The security vulnerability can be fixed by updating the Limits settings for the web site. For some customers, they have some web applications installed on the same web site, Flexera cannot update the settings for the whole web site. Please follow the below instructions to limit the size of the acceptable request to User Console to remediate the Slow HTTP Post vulnerability.
Steps:
- Open IIS settings
- Browse to the web site where User Console is installed to, the default is "Default Web Site"
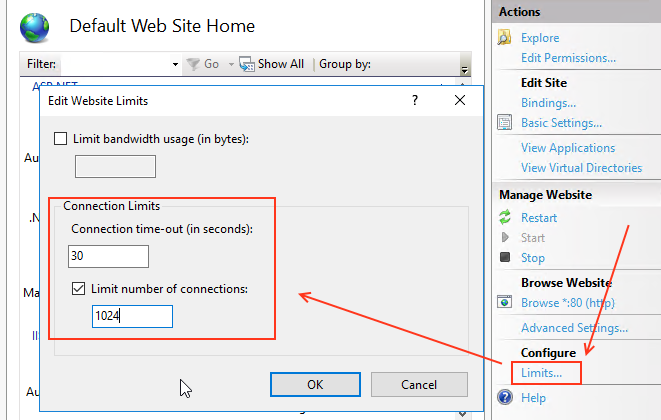
- On the Actions panel, click "Limits"
- Set Connection time-out to 30
- Check "Limit number of connections" and set the value to 1024.
- Click OK
- Run iisreset.exe to restart IIS service and take effect.
Dec 24, 2019 03:02 AM - edited Dec 24, 2019 03:03 AM