- Flexera Community
- :
- Data Platform
- :
- Data Platform Knowledge Base
- :
- Disable HTTP for Flexera Data Platform and User Console UI
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
- Article History
- Subscribe to RSS Feed
- Mark as New
- Mark as Read
- Subscribe
- Printer Friendly Page
- Report Inappropriate Content
Data sent over a non-HTTPS connection is unencrypted and vulnerable to network sniffing attacks that can expose sensitive or confidential information. This includes non-secure cookies and other potentially sensitive data contained in HTTP headers. Even if no sensitive data is transmitted, man-in-the-middle (MITM) attacks are possible over non-HTTPS connections. An attacker who exploits MITM can intercept and change the conversation between the client (like web browsers and mobile devices) and the server.
Disabling HTTP and enabling HTTPS only in your IIS settings can avoid security vulnerabilities. Flexera cannot directly modify your existing IIS host settings since you may have other applications deployed on the same IIS. Below are instructions to update your settings to disable HTTP and fix the insecure vulnerability.
Disable HTTP in Data Platform and User Console
IMPORTANT: If Data Platform and User Console aren’t on the same host, these steps must be completed in the Internet Information Services (IIS) Manager settings for both Data Platform and User Console.
- Open the IIS Manager settings for Data Platform or User Console.
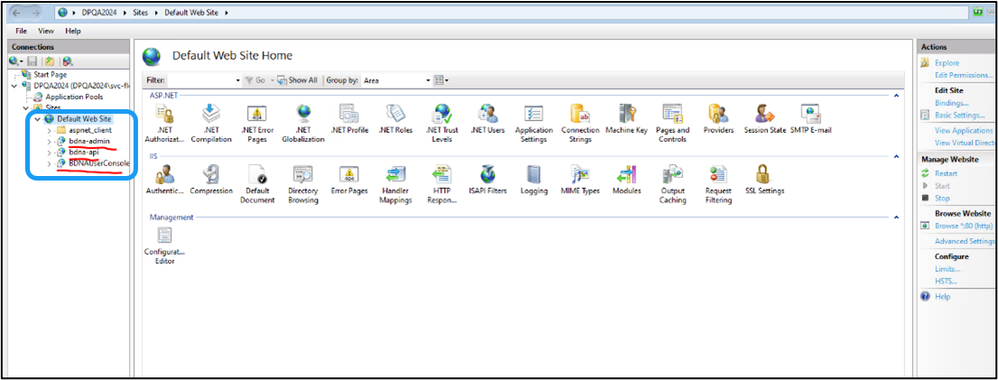
- Browse to the website where Data Platform or User Console is installed to. The default is "Default Web Site."
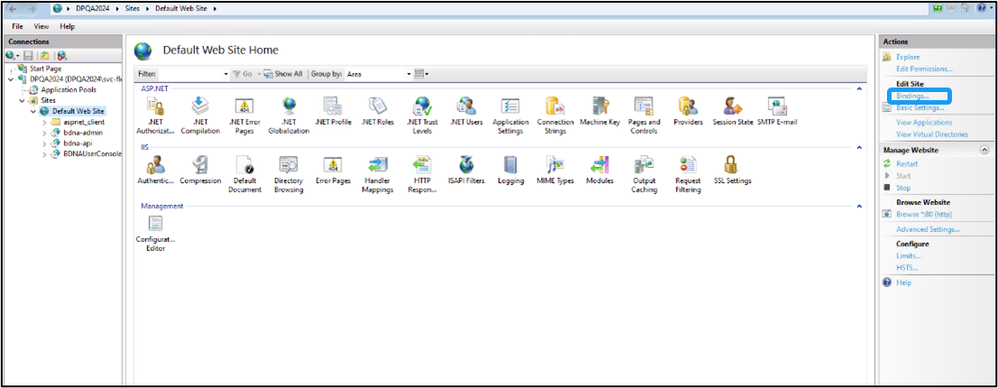
- Select the website, and open Bindings in the Action panel.
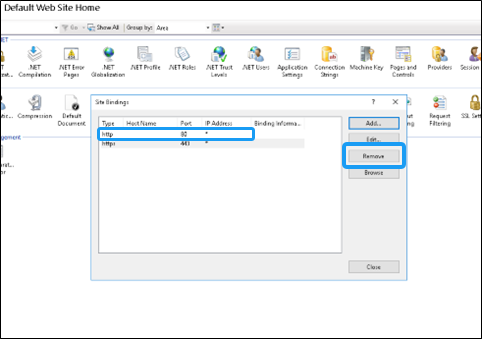
- Remove the HTTP bindings from the list and keep HTTPS only.
- Re-run the Data Platform Configure Wizard with the default settings.
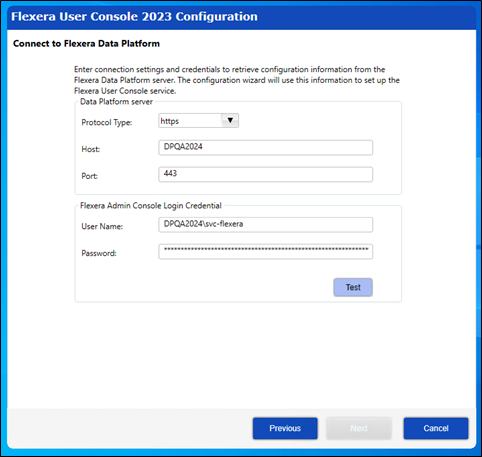
- Re-run the User Console Configuration Wizard to update the website protocol type from HTTP to HTTPS at the Connect to Flexera Data Platform step.
on
Dec 24, 2019
03:22 AM
- edited on
Mar 29, 2024
11:49 AM
by
![]() HollyM
HollyM
![]()